
In recent years businesses are increasingly transitioning from traditional WAN and MPLS network architectures to Software-Defined Wide Area Network (SD-WAN) solutions. This trend is primarily due to SD-WAN's ability to offer a significant improvement to network performance, scalability and security features, whilst also reducing operational overheads, with businesses of all scales often seeing significant Returns On Investment (ROI).
There are many key factors and technical considerations that you should consider when choosing an SD-WAN solution, with the weight that each factor bears being determined by your individual business operations, goals and network criteria. It’s important to select an SD-WAN solution that can integrate with your pre-existing legacy, proprietary and security systems. To assist with this process, in this article we've broken down each vendor's solutions and the depth of their capabilities.
Struggling to determine which features are important to your business? We've outlined how to compare SD-WAN solutions here. Alternatively, find out what each feature does with our glossary and learning centre. |
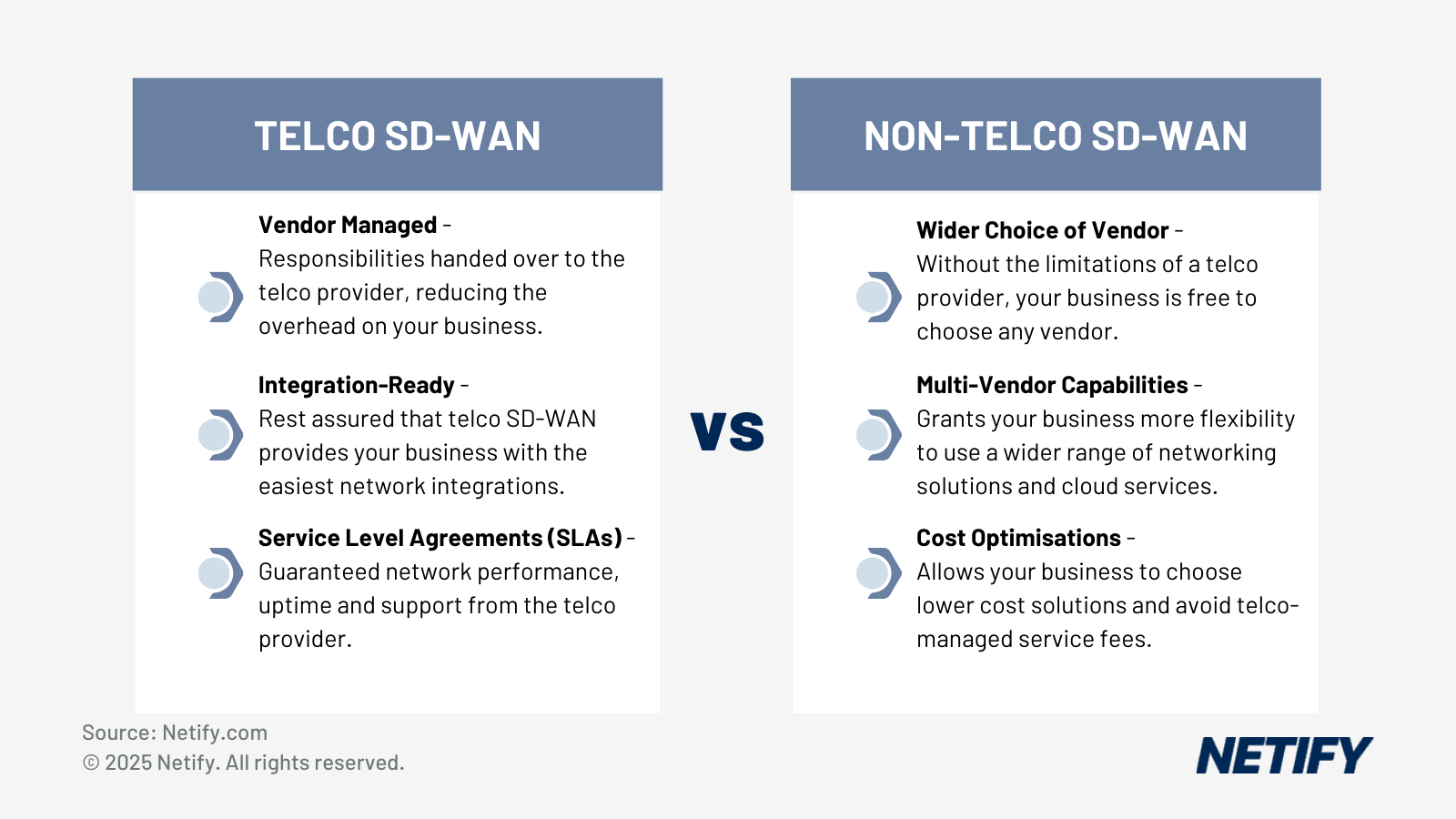
For those that don't have the internal expertise or dedicated resources to manage their network, one of the benefits of Telco providers that offer managed SD-WAN solutions is that the management responsibility is handed over to external experts. Integrating a new SD-WAN solution with existing infrastructure and IT systems can be complex and requires careful planning, therefore, through a managed model, you can rest assured that your business will be guided through the process.
| Vendor | SASE Network Security | Traffic QoS | Deployment | Managed Services | Reporting | Cost |
|---|---|---|---|---|---|---|
| Fortinet | Built-in Next-Generation Firewall (NGFW), Zero Trust Network Access (ZTNA), IPS and SSL inspection. | Offers a large range of QoS settings, actioned through dynamic prioritisation and traffic shaping. Also uses deep packet inspection (DPI), application-based policies and WAN optimisation to improve performance for SaaS, VoIP, and cloud applications. | On-premises, cloud-managed, and hybrid SD-WAN options. | Fortinet's secure SD-WAN is one of the most-used solutions by the Telco SD-WAN providers. | FortiAnalyzer provides AI-driven insights, historical trends and real-time visibility into network performance and security. | Reduces costs by leveraging low-cost broadband, consolidating networking and security functions and offering flexible licensing models. |
| Cisco | Offers built-in NGFW, IPS, DNS security, URL filtering, and Zero Trust Network Access (ZTNA). Integrates with Cisco Umbrella for cloud security and provides end-to-end encrypted traffic protection. | Implements QoS with dynamic prioritisation for applications. Ensures low latency for voice, video and cloud services using policy-based traffic management. | Supports on-premises, hybrid, and fully cloud-based SD-WAN deployments. | Includes professional and managed services for ongoing support. | vAnalytics provides AI-driven insights, historical performance trends and application-level visibility. | Reduces costs by leveraging broadband, consolidating security and networking functions, and offering flexible licensing models. Helps reduce reliance on expensive MPLS circuits. |
| Palo Alto Networks | Offers built-in Next-Generation Firewall (NGFW), Zero Trust Network Access (ZTNA) and threat protection, alongside deep packet inspection and segmentation. | Offers dynamic QoS settings, application-aware prioritisation and automated bandwidth allocation to maintain low latency for critical applications. Utilises policy-based routing and WAN optimisation to reduce latency and improve performance. | Available as a fully cloud-managed, hybrid, or on-premises solution. | N/A | AI-driven insights, real-time and historical analytics and visibility into application and network performance through the Prisma SD-WAN dashboard. | Reduces reliance on expensive MPLS circuits by leveraging broadband and cloud-based security. Consolidates networking and security functions to lower operational costs. |
| Versa Networks | Offers built-in Next-Generation Firewall (NGFW), Secure Web Gateway (SWG) and Zero Trust Network Access (ZTNA). | Provides granular QoS policies with dynamic traffic prioritisation and deep packet inspection (DPI) along with WAN optimisation to help reduce latency. | Supports on-premises, hybrid, and fully cloud-based SD-WAN deployments. | N/A | AI-driven analytics provide historical insights, real-time monitoring and application-level visibility to optimise network performance. | Reduces reliance on MPLS by leveraging broadband and LTE/5G. Integrated security eliminates the need for separate security systems, lowering costs. |
| HPE (Aruba EdgeConnect) | Includes built-in NGFW, IDS/IPS and cloud-based security integrations via Aruba ESP and SASE partnerships. Zero Trust capabilities ensure end-to-end security, with multiple VPNs on a single WAN for improved segmentation. | Offers QoS with dynamic traffic prioritisation and automated bandwidth allocation. Improves application performance through techniques like first-packet iQ, WAN optimisation, TCP acceleration and DPI. | Supports on-premises, hybrid and fully cloud-based SD-WAN. | N/A | Provides AI-driven insights, real-time monitoring and application-level visibility through Aruba Orchestrator. | Reduces costs by leveraging broadband connectivity, consolidating network functions and offering flexible licensing models. |
| Huawei | Integrates security features such as Next-Generation Firewall (NGFW) and supports end-to-end IPsec encryption. | Offers advanced QoS settings, including hierarchical QoS (HQoS) and intelligent traffic steering, ensuring optimal performance for key applications. | Offers on-premises, hybrid and fully cloud-based deployment options. | N/A | Provides detailed analytics and reporting capabilities, offering AI-driven insights and application-level visibility. | Reduces reliance on expensive MPLS circuits by leveraging cost-effective broadband and consolidating network functions, lowering operational expenses. |
| Juniper Networks | Built-in NGFW, Zero Trust security and threat intelligence via Security Director Cloud, supporting multiple VPNs on one WAN link for improved segmentation and security. | AI-driven dynamic QoS, with DPI and policy-based routing prioritising important applications and automatically adjusting bandwidth based on conditions. | Supports on-premises, hybrid, and cloud-based SD-WAN deployments. | N/A | Offers AI-driven insights, historical trend analysis and detailed application visibility via Mist AI and Marvis Virtual Network Assistant. | Reduces MPLS dependency by leveraging broadband, with AI-driven optimisation lowering operational expenses. |
| Ericsson (Cradlepoint) | Features built-in NGFW, Zero Trust Network Access (ZTNA) and threat intelligence integrations, with support for multiple VPNs per WAN for improved segmentation. | Offers QoS settings with dynamic traffic prioritisation, WAN optimisation, DPI and AI-driven policies for cloud-based and latency-sensitive applications. | Available as on-premises, hybrid and cloud-native deployments. | N/A | AI-driven analytics provide deep insights into network performance and bandwidth usage, enabling predictive maintenance. | Reduces costs by leveraging broadband, consolidating network functions and offering flexible licensing models. |
| Peplink | Offers built-in NGFW, intrusion prevention and content filtering. Supports ZTNA and integrates with third-party security platforms, while also supporting multiple VPNs over a single WAN connection. | Provides application-based QoS with dynamic bandwidth control, WAN smoothing and DPI for key application performance. | Offers on-premises, cloud-based and hybrid SD-WAN deployments. | N/A | InControl 2 provides real-time analytics, historical trend reports and AI-driven insights for proactive network management. | Reduces reliance on expensive MPLS by leveraging low-cost broadband and cellular connectivity, while SpeedFusion optimises bandwidth usage. |
| Barracuda Networks | Provides security features such as NGFW capabilities, ZTNA and compliance tools. | Barracuda offers limited QoS settings, including dynamic adjustments and protocol prioritisation, achieved with WAN optimisation, DPI and application-specific policies to reduce latency and increase throughput. | Barracuda offers on-premises, hybrid and fully cloud-based SD-WAN options. | N/A | Barracuda provides analytics tools and reporting capabilities, offering AI-driven insights, historical trends and detailed application-level visibility. | Leverages low-cost broadband connections and consolidates network functions, reducing reliance on expensive MPLS circuits. |
| Aryaka | Includes built-in security such as an NGFW, Secure Web Gateway (SWG) and ZTNA, while also supporting multiple VPNs per WAN connection for data segregation. | Provides QoS with dynamic bandwidth allocation and prioritisation, with WAN optimisation, application acceleration and DPI. | Available as fully managed cloud-based SD-WAN, hybrid or on-premises solutions. | Delivers SD-WAN as a service over a private network, eliminating the need for customers to build their own solutions. | Offers AI-driven network insights, historical performance data and detailed application-level visibility. | Reduces reliance on MPLS by leveraging low-cost broadband, while Aryaka’s private backbone ensures performance. Provides predictable costs. |
| Cato Networks | Built-in security includes NGFW, SWG, ZTNA and Advanced Threat Protection (ATP), fully converged into the SD-WAN fabric with support for multiple VPNs on a single WAN. | Uses a range of QoS techniques, such as dynamic bandwidth allocation, application-aware routing, WAN optimisation and DPI, benefiting cloud and SaaS applications. | Offers cloud-native, hybrid and on-premises deployment models. | Converges SD-WAN and security into a global, cloud-native platform as a single-vendor SASE solution. | Provides AI-driven analytics with real-time network insights, historical trend analysis and detailed application-level visibility. | Reduces reliance on expensive MPLS by leveraging low-cost broadband and consolidating security and networking functions into a single platform. |
| Ecessa | Integrates basic firewall capabilities and supports third-party security tools. While not NGFW-native, it complements existing security frameworks and can be used alongside other solutions to meet compliance needs. | Offers configurable QoS settings to prioritise applications via DPI and policy-based routing, steering traffic by application type. | Supports on-premises and hybrid models. | N/A | EdgeView includes performance monitoring, historical trend analysis and real-time alerts. | Reduces costs by leveraging broadband and eliminating MPLS dependency. |
| Adaptiv Networks | Built-in firewall and secure VPN tunnels. Adaptiv doesn’t offer a full NGFW, but integrates with third-party security tools and follows security best practices. Supports multiple VPNs on a single WAN for segmentation. | Enables traffic prioritisation for critical applications, with dynamic QoS adjustments based on real-time conditions to maintain performance. Supports traffic shaping and DPI. | Available as cloud-managed or hybrid deployment. | N/A | Provides a cloud-based analytics dashboard with real-time and historical data, enabling bandwidth planning and traffic optimisation. | Leverages low-cost broadband and eliminates the need for costly MPLS in many cases. Simple licensing reduces budgeting complexity. |
