How our Compare the Market Quiz can help you find the best fit SD-WAN Vendors
- Answer 10 questions to find out which SD-WAN solution fits your business
- Learn why each solution is a match for your business
- Used by companies including CDC, Permira, Square Enix, British Legion and more
- Totally free to use without commitment
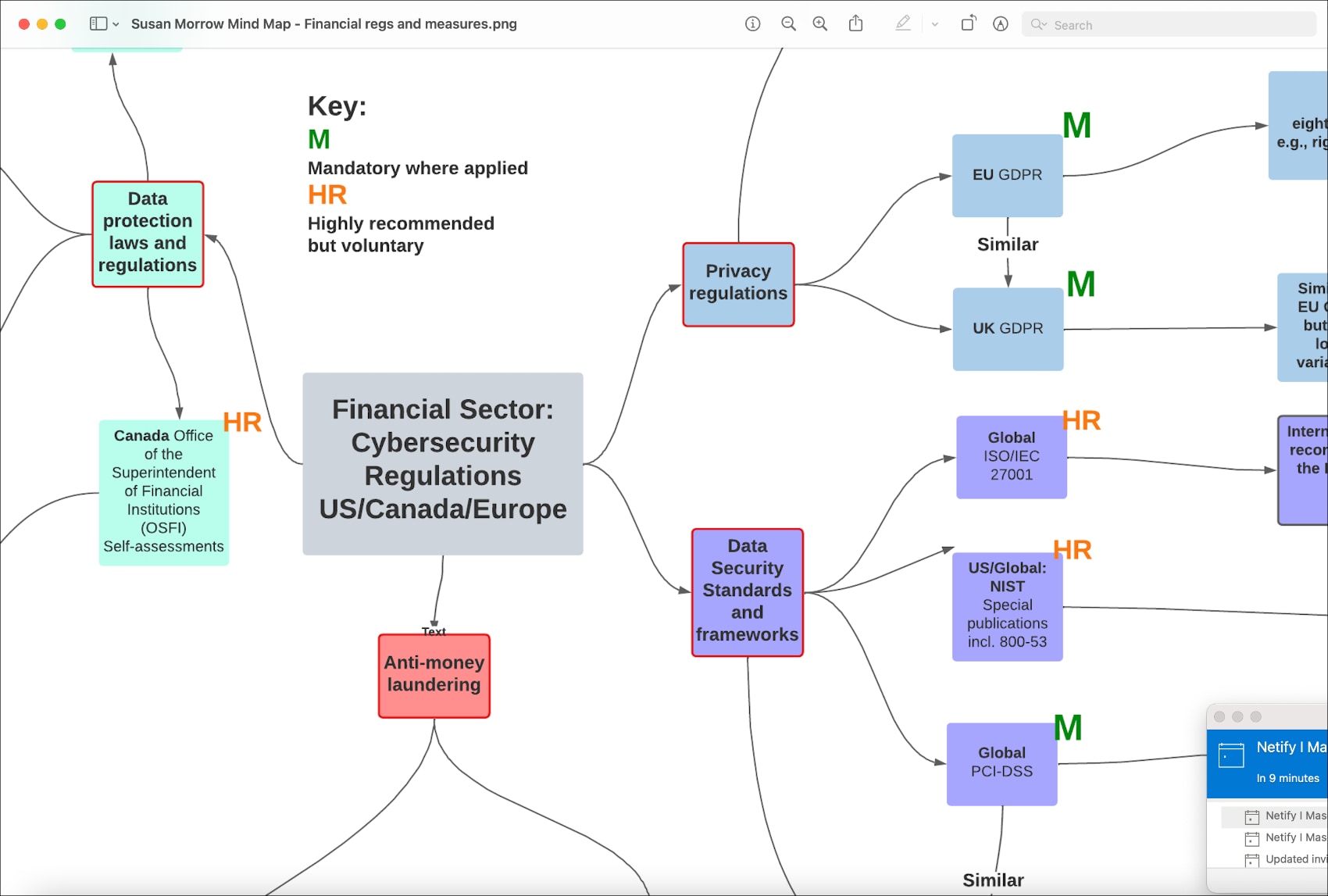
In the financial services industry, many aspects of data security and privacy involve risks—of cyberattacks, lost productivity and brand reputation, and many types of recovery costs, to mention a few.
Mitigating and avoiding these risks require IT security operations to run a gauntlet of challenges. Decisions include whether to update your financial services cybersecurity capabilities, when, and at what cost.
Here are some deployment and adoption considerations written for all levels of IT decision makers. We hope they will simplify your cybersecurity modernization efforts.