| Extreme Networks | Built-in security includes stateful firewalling, IDS/IPS, and integration with third-party security platforms. Offers Zero Trust support and centralised policy enforcement, with multiple VPNs for multi-tenant use cases. | Offers granular QoS settings, WAN optimisation, DPI and application-specific traffic shaping to prioritise business-critical applications. | Available on-premises, cloud-based or hybrid deployments. | N/A | Provides detailed application-level analytics and network health reports. AI-powered insights help identify issues proactively and optimise performance. | Reduces dependency on MPLS through broadband-first designs and by consolidating network functions. |
| FatPipe Networks | Includes a built-in firewall and supports integration with third-party security tools. Not a full NGFW, but offers encryption, DDoS protection and compliance support for regulated industries, and supports multiple encrypted tunnels. | Offers granular QoS controls with real-time adjustments, using DPI, compression, WAN optimisation and packet duplication. | Available in on-premises, hybrid and cloud-hosted deployments. | N/A | Includes performance dashboards and historical analytics for bandwidth, traffic patterns and application usage. | Reduces MPLS dependency by using broadband links while maintaining performance and uptime. Consolidates multiple functions to reduce CAPEX and OPEX. |
| Forcepoint | SD-WAN is integrated with Forcepoint’s NGFW and built-in threat protection, including IPS, SSL inspection, and ZTNA. Multiple VPNs can run over a single WAN for improved segmentation. | Offers granular QoS controls to prioritise latency-sensitive applications via DPI and custom application policies. | Available as physical, virtual, cloud-hosted or hybrid deployments. | N/A | Built-in analytics provide application-level visibility, usage trends and real-time alerts. | Reduces costs by utilising cheaper broadband links over MPLS, consolidating firewall and SD-WAN functions, and offering simplified licensing. |
| Mushroom Networks | Includes firewall capabilities and integrates with third-party security platforms. Supports multiple VPNs per WAN link to segment traffic securely. | Offers traffic shaping, flow control, error correction and adaptive routing for prioritising essential applications. | Available as on-premises, hybrid or fully cloud-managed. | Enables channel partners and service providers to build custom SD-WANs via its autopilot service, offering application-centric overlay tunnels and VNFs. | Provides real-time and historical traffic analytics. Detailed reports include application usage, link health and bandwidth consumption. | Reduces dependency on MPLS by leveraging multiple lower-cost broadband links. Consolidated functions lower total infrastructure costs. |
| Nokia (Nuage Networks) | Includes built-in stateful firewall, micro-segmentation, and integration with third-party security solutions. Supports Zero Trust models with role-based access and policy enforcement, plus multiple VPNs per WAN link. | Enables granular QoS settings with dynamic adjustments based on application and network conditions. Uses DPI and application-aware policies to improve performance. | Supports on-premises, hybrid and fully cloud-hosted SD-WAN deployments. | With 70 certified managed service providers and 700+ enterprise customers, Nuage Networks have a long history of providing managed SD-WAN services for varied business requirements. | Provides detailed analytics through the VNS portal, including real-time and historical views, application visibility and link utilisation metrics. | Reduces costs by enabling the use of lower-cost broadband and consolidating multiple network functions. |
| Oracle | Integrates with third-party security platforms but does not include native NGFW or ZTNA, instead focusing on segmentation, encryption and traffic isolation. | Offers granular QoS settings, with DPI and application-specific policies to optimise traffic routing. | Supports on-premises, cloud-hosted and hybrid deployment models. | Ideal for enterprises already using Oracle Cloud, providing real-time application support across dispersed sites and multiple WAN links. | Provides in-depth analytics, including real-time and historical performance metrics. | Customers benefit from fewer hardware requirements and reduced transport costs by replacing costly MPLS with cheaper broadband links. |
| Riverbed Technology | Includes a built-in firewall, segmentation, and integration with third-party security tools. | Leverages WAN optimisation, DPI and application-aware policies to enable granular QoS controls prioritising latency-sensitive traffic. | Supports on-premises, hybrid and cloud-based deployments. | Transitioned from WAN optimisation (Steelhead) to SD-WAN (SteelConnect), leveraging a global backbone and application acceleration to serve large enterprises. | Built-in analytics offer traffic visibility, usage trends and application insights. | Enables use of lower-cost broadband links and reduces dependency on MPLS. Consolidated management tools lower operational expenses. |
| SonicWall | SonicWall offers built-in integrations of their NGFW, threat prevention and Zero Trust features, with support for multiple VPNs per WAN interface. | Offers granular QoS controls and application-layer intelligence to optimise throughput and reduce latency, prioritising essential application traffic. | Available in on-premises, cloud-managed and hybrid models. | Integrates SD-WAN into firewall appliances, targeting SMBs via TZ series devices and the Capture Cloud Platform for unified security and networking. | NSM provides detailed traffic analytics, application-level visibility and historical reporting. | Reduces dependency on MPLS by leveraging broadband and LTE links. Consolidates security and networking in one appliance, lowering total cost of ownership (TCO). |
| Sophos | Includes integrated NGFW, IPS, anti-malware and ZTNA, while supporting multiple VPNs over a single WAN link. | Offers application-aware traffic shaping, DPI and policy-based routing to optimise performance for SaaS and cloud applications. | Available as cloud-managed, hybrid or on-premises solutions. | Designed for SMB and mid-market customers prioritising security, with gradually implemented SASE services via partnerships (e.g. Zscaler for SSE). | Offers real-time analytics, application-level visibility, and historical reporting via Sophos Central. | Leverages low-cost broadband links and eliminates the need for multiple point solutions by combining SD-WAN with embedded security, reducing total cost of ownership. |
| Turnium | Includes an integrated firewall, traffic segmentation and secure tunnelling. Not positioned as a full security stack, but allows integration with third-party security solutions and supports multiple encrypted tunnels per WAN link. | Enables traffic shaping, packet-based link aggregation and loss recovery to ensure QoS. | Available as on-premises, virtual and cloud-hosted solutions. | Turnium provides the networking element while partners handle security, management, orchestration and other managed services. | Provides real-time traffic monitoring and usage reports, with visibility into application behavior, link performance and historical trends. | Reduces costs by using low-cost broadband and virtualising WAN functions. |
| VMware VeloCloud | Integrates with VMware SASE for NGFW, ZTNA and secure web gateway, delivered via the cloud to reduce local complexity. Supports multiple VPNs per WAN for improved segmentation and resilience. | Offers application-aware QoS, with DPI, app-specific policies and real-time prioritisation for granular control across branches and cloud services. | Supports on-premises, hybrid and cloud-based models. | Operates a global network of 3,700+ gateways across 200+ PoPs, enabling a cloud-native architecture that also supports integration of third-party security services and multi-cloud connectivity. | Built-in analytics offer real-time and historical visibility, application-level insights and bandwidth usage metrics. | Reduces reliance on MPLS by prioritising cheaper broadband connectivity. |
| WatchGuard Technologies | Includes a built-in NGFW, intrusion prevention, web filtering and antivirus. Supports multiple VPNs over a single WAN for improved segmentation. | Offers configurable QoS settings to prioritise critical applications, with rules by application, port or protocol. Utilises traffic shaping and application-layer visibility via DPI. | Supports on-premises and hybrid models (cloud-based control available, though full cloud-native SD-WAN deployment is limited). | Embedded SD-WAN in Firebox appliances combines security and SD-WAN in one platform, providing cost advantages for SMBs. Additional security features can be added via the Total Security Suite. | WatchGuard Cloud includes reporting tools with application-level insights and bandwidth usage metrics. | Enables cost savings by reducing reliance on MPLS and combining network and security functions into a single appliance, using broadband as primary transport. |
| Zyxel | Integrated with Zyxel’s Unified Security Gateway, including firewall, content filtering, and intrusion detection. Supports multiple IPsec VPNs on a single WAN interface for security and segmentation. | QoS policies centrally defined through Nebula and enforced via DPI. | Offers on-premises, hybrid and cloud-managed models. | Targets SMBs and MSPs, aiming to make SD-WAN accessible to all. Allows MSPs to deploy endpoints across client sites to create high-availability network clouds. | Nebula provides real-time and historical analytics on bandwidth usage, traffic patterns and application performance. | Prioritises use of broadband and LTE, reducing reliance on costly MPLS circuits. |
| Bigleaf Networks | N/A (Customers are expected to integrate their own firewalls or third-party security tools.) | Offers application-aware QoS that prioritises traffic automatically via failover, session re-routing and real-time link assessments. | Offers cloud-based models only. | Ideal for SMBs needing reliable internet for cloud apps without extensive IT resources. Operates an extensive backbone (11 PoPs) and peers with 150+ cloud, content, and carrier networks. | Provides live and historical reporting on circuit performance, application behavior and outage history. | Enables use of affordable broadband links instead of MPLS. |
| Check Point | Integrates a full NGFW, IPS, antivirus, anti-bot, URL filtering and Zero Trust controls. | Provides granular QoS with dynamic bandwidth allocation, application-layer awareness, DPI and traffic shaping. | Supports on-premises, hybrid or cloud-delivered SD-WAN. | Released Quantum SD-WAN in 2023 as a ground-up solution to tightly integrate with Check Point’s security. Positioned as part of a complete SASE offering when combined with Harmony Connect (SSE). | Provides real-time and historical analytics through the Infinity Portal. | Consolidates network and security into one platform and enables use of affordable broadband while reducing MPLS dependency. |
| Cloudflare | Provides built-in Zero Trust security with secure web gateway, next-gen firewall and zero trust network architecture. | Offers configurable QoS policies, enabling prioritisation of latency-sensitive apps via DPI and traffic shaping. | Fully cloud-delivered model, with hybrid support via existing infrastructure. | Offers Magic WAN, a cloud-based SD-WAN alternative built on Cloudflare’s global edge network, minimising on-prem hardware by using its private backbone. Part of the Cloudflare One SASE platform. | Offers real-time and historical analytics with application-level insights. | Replaces MPLS with cost-effective broadband by leveraging Cloudflare’s global network. |
| FlexiWAN | Offers integrated firewall capabilities and supports third-party security services. Users can choose their preferred security stack, aligning with flexiWAN’s modular open-source design. | Allows application-based prioritisation and dynamic traffic shaping. Provides performance monitoring for specific applications. | Supports cloud-managed, hybrid and on-premises deployments. | The industry’s first open-source SD-WAN solution, removing vendor lock-in and enabling dynamic third-party applications and SASE integrations. Offers a hardware-agnostic, cost-effective model that scales from small devices to cloud platforms. | Offers real-time dashboards and historical data on bandwidth, application usage and network health. | Reduces costs by using low-cost internet and consolidating network functions. Open-source licensing avoids vendor lock-in and allows budget-friendly scaling. |
| Netskope | Netskope’s SD-WAN includes embedded NGFW, Secure Web Gateway (SWG), Cloud Access Security Broker (CASB), ZTNA and supports multiple VPN overlays per WAN link for improved segmentation. | Provides dynamic adjustments via DPI and application-based policies to deliver QoS. | Supports cloud-native, hybrid and on-premises deployments. | Introduced as part of Netskope’s Borderless SD-WAN after acquiring Infiot in 2022. Delivered via the NewEdge network (71+ regions) as a single-vendor SASE solution that bridges networking and security without trade-offs. | Offers analytics with AI-powered insights, historical trend data and detailed traffic reports. | Reduces reliance on MPLS by using broadband and cellular links. |
| Zscaler | Fully integrates ZTNA, cloud firewall and advanced threat protection, with support for multiple VPNs over a single WAN. | Enables granular QoS with dynamic adjustment based on real-time application requirements, using application-aware routing and cloud proximity for SaaS and web performance. | Cloud-delivered by design, with hybrid support via integration with on-premises infrastructure and SD-WAN partners. | Transitioned from a security partner model to a full SASE offering, now leading the SASE market with a 20% revenue share. Zscaler’s Zero Trust Branch Connectivity appliance (introduced 2023) integrates SD-WAN functionality into its cloud platform. | Includes AI-driven analytics for real-time insights and historical trends. | Utilises broadband and mobile links (LTE/5G) to reduce MPLS dependency. |
| AT&T | AT&T's SD-WAN solutions incorporate security features such as NGFWs, SASE frameworks, and ZTNA. | Offers SLAs for network availability, packet loss, congestion, jitter and latency. | On-premises, hybrid and fully cloud-based SD-WAN options. | Offers a range of managed SD-WAN services, partnering with multiple vendors (Cisco Catalyst, VMware VeloCloud, HPE Aruba EdgeConnect, FatPipe, etc.). Provides fully managed and co-managed options, as well as a self-service SD-WAN for SMBs. | N/A | Optimises transport and operational costs by reducing MPLS reliance, with centralised management, zero-touch deployment and improved application performance. |
| BT | BT's SD-WAN solutions incorporate advanced security measures such as NGFW, ZTNA, SWG and CASB. | BT offers a 100% target availability SLA on its BTnet Leased Line service, with compensation if unmet. | On-premises, hybrid and fully cloud-based SD-WAN options. | BT partners with Cisco Catalyst, Cisco Meraki, Nuage Networks, Palo Alto Prisma, Fortinet, and VMware VeloCloud for its managed SD-WAN services. It has launched global managed offerings (e.g. with Cisco for performance-focused solutions and Fortinet for security-centric SD-WAN). | N/A | Optimises transport and operational costs through reduced MPLS reliance, centralised management, zero-touch deployment and improved application performance. |
| Lumen (CenturyLink) | Lumen's SD-WAN solutions incorporate advanced security measures such as stateful firewalls, IDS/IPS, URL filtering and content filtering. | Offers SLAs for frame delivery, frame delay, and delay variation (99.999% availability with specified loss and jitter thresholds). | On-premises, hybrid and fully cloud-based options. | Delivers fully managed SD-WAN solutions, partnering with Versa, VMware VeloCloud, Cisco Meraki, Cisco Catalyst and Fortinet. Also offers co-managed solutions with improved network visibility and control. Notably, Lumen provides a Sovereign Secure SASE solution with Versa for highly regulated industries. | N/A | Optimises transport and operational costs by reducing MPLS reliance, centralised management, zero-touch deployment and improved application performance. |
| China Mobile (CMI) | China Mobile's SD-WAN solutions offer traffic encryption. | Provides a 99.95% availability SLA (CGW to CGW), with latency guarantees available on request. | On-premises, hybrid and fully cloud-based SD-WAN solutions. | Delivers SD-WAN services via its subsidiary CMI for cross-border connectivity. Integrates with a global backbone for improved performance and connectivity, and offers bilingual support and direct China-to-international connectivity beneficial for businesses operating in China. | N/A | By utilising broadband, internet and LTE, China Mobile's SD-WAN reduces reliance on traditional MPLS circuits, yielding cost efficiencies. |
| China Telecom | Offers security integrations such as NGFW, UTM, IDS, and IPS. | Provides SLAs including uptime guarantees and latency thresholds. | On-premises, hybrid, and fully cloud-based SD-WAN options. | Provides managed and self-managed SD-WAN solutions through a partnership with Versa Networks. Its platform is designed to comply with Chinese regulations while integrating mainstream SaaS applications, enabling secure, cross-border connectivity. | N/A | Leverages cost-effective broadband and consolidates network functions, reducing reliance on MPLS circuits and lowering operational expenses. |
| China Unicom | China Unicom's SD-WAN solutions offer end-to-end encrypted IPsec VPN tunnels. | N/A | On-premises, hybrid, and fully cloud-based SD-WAN solutions. | Delivers managed SD-WAN focused on cross-border networking and hybrid cloud integration. Tailored for enterprises needing high-performance links between China and other regions, leveraging partnerships with Cisco, Huawei and ngena. | N/A | By using a mix of MPLS, VPN and LTE, China Unicom's SD-WAN enables more efficient bandwidth use, reducing MPLS reliance. |
| Comcast Business | Comcast Business' SD-WAN solutions integrate security features such as NGFW, SWG and UTM. | Offers a 99.99% network uptime SLA via its extensive IP backbone. | On-premises, hybrid, and fully cloud-based SD-WAN options. | Offers fully managed SD-WAN through partnerships with Versa Networks, Fortinet, HPE Aruba EdgeConnect, Cisco Catalyst and Cisco Meraki. Its cloud-based ActiveCore platform provides unified management and automation capabilities for these solutions. | N/A | Leverages cost-effective broadband options, reducing reliance on expensive MPLS circuits. |
| Deutsche Telekom | Deutsche Telekom offers integrations for SASE frameworks, including SWG and CASB. | Provides service and performance SLAs. | On-premises, hybrid and fully cloud-based SD-WAN options. | Offers managed SD-WAN under the Telekom SD-X platform, which acts as a marketplace for modular, multivendor service components. Customers can select and combine networking and security services (internet, security, WiFi, VPN, etc.) in a unified solution. | N/A | By leveraging low-cost broadband and flexible licensing models, Deutsche Telekom’s SD-WAN reduces MPLS reliance and operational expenses. |
| GTT Communications | GTT's SD-WAN integrates security measures such as unified firewall capabilities. | Provides 99.999% availability SLAs with ≤0.1% packet loss and ≤2ms jitter. | On-premises, hybrid and fully cloud-based SD-WAN solutions. | Partners with Fortinet, HPE Aruba EdgeConnect and VMware VeloCloud for managed SD-WAN services. With a global backbone of 450+ PoPs, GTT delivers secure, scalable and cloud-ready solutions tailored for distributed enterprises. | N/A | GTT's SD-WAN uses broadband, wireless and MPLS in combination to optimise connectivity and scalability, reducing reliance on MPLS circuits. |
| Hughes Network Systems | Security offerings include NGFW, SWG and encryption capabilities. | No formal SLAs, but uses ActivePath technology (Intelligent Multipath Replication) to replicate traffic across paths and prevent brownouts/blackouts. | On-premises, hybrid and cloud-based architectures. | Introduced HughesON Managed SD-WAN in 2017, complementing its portfolio of managed services for multi-site organizations. Hughes manages thousands of SD-WAN endpoints worldwide and has won industry awards (e.g., SD-WAN Product of the Year 2018) for its capabilities. | N/A | Supports both broadband and LTE to reduce MPLS dependency. |
| KDDI | Offers KDDI Security Cloud based on Symantec Blue Coat, including NGFW, SWG, advanced threat prevention and managed threat detection/response. | Provides SLAs guaranteeing availability, performance, and support response times. | On-premises, hybrid and fully cloud-based SD-WAN. | KDDI deploys managed SD-WAN globally, partnering with vendors like Cisco Catalyst, Aruba EdgeConnect and Fortinet. It has notable customers such as All Nippon Airways, where KDDI’s SD-WAN enabled new work styles with consistent service quality across global sites. | N/A | Reduces WAN costs by using less expensive broadband instead of costly MPLS circuits. |
| Macquarie Technology Group | Dynamic key encryption at the packet level ensures end-to-end data security across all links. | Provides >99.9% uptime guarantee (with SLA) for its network. | On-premises, hybrid and cloud-based SD-WAN solutions. | Serves over 6,000 SD-WAN sites in Australia, having selected VMware VeloCloud after evaluating 28 providers globally. Macquarie has won the VMware Partner Innovation Award for SD-WAN in APAC and is recognized as the Best SD-WAN Supplier in the region. | N/A | Utilises multiple links (including low-cost broadband and 4G) to create faster, more reliable connections, reducing MPLS reliance and cutting operational expenses. |
| TPx Communications | Integrated security measures include VPN encryption and NGFW capabilities. | Offers SLAs with a 100% uptime guarantee for UCaaS when paired with their SD-WAN. | On-premises, hybrid and fully cloud-based SD-WAN solutions. | A leading US managed services provider with 50,000 customers and over 15,000 SD-WAN edges under management. An early adopter of VMware SD-WAN (since 2015), TPx has deep expertise in policy design and features on Vertical Systems Group’s U.S. Carrier Managed SD-WAN Leaderboard. | N/A | Leverages economical bandwidth options and eliminates the need for expensive MPLS circuits. |
| MetTel | MetTel's SD-WAN integrates its own stateful, context-aware NGFWs and segmentation capabilities for site-to-site communications without leaving the MetTel network. | Offers sub-second blackout and brownout protection, though no formal SD-WAN SLAs. | On-premises, hybrid and fully cloud-based SD-WAN solutions. | Delivers SD-WAN as a fully managed service across North America using its own cloud network (20 data centers/PoPs). MetTel maintains relationships with ~120 carriers and is an authorized Starlink reseller, extending its managed network services globally. | N/A | By combining existing and available circuits (DSL, LTE, 4G), MetTel’s SD-WAN reduces reliance on expensive MPLS circuits. |