Cybersecurity Risk in the Financial Services Industry
Exactly what do we mean when we talk about cybersecurity risks? In this section, we’ll define risks that are most relevant to companies in the financial sector. Then, we’ll use our definition to ask some important questions.
What is Cybersecurity Risk?
Cybersecurity risk is one of many risks that financial services companies assume when they do business. But it’s helpful to remember that risk isn’t a thing or even an idea. It’s a number, a probability.
Cybersecurity risk is the probability of exposure, a loss of critical assets and sensitive information, or damage to a company’s reputation. It occurs when a cybersecurity threat (an attack or data breach) occurs anywhere within an organization’s computer system. In a larger sense, risk also refers to:
- The loss of confidentiality, integrity, or availability of information, data, or information control systems.
- Potentially adverse effects to an organization’s operations, assets, individuals, and partner organizations.
New types of threats appear constantly. Here are some of the newer items in the cyberthreat lineup:
- Island hopping, a hacking campaign, in which bad actors target an organization's more vulnerable third-party partners to get access to the company’s network.
- Brokerage account takeovers, a type of bank fraud, in which cybercriminals gain access to online accounts and use them to make purchases, withdraw money, or get information they can sell or use to enter other accounts.
- Timestamp manipulation, a type of fraud that can be caused by data injection attacks on blockchain smart contracts.
The cybersecurity environment of any company is complex and dynamic. In the financial services sector, with its daunting levels of risk and regulation, the damage that attacks can do is unusually high. Here’s the current lineup of the sector’s most damaging cybersecurity threats.
Biggest Cybersecurity Threats in Financial Services Sector
US and UK financial services regulators named cybersecurity risk the #1 risk to financial stability. The government’s concern focuses on financial companies and institutions. Current regulations expect that participants in the financial system will set up risk reduction and resilience initiatives that would reduce the frequency and damage done by cyberthreats.
The government cited three current or emerging cyberthreats, which include ransomware exploits, supply chain attacks, and DDOS attacks.
According to IBM and the Ponemon Institute, in 2021, the average cost of an enterprise data breach in the U.S. financial sector is $4.2 million. This section describes the threats that caused data breaches and other types of digital mayhem.
This year’s most dangerous threats for financial services companies
In January 2022, six types of cybersecurity threats pose the biggest risk to financial services organizations. They include:
- Phishing attacks
- Ransomware exploits
- Injection and scripting attacks
- DDoS attacks
- Supply chain attacks
- Bank drop accounts
Phishing attacks
It's estimated that more than 90 percent of all successful cyberattacks start with a phishing attack. Phishing is an umbrella term for several types of social engineering attacks. Cyber attackers use phishing to trick users into giving up user login information and gain access to network systems.
In email phishing, an email messages poses as legitimate communication sent to victims. Opening the infected link or attachment starts the installation of malware on the target computer system. Or it might load a fake web page that harvests user login credentials.
There are many ways to prevent phishing attacks.
- Start by educating your employees and conducting training sessions with mock phishing scenarios. We’ve all heard about “good security hygiene“ and employee security awareness” ad nauseum, but they’re essential to reducing cybersecurity risk.
- Develop—and consistently enforce—security policies that include but go beyond password strength and expiration dates. Privileged access management (PAM) is the main culprit here.
- Continue by deploying:
- An antivirus solution.
- A SPAM filter that detects viruses and blank senders.
- A web filter to block malicious websites.
Finally, maintain:
- All systems with the latest security patches and updates.
- All systems by scheduling signature updates.
- The antivirus status of all systems by monitoring them constantly.
- System security by encrypting all sensitive company information.
- System security by requiring encryption for employees who work remotely or telecommute.
Ransomware exploits
Diverse tactics. Ransomware attackers use different ways to extort victims into paying a ransom. The most popular has been publishing portions of seized sensitive data on criminal forums until a ransom is paid. These tactics are effective because the heavily regulated financial services industry assumes that all financial businesses have great cyberattack and data breach resilience. With ransomware attacks now evolving into data breach exploits, a successful attack could put target businesses in the crosshairs of regulators.
Business outcomes of successful ransomware attacks can be severe. They include the loss of funds, a damaged company reputation, sensitive information made public on the internet and Dark Web., and non-compliance penalties. If passed, the proposed Ransom Disclosure Act would require US businesses to disclose any ransomware payments within 48 hours of the transaction.
Preventing ransomware exploits. As in phishing, human nature lies at the core of a ransomware victim’s response. And because the human element is key, there’s no way to stop it altogether. However, you can:
- Review the effectiveness of your current protection systems and methods.
- Monitor systems for patterns of suspicious network behavior.
Data leaks, injection attacks and cross-site scripting
During 2021, three types of cyberattack were the most frequently observed in the financial sector.