| NTT Communications | NTT offers Secure Web Gateways at 75+ Local Cloud Centers worldwide, providing URL filtering, firewall protection, intrusion prevention and malware detection reporting. | Guarantees bandwidth (via SLA) and 99.999% network access (using MPLS-TP), plus SLAs for provisioning, recovery and notifications. | On-premises, hybrid and fully cloud-based SD-WAN solutions. | A global telecom provider recognized for launching the world’s first SD-WAN platform (coverage in 190+ countries). NTT operates a 100% software-defined network and maintains 75+ local cloud centers worldwide to optimize network, mobility and security services. | N/A | By supporting a mix of connectivity options (broadband, wireless, 4G/LTE), NTT’s SD-WAN allows businesses to reduce reliance on expensive MPLS circuits. |
| Orange Business Services | Orange's managed SD-WAN solutions offer NGFW, secure web gateways and encrypted VPN tunnels. | Provides clear SLAs guaranteeing performance and connectivity (e.g. site availability, device availability, time to repair). | On-premises, hybrid, and fully cloud-based SD-WAN options. | Leverages the world’s largest voice and data network (Orange Group), with 70+ cloud data centers and 50+ technology partnerships. Offers AI-driven networking and unified SD-WAN/SD-LAN solutions reinforced by 4G/5G connectivity. Recently launched SD-WAN Essentials, a co-managed service providing businesses greater control, reliability, performance, application-level routing and security features. | N/A | Utilises cost-effective connectivity options (broadband, LTE), reducing reliance on expensive MPLS circuits. |
| Singtel | Singtel's SD-WAN solutions incorporate integrated firewalls, antivirus, IPS, web filtering, and data encryption. | Provides SLA-guaranteed network performance over its business-grade network. | On-premises, hybrid and cloud-based SD-WAN solutions. | Asia’s leading communications technology group with a significant presence in Asia, Australia and Africa (serving 760M mobile users in 21 countries). Provides end-to-end network deployment services backed by 24/7 technical support and SLA-guaranteed performance. | N/A | By leveraging hybrid networking (MPLS + Internet), Singtel’s SD-WAN optimises bandwidth usage and reduces reliance on expensive circuits. |
| Spectrum Enterprise | Offers security measures such as firewalls, UTM, URL content filtering and intrusion prevention. | 100% network uptime SLA, with 24/7 US-based support and SLAs for uptime, latency and packet delivery. | Internet-based SD-WAN and hybrid configurations that integrate with existing Ethernet services. | Launched nationwide managed SD-WAN in 2019, integrated into its fiber network across the US. By utilising its fiber network, Spectrum provides highly available, scalable and geo-redundant connectivity, delivering high-performance, low-latency WAN solutions from any client location. | N/A | Leverages various connectivity options (broadband, LTE, etc.), allowing businesses to optimise costs by choosing the most appropriate transports. The managed model also reduces need for significant in-house resources. |
| Sprint | Sprint's SD-WAN integrates security measures including NGFW and UTM. | Offers SLAs for network node-to-node, end-to-end, and managed services (issues resolved within 24 hours). | On-premises, cloud-based and hybrid models. | First introduced SD-WAN to the Pacific region. Now covers 100+ countries, offering three tiers: SD-WAN Complete (fully managed end-to-end), SD-WAN Complete with Co-Management (shared control), and SD-WAN Service (network optimisation without full management), utilising Cisco Meraki, Versa Networks and VMware VeloCloud. | N/A | By using a mix of MPLS and broadband, Sprint’s SD-WAN optimises bandwidth usage and can lower operational expenses. |
| Tata Communications | Tata's managed SD-WAN incorporates advanced security measures such as NGFW, secure web gateways, and micro-segmentation. | Offers end-to-end SLA guarantees for the WAN and uptime guarantees as part of its SLA framework. | On-premises, hybrid and fully cloud-based options. | A leading Indian telecom company providing global network services. Has implemented SD-WAN at 5,000+ sites in 120+ countries, managing over 3,000 customer sites worldwide. Recently launched a unified hosted SASE solution combining SD-WAN with SSE capabilities, and offers its own IZO SD-WAN managed solution covering 130+ countries. | N/A | Leverages existing internet connections to reduce reliance on expensive MPLS circuits. Also provides a fully managed service with a single SLA, simplifying management and potentially lowering operational costs. |
| Telefónica | Telefónica's SD-WAN solutions incorporate security measures such as NGFW, SASE and ZTNA. | Seamless integration with major cloud platforms, with private backbones for multi-cloud, plus global SLAs and traffic guarantees (e.g. via Telefónica Global Solutions network). | On-premises, hybrid, and fully cloud-based SD-WAN options. | Spanish multinational with SD-WAN offerings via partnerships (e.g. Nokia Nuage). Since 2017, uses Nuage’s VNS platform to deliver automated, end-to-end services with customer self-service portals. In 2024, integrated Nokia’s Network Exposure Function in Spain to leverage Network-as-Code and developed private 5G capabilities for enterprise use. | N/A | By leveraging low-cost broadband and consolidating network functions, Telefónica's SD-WAN solutions help reduce reliance on expensive MPLS circuits. |
| Telia | Telia's SD-WAN provides firewall for direct internet access from offices. | 24-hour service level for customer edge devices, ensuring predictable service levels. | Fully managed and co-managed SD-WAN services. | Allows enterprises to attach their SD-WAN overlay to Telia Carrier’s backbone network. For security, Telia leverages relationships with Fortinet and Check Point. Telia was highlighted on Vertical Systems Group’s SD-WAN Coverage Analysis leaderboard as a top Global Provider. | N/A | Enables flexible use of both private (DataNet) and internet connections at the same site. Critical traffic can use private links while less important traffic uses internet, optimising cost and performance. |
| Telstra | The solution integrates NGFW, ZTNA and advanced threat protection. | SLAs covering uptime and latency guarantees. | On-premises, hybrid, and cloud-based deployments. | Australia's largest telco (among the world’s top 20) that provides fully managed services including project management, design, provisioning and maintenance of network infrastructure, backed by performance and uptime SLAs. Its SD-WAN combines Australia-wide gateways with partnerships (Cisco Meraki, Cisco Catalyst, VMware VeloCloud) to meet diverse customer needs. | N/A | Reduces reliance on MPLS by leveraging broadband with optimised routing. Also offers simplified licensing and bundled managed services to lower operational costs. |
| Verizon | Verizon adds managed security services, including built-in NGFW, ZTNA, and SWG. Also offers managed threat detection and response services. | Performance SLAs with uptime guarantees and latency thresholds. | On-premises, hybrid, and cloud-based SD-WAN deployments. | Offers a wide range of managed SD-WAN solutions through partnerships with leading vendors (Cisco, VMware, Fortinet, Versa, etc.). Focuses on security, cloud connectivity and global enterprise networking, integrating SD-WAN with its private network services and incorporating Zero Trust frameworks and AI-powered analytics for proactive issue resolution. | N/A | Offers flexible pricing models (pay-as-you-go, subscription) and streamlines operations by integrating multiple network functions into one solution, reducing hardware dependencies. |
| Virgin Media Business | Virgin Media offers next-generation security features such as stateful and next-gen firewalls, DNS filtering, URL filtering and antivirus protection. | Service level agreements (SLAs) tailored to the company’s specific infrastructure and needs. | On-premises, hybrid and cloud-based models. | Provides managed SD-WAN services with a focus on high-speed broadband and resilient connectivity. Primarily partners with Versa Networks and Fortinet to deliver fully managed network services that cater either to secure cloud connectivity or strict security requirements. | N/A | Utilises a hybrid network approach, combining private and public networks to optimise connectivity and reduce reliance on expensive circuits. |
| Vodafone | Vodafone's SD-WAN incorporates security measures such as NGFW, ZTNA and SASE frameworks. | Performance SLAs including uptime guarantees and latency thresholds. | On-premises, hybrid and fully cloud-based SD-WAN options. | Delivers managed SD-WAN via partnerships with Cisco Meraki, VMware VeloCloud and Juniper Networks. Vodafone’s SD-WAN is tailored for enterprises needing global coverage and 5G-ready networking, backed by Vodafone’s extensive fibre and mobile infrastructure. | N/A | Leverages cost-effective broadband, consolidates network functions, and offers straightforward licensing models. This reduces reliance on MPLS and lowers operational expenses. |
| Windstream | Windstream's SD-WAN incorporates security measures such as NGFW, ZTNA and SASE frameworks. | Offers performance SLAs with uptime guarantees and latency thresholds. | Offers flexible deployment models, including on-premises, hybrid and fully cloud-based SD-WAN. | Offers managed SD-WAN through partnerships with VMware VeloCloud and Fortinet. Focuses on optimising bandwidth utilisation, improving network security and ensuring high availability for multi-site businesses. Windstream integrates SD-WAN with its Kinetic Business fiber network to provide a hybrid WAN strategy for secure, scalable, high-speed connectivity. | N/A | Consolidates network functions and leverages cost-effective broadband, reducing reliance on expensive MPLS circuits and cutting operational expenses. |
| Zayo Group | Zayo SD-WAN incorporates security measures such as NGFW, ZTNA and SASE frameworks. | Guarantees 99.99% network uptime for on-net fiber and waves, with 24x7 service assurance and real-time network monitoring via its NOC. | On-premises, hybrid, and fully cloud-based SD-WAN solutions. | Delivers managed SD-WAN services with a focus on fiber-optic infrastructure and cloud connectivity. The platform is built to provide secure, low-latency networking for businesses relying on hybrid and multi-cloud environments. Zayo’s SD-WAN integrates with its extensive metro and long-haul fiber networks, ensuring high-performance, resilient connectivity alongside real-time analytics and intelligent traffic management. | N/A | By leveraging low-cost broadband options and consolidating network functions, Zayo's SD-WAN helps reduce reliance on expensive MPLS circuits and lower operational expenses. |
SD-WAN Vendors
- Fortinet
- Cisco
- Palo Alto Networks
- Versa Networks
- HPE (Aruba EdgeConnect)
- Huawei
- Juniper Networks
- Ericsson (Cradlepoint)
- Peplink
- Barracuda Networks
- Aryaka
- Cato Networks
- Ecessa
- Adaptiv Networks
- Extreme Networks
- FatPipe Networks
- Forcepoint
- Mushroom Networks
- Nokia (Nuage Networks)
- Oracle
- Riverbed Technology
- SonicWall
- Sophos
- Turnium
- VMware VeloCloud
- WatchGuard Technologies
- Zyxel
- Bigleaf Networks
- Checkpoint
- Cloudflare
- FlexiWAN
- Netskope
- Zscaler
- AT&T
- BT
- Lumen (CenturyLink)
- China Mobile (CMI)
- China Telecom
- China Unicom
- Comcast Business
- Deutsche Telekom
- GTT Communications
- Hughes Network Systems
- KDDI
- Macquarie Technology Group
- TPx Communications
- MetTel
- NTT Communications
- Orange Business Services
- Singtel
- Spectrum Enterprise
- Sprint
- Tata Communications
- Telefónica
- Telia
- Telstra
- Verizon
- Virgin Media Business
- Vodafone
- Windstream
- Zayo Group
Fortinet
Market Leader North America Latin America Europe Middle East & Africa Asia-Pacific Security
Fortinet claims to be the first vendor to integrate security and network functionality into a single system. This is achieved through their Secure SD-WAN solution - fully integrated into the FortiGate platform.