“Data leaks” is polite language for stolen data that leaves its authorized IT environment. Cyber-attackers can steal or change poorly protected data and use the information in identity theft, credit card fraud, or other crimes.
Data leak damage is the same as data stolen under different circumstances—loss of funds and company reputation or compliance-related trouble with federal agencies.
Mitigate data leak risks by:
- Identifying sensitive data and applying appropriate security controls.
- Destroying data that’s not absolutely needed.
- Encrypting sensitive data at rest with strong encryption protocols, algorithms, and keys.
- Encrypting data in transit with secure protocols such as HTTPS, HSTS, and TLS.
- Disabling caching of sensitive data.
In data injection exploits, a remote attacker’s hostile data tricks the victim’s system to run malicious code or provide access to sensitive personal data without authorization.
Mitigate injection exploits by:
- Using positive (whitelist), server-side, input validation.
- Escaping special characters
- Using LIMIT and other SQL controls within queries.
Cross-site scripting involves cybercriminals injecting client-side scripts into web pages viewed by other users. Attackers can use this method to steal valuable information such as session cookies, which they can use to take over customer accounts on financial services sites. Mitigate cross-site scripting by installing a web application firewall (WAF).
DDoS attacks
In 2020, the financial services sector experienced more distributed denial-of-service (DDoS) attacks than any other type of attack, a 30-percent year-on-year increase.
In 2020-2021, multi-vector DDoS attacks (attacks using more than one method to overwhelm security teams) increased by 80 percent year-on-year.
During a DDoS attack, a victim's server is overwhelmed with fake connection requests, forcing target servers offline. DDoS exploits against financial services companies are popular because they offer attackers different ways to disrupt various targets, such as banking IT infrastructures, payment portals, and customer accounts. This approach enables DDoS attacks to penetrate deeply into the infrastructure of a wide range of companies.
You can reduce the risk of a distributed denial of service attack by:
- Developing a denial-of-service response plan.
- Securing your network infrastructure.
- Filtering routers at the edge of your network to spot and drop DDoS connections.
- Directing all traffic to an invalid address.
Supply chain cyberattacks
Although supply chain attacks target an organization’s less-secure vendors or supply chain partners, these exploits can occur at any organization from the financial sector to the oil industry or a government agency.
Some of the most memorable and damaging cyberattacks were supply chain exploits. In a 2013 attack, a Target store gave network access to a third-party vendor, a small Pennsylvania HVAC company. The company, which didn’t follow accepted security best practices, provided attackers with easy entry into Target’s network. The result: In December 2013, Target publicly confirmed that 40 million debit and credit card accounts were exposed in a data breach.
Later in January 2014, on January 10, 2014, Target disclosed that personal (non-financial) information such as names, addresses, and email addresses of about 70 million customers was also stolen.
In 2021 (which some cybersecurity pros call “The year of the supply chain hack,” supply chain attacks rose threefold. As the 2021 Software Supply Chain Security Report notes, successful attacks clustered in three types of threat:
- Open-source software vulnerabilities and poisoning
- Computer code QA
- Criminals exploiting the software supply chain process and supplier trust
The primary driver, however, was a fact well known by cybercrooks: most third-party vendors are not prepared for cyberattacks. Approximately 66 percent of compromised suppliers either did not know or failed to report that they were breached.
To defend against supply chain attacks, financial services companies should implement a Zero Trust architecture and set up and consistently enforce privileged access management (PAM) policies.
Bank drop scenarios
A drop refers to a physical space or a bank account that receives stolen goods or funds. Creating and using bank drops is a skill, which is part of an ecosystem of illegal services to launder funds and hide their location from authorities. Cybercriminals often store funds in fake bank accounts (drops) opened with stolen customer credentials. In bank drop scenarios:
- The mule (person handling stolen funds) receives fraudulent transfer accounts, which hackers have opened with stolen credentials. This is where the illicit funds reside, but fraudsters are reluctant to keep stolen money in place for any length of time. They prefer to transfer the goods out of the banking system as quickly as possible.
- When the mule receives the transfer, he or she cashes out the money and sends it to the fraudster via Western Union or another legitimate money transfer service.
Preventing bank drop scenarios altogether is unlikely. Engaging a service company to measure the overall health and resiliency of your IT infrastructure, however, is feasible. And it can help you identify potential entry points and vulnerabilities that can compromise IT operations.
What cyberthreat scenarios tell us
Going through cyberthreat descriptions and reading their prevention measures enable us to identify the assets, skills, and practices that help to reduce the risk of cyberattacks.
Establishing Cybersecurity Tech and Best Practices
When it’s time to buy or update cybersecurity software, tools, or services, it’s time to consider capabilities that help your IT or security team reduce cybersecurity risk. Here are some suggestions to guide your security protection efforts.
Deployment Considerations
What tools and technology can you deploy to reduce cybersecurity risk? When we think about securing computer systems, hardware and software products are the first things that come to mind.
Here are examples of cybersecurity products that can be used on-premises for ongoing protection or services, which you can engage to provide a snapshot of your system’s strengths and vulnerabilities. Some of the newer options haven’t developed a track record. Others are familiar elements of secure IT infrastructures everywhere.
- Hardware and software firewalls. Instead of asking which option to select, consider using each tool for the job it does best.
- Hardware firewalls offer network-wide protection from the external threats of incoming internet traffic. While they work, remember that these days, much of your company’s activity works at the edge of your IT infrastructure, which might occur beyond the network perimeter.
- Software firewalls are installed on individual computers. They inspect data more closely and can block malicious programs (malware) from sending data back into the Internet.
- Security essentials. Don’t forget to update these cybersecurity basics: the latest versions of antivirus solutions, SPAM filters, which detect blank senders and viruses, and web filters, which block malicious websites.
- Third-party risk management solutions. TPRM solutions use sophisticated software to assure that third-party vendor networks are secure. Solution software confirms cybersecurity improvements by assigning vendor networks with security ratings . And it tests compliance with standard security assessments. Advanced TPRM solutions also map security assessment responses to mandatory regulations associated with each vendor ‘s industry to uncover deficiencies that prevent compliance.
- Managed security detection and response services. Concerns about the inhouse cybersecurity skills gap drive the market for managed detection and response (MDR) services. MDR vendors provide a cost-effective selection of services that can improve enterprise cybersecurity defenses, minimize risk, and avoid an upfront cybersecurity investment.
- Attack surface monitoring solutions, which can help you detect and correct vulnerabilities that could bring about data breaches in your IT infrastructure. By looking beyond networks to entire IT infrastructures and vendor systems, these solutions help financial services businesses improve their security readiness and meet the strict cyber-resilience expectations built into financial services regulations.
- Data leak detection solutions. Data leaks make data breaches more likely and expose sensitive information, which could violate regulatory guidelines. A solution that can detect data leaks in an IT infrastructure and throughout the vendor network can prevent unnoticed regulatory violations and their associated penalties.
- Cybersecurity practices. Some new and some “classics,” are also part of a secure IT infrastructure.

Considering Security-related Practices
Updated cybersecurity-related technology is important, but your procedures, practices, and attitudes might need to change, too. The security risk reduction measures summarized in the previous sections provide a rich source of practices that support and strengthen your cybersecurity readiness.
Security practices. This section describes the security practices that can help your IT organization reduce the risk of successful cyberattacks.
Zero-trust architecture. This approach to cybersecurity assumes that all network activity is malicious until proven otherwise. Zero-trust security provides the framework for developing secure services anywhere, on any device that colleagues choose to use. Adding access management practices to zero-trust systems makes them more difficult for cybercriminals to break into sensitive data.
Privileged access management (PAM). In many companies, who gets what kind—and what level—of system privileges is a matter of status. That makes controlling access to systems privileges a delicate matter. It’s worth the effort, however because many cyberattacks are enabled by inappropriate account access.
Compliance-related practices. In a regulatory environment charitably described as “inconsistent,” keeping up with U.S. financial services regulations is a high-risk, high-stakes task. Each company’s compliance status depends on many factors. Compliance software is available. It’s used to continually monitor, track, and audit financial services processes to ensure they are coordinated with applicable industry, legal, and security requirements, consumer standards, and organizational policies.
Maintenance practices. Don’t forget the unglamorous, repetitive tasks of keeping IT infrastructures secure, jobs such as:
- Periodically reviewing the effectiveness of your current protection systems and methods.
- Monitoring all systems in your IT infrastructure for patterns of suspicious network behavior.
- Applying the latest security patches and updates on all systems.
- Scheduling sand running signature updates for all systems.
- Constantly monitoring all systems for viruses.
- Encrypting all sensitive company information, in transit or at rest.
- Requiring that systems of all employees who work remotely or telecommute are encrypted.
So that’s it, the rather long list of changes to consider when you build, update, and strengthen your cybersecurity readiness. Many of these suggestions might seem to be overkill. However, that’s what it takes to reduce the risk of cyber-attacks.
Conclusions
When you update your IT infrastructure’s cybersecurity capabilities, remember that upgrading hardware and software is only part of the story of reducing cybersecurity risk. Be sure to:
- Reassess your security-related practices and management methods.
- Judge whether your technology and practices strengthen your overall security readiness.
- Eliminate or update any part of your IT security system that doesn’t keep your infrastructure strong.