Now deployed by over 31,000 customers globally, prior to their SD-WAN solution, Fortinet were primarily a cybersecurity company. Originally producing FortiGate as a physical firewall solution, FortiGate featured alongside early Fortinet solutions, such as endpoint security and intrusion detection systems. In 2016, Fortinet moved onto their Security Fabric architecture (to enable communication between multiple network security products) which was their previous most network-focused offering.
By integrating their SD-WAN solution into the FortiGate security platform, Fortinet SD-WAN has become the forefront of their broader portfolio, offering businesses with all-round network security capabilities and an ideal choice for enterprises with sensitive data, secure connectivity or requirements for in-depth security monitoring. This has led to Fortinet's secure SD-WAN being one of the most-used solutions by the Telco SD-WAN providers.
| Feature | Vendor/Provider Support |
|---|---|
| Centralised Cloud Management | Fortinet’s FortiManager provides centralised SD-WAN management with real-time visibility, unified policy control and automation. |
| Support for Multiple Connection Types | Supports broadband, LTE, MPLS and satellite. Uses application-aware routing with FortiOS and AI-driven analytics to optimise paths dynamically for performance and reliability. Multiple VPNs can run on a single WAN connection and WAN Path Controller ensures seamless performance. |
| Integrated Security Features | Built-in Next-Generation Firewall (NGFW), Zero Trust Network Access (ZTNA), IPS and SSL inspection. |
| Quality of Service (QoS) | Offers a large range of QoS settings, actioned through dynamic prioritisation and traffic shaping. Also uses deep packet inspection (DPI), application-based policies and WAN optimisation to improve performance for SaaS, VoIP, and cloud applications. |
| Scalability and Flexibility | Scales from SMBs to global enterprises. Cloud-based orchestration supports multi-site expansion and hybrid workforce connectivity. FortiManager offers Zero-touch provisioning (ZTP), automated deployments and centralised policy management and integrates legacy infrastructure. |
| Cloud and Multi-Cloud Integration | Direct cloud on-ramps to AWS, Azure, and Google Cloud. Supports private backbone routing for lower latency and improved cloud application performance. |
| Resilience and Failover Capabilities | Sub-second failover with multi-path redundancy and real-time link monitoring to ensure uninterrupted connectivity. |
| Cost Efficiency | Reduces costs by leveraging low-cost broadband, consolidating networking and security functions and offering flexible licensing models. |
| Analytics and Reporting | FortiAnalyzer provides AI-driven insights, historical trends and real-time visibility into network performance and security. |
| Programmatic APIs | Open APIs for automation, custom integrations and network management. |
| Support for Cellular Connectivity | 5G/LTE support with integrated SIM management for failover, redundancy, and remote site connectivity. |
| AI Integrations | Uses AI-powered automation and anomaly detection. |
| Deployment Models Supported | On-premises, cloud-managed, and hybrid SD-WAN options. |
| Compliance and Regulatory Certifications | ISO 27001, SOC 2, PCI DSS and HIPAA compliance for regulated industries. |
| Support and Training Options | Fortinet offers a wide variety of training, as well as their QuickStart SD-WAN consulting services to help customers accelerate the time-to-value of their SD-WAN network implementation. |
| Target-Market Customers | Targets Finance, Healthcare, Retail, Manufacturing, Education, Government, Technology, Transportation, Energy and Telecommunications. |
Cisco

Market Leader North America Latin America Europe Middle East & Africa Asia-Pacific Security
Cisco entered the market through Meraki SD-WAN, which it acquired in 2012. Prior to this, Cisco's primary offering was Cisco IWAN, which was an on-premises SD-WAN device based on ISR branch routing.
Finally, in 2017, Cisco expanded its offerings through the acquisition of Viptela, creating a portfolio that could cater to all business requirements through the easier-to-use Meraki and more-in depth Viptela - which is reflected by the large volumes of SD-WAN providers offering both Cisco Catalyst sd wan and Cisco Meraki, showcasing that they are clearly one of the best sd wan vendors.
Viptela was acquired by Cisco due to the Viptela SD-WAN solution being specifically designed with a separation of data, control and management planes, which complimented Cisco's Digital Network Architecture (DNA). Today, Cisco's main SD-WAN (now rebranded from Cisco Viptela to Cisco Catalyst) is recognised as one of the leading SD-WAN solutions in the market, whilst Meraki SD-WAN is widely used for more simplified use cases.
| Feature | Vendor/Provider Support |
|---|---|
| Centralised Cloud Management | Cisco SD-WAN is managed via vManage, a unified dashboard providing real-time visibility, policy control and automation. |
| Support for Multiple Connection Types | Supports MPLS, broadband, LTE and satellite with intelligent path selection using AI-driven analytics. Utilises application-aware routing to optimise traffic paths based on real-time performance metrics. Supports multiple VPNs on a single WAN connection. |
| Integrated Security Features | Offers built-in NGFW, IPS, DNS security, URL filtering, and Zero Trust Network Access (ZTNA). Integrates with Cisco Umbrella for cloud security and provides end-to-end encrypted traffic protection. |
| Quality of Service (QoS) | Implements QoS with dynamic prioritisation for applications. Ensures low latency for voice, video and cloud services using policy-based traffic management. |
| Scalability and Flexibility | Designed for large enterprises, scaling across thousands of sites. Supports hybrid workforces and cloud-based expansions, with zero-touch provisioning (ZTP) and policy-based automation. Integrates with existing networking infrastructure, including MPLS. |
| Cloud and Multi-Cloud Integration | Provides direct cloud connectivity with AWS, Azure, and Google Cloud through optimised cloud on-ramps. Uses Cisco Cloud OnRamp for SaaS to improve application performance. |
| Resilience and Failover Capabilities | Ensures sub-second failover with multi-path redundancy and advanced link health monitoring. Uses Cisco's SD-WAN fabric for seamless failover in case of outages. |
| Cost Efficiency | Reduces costs by leveraging broadband, consolidating security and networking functions, and offering flexible licensing models. Helps reduce reliance on expensive MPLS circuits. |
| Analytics and Reporting | vAnalytics provides AI-driven insights, historical performance trends and application-level visibility. |
| Programmatic APIs | Offers open APIs for automation, network programmability and integration with IT workflows. |
| Support for Cellular Connectivity | Supports LTE/5G connectivity for backup and primary WAN links. |
| AI Integrations | Uses AI-driven analytics for automated policy adjustments, traffic optimisation and predictive network issue detection. |
| Deployment Models Supported | Supports on-premises, hybrid, and fully cloud-based SD-WAN deployments. |
| Compliance and Regulatory Certifications | Holds certifications including ISO 27001, SOC 2 and PCI DSS. |
| Support and Training Options | Offers 24/7 global support, dedicated technical account managers and online training through Cisco Learning Network. Includes professional and managed services for ongoing support. |
| Target-Market Customers | Targets Finance, Healthcare, Retail, Manufacturing, Education, Government, Technology, Transportation, Energy and Telecommunications sectors. |
Palo Alto Networks

Leader North America Latin America Middle East & Africa Security
Palo Alto Networks have long been known for their cybersecurity capabilities, predominantly through their Next-Generation Firewall (NGFW) technology. Through PAN-OS, Palo Alto provided Layer 7 visibility and control over network traffic utilising their firewall appliances – making them well-placed to move into the SD-WAN market for more security-focused use cases.
Palo Alto Networks produced their SD-WAN solution in 2020, self-dubbing it the "Industry's First Next-Generation SD-WAN Solution" and formed part of Palo Alto Networks' CloudGenix SD-WAN offering.
In 2021, Palo Alto launched Prisma Access, a Secure Access Service Edge (SASE) solution to implement both security and networking capabilities, which includes Application-Aware Routing (AAR) and Zero Touch Provisioning into a single solution. This has proved to be successful for Palo Alto, who are currently one of only three vendors recognised as a Leader across all three SASE-related Magic Quadrant reports:
Security Service Edge (SSE),
Single-Vendor SASE,
SD-WAN
| Feature | Vendor/Provider Support |
|---|---|
| Centralised Cloud Management | Palo Alto’s Prisma SD-WAN offers centralised cloud-based management via the Prisma SD-WAN dashboard. Prisma provides real-time visibility, unified policy control and AI-driven insights to simplify operations and improve network performance. |
| Support for Multiple Connection Types | Supports broadband, LTE, MPLS and satellite connections. Uses AI-powered path selection and real-time performance monitoring to optimise traffic routing dynamically, with sub-second failover and traffic steering based on real-time network conditions. |
| Integrated Security Features | Offers built-in Next-Generation Firewall (NGFW), Zero Trust Network Access (ZTNA) and threat protection, alongside deep packet inspection and segmentation. |
| Quality of Service (QoS) | Offers dynamic QoS settings, application-aware prioritisation and automated bandwidth allocation to maintain low latency for critical applications. Utilises both policy-based routing and WAN optimisation to reduce latency and improve application performance. |
| Scalability and Flexibility | Scales from small branch offices to large global enterprises. Supports hybrid workforce needs with cloud-managed and on-premises deployment options. Offers zero-touch provisioning and automated deployments via Prisma SD-WAN, with integrations for existing infrastructure. |
| Cloud and Multi-Cloud Integration | Direct cloud connections to AWS, Azure, Google Cloud, and SaaS applications. Uses private backbone connectivity and intelligent traffic steering to enable multi-cloud performance. |
| Resilience and Failover Capabilities | Provides sub-second failover, multi-path redundancy and AI-driven link monitoring. |
| Cost Efficiency | Reduces reliance on expensive MPLS circuits by leveraging broadband and cloud-based security. Consolidates networking and security functions to lower operational costs. |
| Analytics and Reporting | AI-driven insights, real-time and historical analytics and visibility into application and network performance through Prisma SD-WAN’s analytics dashboard. |
| Programmatic APIs | Open APIs enable automation, integration with IT service management tools and custom policy configurations. |
| Support for Cellular Connectivity | Supports LTE and 5G for backup connectivity and primary WAN in remote locations. |
| AI Integrations | Uses AI-powered analytics for predictive network optimisation, self-healing capabilities and automated policy tuning. |
| Deployment Models Supported | Available as a fully cloud-managed, hybrid, or on-premises solution. |
| Compliance and Regulatory Certifications | Certified for ISO 27001, SOC 2, PCI DSS and HIPAA. |
| Support and Training Options | 24/7 customer support, dedicated account managers, online training resources and documentation for self-service learning. |
| Target-Market Customers | Targets customers from Finance, Healthcare, Retail, Manufacturing, Education, Government, Technology, Transportation, Energy and Telecommunications markets. |
Versa Networks

Leader North America Latin America Europe Middle East & Africa Asia-Pacific Multi-tenancy Multi-deployment
Headquartered in California, Versa Networks were founded in 2012 and were one of the startups that helped form the SD-WAN market. Initially started by two brothers, Kumar Mehta who had previously served as VP Engineering at Juniper Networks (2004-2012) and Apurva Mehta, CTO and Chief Architect at Juniper Networks' Mobility Business Unit, Versa came from a background of networking expertise.
By October 2019, Versa Networks had over 1,000 total customers and sold more than 200,000 software licenses.
Versa’s operating system (VOS) not only offers SD-WAN but has been extended to form a SASE solution, making Versa Networks currently one of only three vendors recognised as a Leader across all three SASE-related Magic Quadrant reports:
Security Service Edge (SSE),
Single-Vendor SASE,
SD-WAN
| Feature | Vendor/Provider Support |
|---|---|
| Centralised Cloud Management | Versa offers a unified management platform, Versa Titan, providing real-time visibility, centralised policy enforcement, and AI-driven insights. |
| Support for Multiple Connection Types | Supports broadband, MPLS, LTE/5G, and satellite. Versa’s AI-driven analytics optimise traffic paths dynamically, utilising real-time link monitoring and application-aware routing. Versa also supports multiple VPNs on a single WAN link. |
| Integrated Security Features | Offers built-in Next-Generation Firewall (NGFW), Secure Web Gateway (SWG) and Zero Trust Network Access (ZTNA). |
| Quality of Service (QoS) | Provides granular QoS policies with dynamic traffic prioritisation and both deep pack inspection and WAN optimisation techniques to help reduce latency. |
| Scalability and Flexibility | Supports enterprise-wide scalability, with easy expansion to new branches and hybrid workforces. Offers zero-touch provisioning (ZTP) and automated deployments. |
| Cloud and Multi-Cloud Integration | Provides direct cloud on-ramps to AWS, Azure and Google Cloud; Versa’s private backbone improves cloud performance. |
| Resilience and Failover Capabilities | Sub-second failover with multi-path redundancy and real-time link health monitoring. |
| Cost Efficiency | Reduces reliance on MPLS by leveraging broadband and LTE/5G. Integrated security eliminates the need for separate firewalls/other security systems, lowering costs. |
| Analytics and Reporting | AI-driven analytics provide historical insights, real-time monitoring and application-level visibility to optimise network performance. |
| Programmatic APIs | Versa offers APIs and SDKs, enabling automation and integration with third-party platforms for custom workflows. |
| Support for Cellular Connectivity | Supports LTE and 5G for primary or backup connectivity. |
| AI Integrations | Uses AI for predictive analytics, automated policy adjustments and self-healing capabilities. |
| Deployment Models Supported | Supports on-premises, hybrid, and fully cloud-based SD-WAN deployments. |
| Compliance and Regulatory Certifications | Certified for ISO 27001, SOC 2, PCI DSS, and HIPAA. |
| Support and Training Options | Offers 24/7 support, dedicated account managers and online training. |
| Target-Market Customers | Targets Finance, Healthcare, Retail, Manufacturing, Education, Government, Technology, Transportation, Energy and Telecommunications. |
Hewlett Packard Enterprise (HPE)

Leader North America Latin America Europe Middle East & Africa Asia-Pacific SMBs
Hewlett Packard Enterprise (HPE) have formed the HPE Aruba EdgeConnect SD-WAN solution from their prior networking expertise and multiple acquisitions of other SD-WAN vendors.
HPE have been long term experts in Software Defined Networking (SDN) solutions. Before offering SD-WAN, HPE offered SDN products with OpenFlow-enabled switches and HP Cloud Managed Network Wireless LAN for small and mid-sized businesses. These lay the foundations for a software-based networking approach, which was later realised in March 2015 when they acquired Aruba Networks.
Improving upon this, in 2020 HPE acquired Silver Peak Systems, who were well-known for their EdgeConnect SD-WAN solution, enabling HPE to integrate EdgeConnect into their Aruba Edge Service platform and now their SD-WAN offers WAN edge infrastructure, as well as advanced routing capabilities.
HPE Aruba's SD-WAN solution now consists of three main components:
EdgeConnect: Available as physical or virtual appliances, supporting hybrid WAN architecture
Aruba Orchestrator: Central administration console for network management
Aruba Boost: Optional WAN optimisation performance pack
| Feature | Vendor/Provider Support |
|---|---|
| Centralised Cloud Management | HPE’s Aruba EdgeConnect SD-WAN provides centralised cloud-based orchestration through Aruba Orchestrator. |
| Support for Multiple Connection Types | Supports broadband, MPLS, LTE, and satellite connections. Uses intelligent path control and first-packet iQ for application-aware routing. |
| Integrated Security Features | Includes built-in NGFW, IDS/IPS and cloud-based security integrations via Aruba ESP and SASE partnerships. Zero Trust capabilities ensure end-to-end security. Whilst support for multiple VPNs on a single WAN connection enable improved segmentation and security. |
| Quality of Service (QoS) | Offers QoS with dynamic traffic prioritisation and automated bandwidth allocation. Improves application performance through first-packet iQ, WAN optimisation, TCP acceleration and deep packet inspection (DPI) techniques. |
| Scalability and Flexibility | Scales for enterprises of all sizes with Zero Touch Provisioning and automated deployments, multi-cloud integration and support for hybrid workforces. |
| Cloud and Multi-Cloud Integration | Provides direct cloud connections to AWS, Azure and Google Cloud, with optimised cloud access and private backbone options. |
| Resilience and Failover Capabilities | Offers sub-second failover, multi-path redundancy and link health monitoring to prevent downtime. |
| Cost Efficiency | Reduces costs by leveraging broadband connectivity, consolidating network functions and offering flexible licensing models. |
| Analytics and Reporting | Provides AI-driven insights, real-time monitoring and application-level visibility through Aruba Orchestrator. |
| Programmatic APIs | Offers RESTful APIs for automation and integration with third-party IT systems. |
| Support for Cellular Connectivity | Supports LTE and 5G connectivity for backup and remote deployments. |
| AI Integrations | Uses AI-powered analytics for predictive performance management, automated policy adjustments and self-healing network capabilities. |
| Deployment Models Supported | Supports on-premises, hybrid and fully cloud-based SD-WAN. |
| Compliance and Regulatory Certifications | Complies with ISO 27001, SOC 2, PCI DSS, and HIPAA standards. |
| Support and Training Options | Provides 24/7 global support, online training and dedicated account managers. |
| Target-Market Customers | Focuses on Finance, Healthcare, Retail, Manufacturing, Education, Government, Technology, Transportation, Energy and Telecommunications. |
Huawei

Challenger Latin America Europe Middle East & Africa Asia-Pacific Large Enterprises
A Chinese vendor, since 2012 Huawei have become the largest telecommunications equipment manufacturer globally, typically known for technology services such as their breakthrough C&C08 telephone switch, which was the most powerful switch in China upon released in 1993.
Huawei previously offered an SDN-based agile controller, launched in 2017 that would later become their SD-WAN solution. In 2018, Huawei progressed via the launch of their SD-WAN cloud services and as of more recent, Huawei have been recognised by Gartner Peer Insights Customers' Choice for SD-WAN for four consecutive times.
Huawei's cloud services include cloud gateways such as Azure, Alibaba Cloud, Huawei Cloud, AWS (Amazon Web Services), the Google Cloud Platform and e-Cloud, which can be essential for businesses utilising a large range of Software-as-a-Service (SaaS) applications or WAN edge infrastructures.
To further create a secure SD-WAN offering, Huawei has integrated SASE capabilities into their SD-WAN through their Xinghe Intelligent SASE Solution, complying with MEF SASE model standards to reduce integration and management complexity for network administrators.
| Feature | Vendor/Provider Support |
|---|---|
| Centralised Cloud Management | Huawei's SD-WAN solution utilises the iMaster NCE platform, offering unified control and real-time visibility across the network. |
| Support for Multiple Connection Types | Huawei supports various transport types, including broadband, LTE, MPLS and satellite connections. |
| Integrated Security Features | Integrates security features such as Next-Generation Firewall (NGFW) and supports end-to-end IPsec encryption. |
| Quality of Service (QoS) | Huawei offers advanced QoS settings, including hierarchical QoS (HQoS) and application-based intelligent traffic steering, ensuring optimal performance for key applications. |
| Scalability and Flexibility | Supports large-scale deployments with flexible networking options. Implements zero-touch provisioning (ZTP) and automated deployments. |
| Cloud and Multi-Cloud Integration | Huawei integrates with leading cloud platforms, providing direct cloud on-ramps and specialised routing algorithms. |
| Resilience and Failover Capabilities | Huawei's SD-WAN offers failover mechanisms such as multi-path redundancy and link health monitoring. |
| Cost Efficiency | By leveraging cost-effective broadband and consolidating network functions, Huawei's SD-WAN solution reduces reliance on expensive MPLS circuits and lowers operational expenses. |
| Analytics and Reporting | Provides detailed analytics and reporting capabilities, offering AI-driven insights and application-level visibility. |
| Programmatic APIs | Huawei offers open APIs within its SD-WAN solution, enabling automation and simplifying integration with existing systems/infrastructure. |
| Support for Cellular Connectivity | Huawei supports both LTE and 5G connectivity. |
| AI Integrations | Huawei utilises AI for predictive analytics and automated policy adjustments. |
| Deployment Models Supported | Huawei's SD-WAN offers on-premises, hybrid and fully cloud-based deployment options. |
| Compliance and Regulatory Certifications | Huawei's SD-WAN complies with the MEF (Metro Ethernet Forum) standard, CSA STAR gold certification, NIST cybersecurity framework and ISO 27018. |
| Support and Training Options | Huawei provides customer support including both 24/7 helpdesks and online training resources. |
| Target-Market Customers | Huawei's SD-WAN solution is suited for various industries including finance, healthcare, retail, manufacturing, education, government, technology, transportation, energy and telecommunications. |
Juniper Networks

Visionary North America Latin America Europe Middle East & Africa Asia-Pacific AI Capabilities
Juniper Networks SD-WAN’s unique selling point is primarily in its vast amounts of Artificial Intelligence (AI) integrations. These include:
Mist AI for insights and automated troubleshooting
Marvis, an AI-driven virtual network assistant for deep insights into client and network behaviours
Automated network security and analytics via AI
Whilst several other vendors have integrated AI for features such as analytics insights and reporting, in our opinion, Juniper Networks has by far the most AI integrations into its services, making it a top SD-WAN provider for AI integrations. One benefit of this use of AI is the reduced complexity for network administrators, who benefit from WAN optimization, advanced routing, Zero Touch Provisioning and secure SD-WAN, all whilst reducing network costs through lower operational workloads.
Following the October 2020 acquisition of 128 Technology, Juniper Networks has further strengthened their market position by adding session-aware networking capabilities to their AI-driven portfolio of features.
| Feature | Vendor/Provider Support |
|---|---|
| Centralised Cloud Management | Juniper’s Mist AI-driven cloud management provides real-time visibility, automation and unified control via the Mist UI. |
| Support for Multiple Connection Types | Supports MPLS, broadband, LTE and satellite with AI-driven analytics and Juniper’s Session Smart Routing for handling dynamic traffic routing. |
| Integrated Security Features | Built-in Next-Generation Firewall (NGFW), Zero Trust Security and Threat Intelligence via Juniper’s Security Director Cloud, supporting multiple VPNs on a single WAN connection for improved segmentation and security. |
| Quality of Service (QoS) | AI-driven dynamic QoS, alongside deep packet inspection (DPI) and policy-based routing (PBR), prioritises important applications, automatically adjusting bandwidth allocation based on network conditions. |
| Scalability and Flexibility | Scales for large enterprises with AI-driven automation, supporting distributed branches and hybrid workforces. Also features zero-touch provisioning (ZTP) with AI-driven automation for branch scaling. |
| Cloud and Multi-Cloud Integration | Direct integrations with AWS, Azure and Google Cloud, with cloud on-ramps and private backbone options for optimised multi-cloud access. |
| Resilience and Failover Capabilities | Offers sub-second failover and multi-path redundancy, with AI-driven link health monitoring. |
| Cost Efficiency | Reduces MPLS dependency by leveraging broadband, with AI-driven optimisation lowering operational expenses. |
| Analytics and Reporting | Offers AI-driven insights, historical trend analysis and detailed application visibility via Mist AI and Marvis Virtual Network Assistant. |
| Programmatic APIs | Open APIs and SDKs enable seamless integration with third-party platforms. |
| Support for Cellular Connectivity | Supports 5G/LTE for failover, remote site deployments and mobile workforce connectivity. |
| AI Integrations | Mist AI enables predictive analytics, self-healing networks and automated policy adjustments. |
| Deployment Models Supported | Supports on-premises, hybrid, and cloud-based SD-WAN deployments. |
| Compliance and Regulatory Certifications | Juniper offers ISO 27001, SOC 2, PCI DSS and HIPAA certifications. |
| Support and Training Options | Provides 24/7 global support, dedicated account managers, online documentation and AI-driven support assistance via Marvis. |
| Target-Market Customers | Designed for Finance, Healthcare, Retail, Manufacturing, Education, Government, Technology, Transportation, Energy and Telecommunications. |
Ericsson (Cradlepoint)

Niche Player North America Latin America Europe Asia-Pacific Remote Workforces
Having acquired Cradlepoint in 2020, Ericsson’s SD-WAN solution has a heavy focus on the cellular wireless and 5G enterprise markets, which has followed into their SD-WAN design. By integrating Cradlepoint's prior SD-WAN solution into Ericsson’s NetCloud Exchange architecture, the solution is ideal for distributed sites, vehicles, Internet of Things (IoT) and remote work environments. This is primarily due to the specialisations in 5G-optimisations for cellular-specific traffic, which can be essential for network resilience.
Having acquired Ericom, a cloud-based security company, improvements have been seen on Cradlepoint's NetCloud platform, which now utilises Ericom's zero trust and cloud-based security solutions to form the basis of the new Cradlepoint NetCloud Threat Defence cloud service to create secure SD-WAN edges. This was an essential step for Ericsson to better deliver edge computing architectures and enable the use of IoT.
| Feature | Vendor/Provider Support |
|---|---|
| Centralised Cloud Management | Offers a cloud-native SD-WAN platform with real-time visibility, centralised policy control and AI-driven analytics. |
| Support for Multiple Connection Types | Supports broadband, LTE, MPLS and satellite, with AI-driven traffic optimisation and real-time traffic analysis for route switching. |
| Integrated Security Features | Features built-in Next-Generation Firewall (NGFW), Zero Trust Network Access (ZTNA) and threat intelligence integrations to improve security, alongside support for multiple VPNs per WAN connection for improved segmentation capabilities. |
| Quality of Service (QoS) | Offers QoS settings with dynamic traffic prioritisation, WAN optimisation, deep packet inspection and AI-driven application policies, particularly for cloud-based and latency-sensitive applications. |
| Scalability and Flexibility | Designed for large enterprises and service providers. Supports zero-touch provisioning, existing legacy network infrastructure and third-party security platforms. |
| Cloud and Multi-Cloud Integration | Direct cloud on-ramps and private backbone connectivity for AWS, Azure and Google Cloud. |
| Resilience and Failover Capabilities | Provides sub-second failover, multi-path redundancy and real-time link monitoring to maintain high availability. |
| Cost Efficiency | Reduces costs by leveraging broadband, consolidating network functions and offering flexible licensing models. |
| Analytics and Reporting | AI-driven analytics provide deep insights into network performance, bandwidth usage and enable predictive maintenance. |
| Programmatic APIs | Offers open APIs and SDKs for automation, enabling integrations with third-party network management tools. |
| Support for Cellular Connectivity | Supports LTE/5G for backup connectivity and remote site connectivity. |
| AI Integrations | Uses AI for predictive analytics, self-healing network capabilities and automated policy adjustments. |
| Deployment Models Supported | Available as on-premises, hybrid and cloud-native. |
| Compliance and Regulatory Certifications | Holds certifications including ISO 27001, SOC 2 and PCI DSS. |
| Support and Training Options | Provides 24/7 support, dedicated account management and online training. |
| Target-Market Customers | Focuses on Telecommunications, Finance, Healthcare, Retail, Manufacturing, Government, Transportation, Energy, Technology and Education. |
Peplink

Niche Player North America Europe Asia-Pacific SMBs
Peplink SD-WAN primarily focuses on wireless and mobile SD-WAN solutions, which compliments their global coverage for their eSIM data plans. Typically targeting Small to medium enterprises (with 1-150 recommended users per deployment), Peplink SD-WAN is ideal for use cases such as IoT, public safety, transport and broadcasting.
Prior to SD-WAN, Peplink was known for pioneering multi-WAN technology and link aggregation solutions. By already having made solutions (SpeedFusion VPN) for combining multiple WAN sources into one connection, Peplink have long term expertise in getting the most out of WAN connectivity and ensuring consistent uptimes, which has continued on through their SD-WAN solution.
These capabilities have helped Peplink garner more than 17,000 SD-WAN subscribers, with customers operating in a range of markets, such as construction, transport and retail.
| Feature | Vendor/Provider Support |
|---|---|
| Centralised Cloud Management | Peplink’s InControl 2 platform provides centralised SD-WAN management with real-time visibility, device control and automated reporting. InControl 2 also enables bulk configuration, remote troubleshooting and firmware updates for the entire network. |
| Support for Multiple Connection Types | Supports broadband, LTE, 5G, MPLS and satellite connections with intelligent load balancing and failover. Uses SpeedFusion technology to aggregate multiple links. |
| Integrated Security Features | Offers built-in Next-Generation Firewall (NGFW), intrusion prevention and content filtering. Supports Zero Trust Network Access (ZTNA) and integration with third-party security platforms, whilst also supporting multiple VPNs over a single WAN connection. |
| Quality of Service (QoS) | Provides application-based QoS with dynamic bandwidth control measures, WAN smoothing and deep packet inspection (DPI) for core application performance. |
| Scalability and Flexibility | Supports deployments from small businesses to large enterprises with multi-site scalability and cloud integrations. Peplink’s API and InControl 2 also enable integrations with existing network infrastructure. |
| Cloud and Multi-Cloud Integration | Direct integration with AWS, Azure, Google Cloud and private clouds via SpeedFusion Cloud. |
| Resilience and Failover Capabilities | Offers hot failover using SpeedFusion, WAN smoothing and multi-WAN redundancy to ensure sub-second failover and uninterrupted connectivity. |
| Cost Efficiency | Reduces reliance on expensive MPLS by leveraging low-cost broadband and cellular connectivity, whilst SpeedFusion optimises bandwidth usage. |
| Analytics and Reporting | InControl 2 provides real-time analytics, historical trend reports and AI-driven insights for proactive network management. |
| Programmatic APIs | Offers open RESTful APIs for automation and third-party integrations. |
| Support for Cellular Connectivity | Peplink provides LTE/5G connectivity with multi-carrier support and seamless failover. Ideal for mobile deployments, remote locations and edge connectivity for technologies such as IoT. |
| AI Integrations | Uses AI-driven adaptive traffic management and AI for automated failover capabilities. |
| Deployment Models Supported | Offers on-premises, cloud-based and hybrid SD-WAN deployments. |
| Compliance and Regulatory Certifications | Holds ISO 27001, SOC 2 and PCI DSS certifications. |
| Support and Training Options | Provides 24/7 global support, dedicated account managers, online training and documentation. |
| Target-Market Customers | Targets Finance, Healthcare, Retail, Manufacturing, Education, Government, Technology, Transportation, Energy and Telecommunications sectors. |
Barracuda Networks

Niche Player North America Europe Asia-Pacific Microsoft Azure
Barracuda Networks offers two SD-WAN products:
CloudGen Firewall (traditional offering)
SecureEdge (newer SASE-focused solution)
SecureEdge replaces Barracuda’s previous alternative option, CloudGen WAN, which was a SASE solution tightly integrated with Microsoft Azure. Given this, both of the current solutions offer native Azure integrations, working directly with Azure service fabric to manage User Defined Routes and monitor internet protocol (IP) forwarding settings and deployment directly through the Azure Marketplace.
This makes Barracuda’s offerings well-suited for their target audience, which primarily focuses on smaller enterprise and SMB customers, who typically make use of Azure for other business operations, due to the benefits related to reduced costs and improved application performance.
Whilst this does make things easier for businesses using Azure, it should be noted that Barracuda’s solution do offer limited integration with third-party SSE vendors, should your business want to leverage external security resources.
| Feature | Vendor/Provider Support |
|---|---|
| Centralised Cloud Management | Barracuda's Azure-native offering provides real-time visibility and unified control of the network. |
| Support for Multiple Connection Types | Supports a range of transport types, including broadband, LTE, MPLS and satellite connections. By monitoring metrics such as bandwidth and latency, Barracuda utilises performance-based transport selection to prevent downtime. |
| Integrated Security Features | Provides security features, such as Next-Generation Firewall (NGFW) capabilities, Zero Trust Network Access (ZTNA) and compliance tools. |
| Quality of Service (QoS) | Barracuda offers more-limited QoS settings, including dynamic adjustments and prioritisation of specific protocols.These are achieved with WAN optimisation, deep packet inspection and application-specific policies to reduce latency and increase throughput |
| Scalability and Flexibility | Barracuda SD-WAN is designed to scale, accommodating large enterprise deployments, quickly adding new branches and supporting hybrid workforces. This is achieved through zero-touch provisioning and automated deployments, reducing deployment time and lower |
| Cloud and Multi-Cloud Integration | Connects with cloud platforms and supports multi-cloud environments through features such as direct cloud on-ramps. |
| Resilience and Failover Capabilities | Provides failover mechanisms, sub-second failover, multi-path redundancy and link health monitoring. |
| Cost Efficiency | Leverages low-cost broadband connections and consolidates network functions, reducing reliance on expensive MPLS circuits. |
| Analytics and Reporting | Barracuda provides analytics tools and reporting capabilities, offering AI-driven insights, historical trends and detailed application-level visibility. |
| Programmatic APIs | Barracuda WAF and WAF-as-a-Service are fully configurable using REST APIs, with CloudGen WAF APIs publicly available on GitHub. Also offers integrations with Microsoft Azure vWAN for zero-touch deployment and support for Office 365 policies. |
| Support for Cellular Connectivity | Barracuda's solution supports LTE and 5G connectivity, enabling redundancy and remote use cases. |
| AI Integrations | Utilises AI for predictive analytics and automated policy adjustments. |
| Deployment Models Supported | Barracuda offers on-premises, hybrid and fully cloud-based SD-WAN options. |
| Compliance and Regulatory Certifications | Offers certifications such as ISO 27001 and SOC 2. |
| Support and Training Options | Barracuda provides 24/7 helpdesks, dedicated account managers and online training resources. |
| Target-Market Customers | Barracuda's SD-WAN solutions are suited for various industries including finance, healthcare, retail, manufacturing, education, government, technology, transportation, energy and telecommunications. |
Aryaka

Previous Visionary North America Latin America Europe Middle East & Africa Asia-Pacific Managed Services
Aryaka launched its SD-WAN service offering in September 2010, which was revamped with their SmartServices platform in 2019. This platform delivers SD-WAN as a service over a private network, rather than requiring customers to build their own solutions, which has become a key differentiator in the market when compared to their competitors.
Arguably Aryaka’s best feature is their global private network, which includes over 30 Service Points of Presence (PoPs) across six continents. This not only provides businesses with, in our opinion, the best connectivity within the China and Asia region, but these points are also strategically located near business hubs and major cloud service providers, including AWS, Azure, Google Cloud, Oracle Cloud and Alibaba Cloud.
These capabilities have led Aryaka to establish itself as the largest pure-play SD-WAN market leader with an 18% revenue share, maintaining a 6% lead over the likes of Cisco.
| Feature | Vendor/Provider Support |
|---|---|
| Centralised Cloud Management | Aryaka’s SD-WAN is managed via its SmartManage platform, offering real-time visibility and centralised policy control. |
| Support for Multiple Connection Types | Supports broadband, MPLS, LTE and satellite connections with optimised traffic steering via Aryaka’s proprietary SmartConnect service, which dynamically selects paths using real-time monitoring and application-aware routing. |
| Integrated Security Features | Includes built-in security such as a Next-Generation Firewall (NGFW), Secure Web Gateway (SWG) and Zero Trust Network Access (ZTNA), whilst also supporting multiple VPNs per WAN connection for data segregation. |
| Quality of Service (QoS) | Provides QoS with dynamic bandwidth allocation and prioritisation, with WAN optimisation, application acceleration and deep packet inspection. |
| Scalability and Flexibility | Designed for enterprises of all sizes, Aryaka’s SD-WAN can scale to support large global deployments, especially those operating in the China region. Supports zero-touch provisioning (ZTP) and integrations for existing MPLS and security environments. |
| Cloud and Multi-Cloud Integration | Direct cloud connectivity with AWS, Azure, and Google Cloud via Aryaka’s private backbone, supporting multi-cloud use cases. |
| Resilience and Failover Capabilities | Aryaka provides sub-second failover, multi-path redundancy and continuous link health monitoring. |
| Cost Efficiency | Reduces reliance on MPLS by leveraging low-cost broadband, while Aryaka’s private backbone ensures performance. Provides predictable costs. |
| Analytics and Reporting | Offers AI-driven network insights, historical performance data and detailed application-level visibility. |
| Programmatic APIs | Provides REST APIs for automation and integrations with other systems and security platforms. |
| Support for Cellular Connectivity | Supports LTE and 5G for backup and primary connectivity in remote locations. |
| AI Integrations | Leverages AI-driven insights for routing, AI-automated policy adjustments and self-healing network capabilities to prevent downtime. |
| Deployment Models Supported | Available as fully managed cloud-based SD-WAN, hybrid or on-premises solutions. |
| Compliance and Regulatory Certifications | Certified for ISO 27001, SOC 2 and GDPR compliance. |
| Support and Training Options | Offers 24/7 global support, dedicated account managers and online training resources. |
| Target-Market Customers | Focuses on Finance, Healthcare, Retail, Manufacturing, Education, Government, Technology, Transportation, Energy and Telecommunications markets. |
Cato Networks

Leader North America Latin America Europe Middle East & Africa Asia-Pacific Managed Services
Whilst only moving up from a Challenger to a Leader within the Gartner SD-WAN magic quadrant in 2024, Cato Network’s SD-WAN solutions have frequently set trends for the entire market.
The company initially launched its SD-WAN service in 2017, however in 2018 introduced the first cloud-based threat hunting system across the SD-WAN market, with one of the key benefits being that it didn’t require dedicated data collection infrastructure. This leveraged zero-footprint data aggregation and machine learning algorithms for threat detection.
Following this, in 2020, Cato Networks were awarded the INTERNET TELEPHONY SD-WAN Product of the Year Award, recognising their achievement as the only SASE platform to converge SD-WAN and security into a global, cloud-native platform.
But these haven’t been the only milestones to note, with Cato also being recognised for creating the industry's first identity-aware routing engine, as well as, in February 2025, becoming the first SASE platform to achieve PCI DSS v4.0 compliance.
| Feature | Vendor/Provider Support |
|---|---|
| Centralised Cloud Management | Cato Networks offers a fully cloud-native management application that provides real-time visibility, analytics and policy enforcement. |
| Support for Multiple Connection Types | Supports broadband, LTE, MPLS and satellite. Uses AI-driven analytics and continuous traffic monitoring to dynamically select the best path for applications, whilst multi-path capabilities ensure failover in the event of link downtime. |
| Integrated Security Features | Built-in security includes Next-Generation Firewall (NGFW), Secure Web Gateway (SWG), Zero Trust Network Access (ZTNA) and Advanced Threat Protection (ATP). Security is fully converged into the SD-WAN fabric, alongside support for multiple VPNs on a singl |
| Quality of Service (QoS) | Uses a range of QoS techniques, such as dynamic bandwidth allocation, application-aware routing, WAN optimisation and deep packet inspection, with significant benefits seen by cloud and SaaS applications. |
| Scalability and Flexibility | Cloud-native architecture enables increased scalability when compared to physical, with new sites added more quickly through zero-touch provisioning with automated deployments and supporting both hybrid workforces and global operations. |
| Cloud and Multi-Cloud Integration | Direct cloud on-ramps to AWS, Azure and Google Cloud, amongst other major platforms. Uses a private backbone for optimised multi-cloud access. |
| Resilience and Failover Capabilities | Offers sub-second failover with real-time link health monitoring and multi-path redundancy to provide high availability. |
| Cost Efficiency | Reduces reliance on expensive MPLS by leveraging low-cost broadband and consolidating security and networking functions into a single platform. |
| Analytics and Reporting | Provides AI-driven analytics provide real-time network insights, historical trend analysis and detailed application-level visibility. |
| Programmatic APIs | Offers open APIs for automation and custom integrations. |
| Support for Cellular Connectivity | Fully supports LTE and 5G for primary or backup connectivity. |
| AI Integrations | Uses AI for predictive analytics, automated policy adjustments and self-healing capabilities. |
| Deployment Models Supported | Offers cloud-native, hybrid and on-premises deployment models. |
| Compliance and Regulatory Certifications | Holds ISO 27001, SOC 2, PCI DSS and HIPAA certifications. |
| Support and Training Options | Cato provides 24/7 support, dedicated account managers, online training and extensive documentation. |
| Target-Market Customers | Market focus includes Finance, Healthcare, Retail, Manufacturing, Education, Government, Technology, Transportation, Energy and Telecommunications sectors. |
Ecessa

Unranked North America Europe Asia-Pacific SMBs
Ecessa, who were acquired by OneNet Global in July 2023, differentiates itself from many of its competitors through its deployment guarantee and phased implementation approach, which has helped customers achieve faster deployment times compared to other solutions.
They offer multiple product tiers:
Ecessa Edge: Entry-level solution for small businesses, introducing basic load balancing and in-call failover
PowerLink: Mid-tier solution focusing on WAN link management with VPN and SIP functionality
WANworX: Enterprise-grade solution offering complete SD-WAN features including automatic failover, active/active bandwidth usage, QoS and support for bandwidths up to 20Gbps.
| Feature | Vendor/Provider Support |
|---|---|
| Centralised Cloud Management | Ecessa EdgeView, a cloud-based dashboard, provides real-time visibility, traffic monitoring and firmware upgrades. |
| Support for Multiple Connection Types | Ecessa supports broadband, MPLS, LTE and satellite links, using link aggregation and monitoring to optimise traffic flow, automatically redirecting traffic based on link performance. |
| Integrated Security Features | Ecessa SD-WAN integrates basic firewall capabilities and supports third-party security tools. While not NGFW-native, it complements existing security frameworks and can be used alongside other solutions to meet compliance needs. Ecessa supports multiple V |
| Quality of Service (QoS) | Offers configurable QoS settings to prioritise applications via deep packet inspection and policy-based routing to steer traffic according to application type. |
| Scalability and Flexibility | Ecessa can support from small businesses to distributed enterprises and adapts well to hybrid workforces. Supports zero-touch provisioning and remote firmware updates via EdgeView. |
| Cloud and Multi-Cloud Integration | Offers cloud-optimised routing and integration with platforms such as AWS and Azure, with direct cloud connections and policy controls to enable multi-cloud access. |
| Resilience and Failover Capabilities | Sub-second failover, active/active or active/passive configurations, and continuous link health checks ensure always-on connectivity. |
| Cost Efficiency | Reduces costs by leveraging broadband and eliminating MPLS dependency. |
| Analytics and Reporting | EdgeView includes performance monitoring, historical trend analysis and real-time alerts. |
| Programmatic APIs | Offers APIs for integration with third-party systems and custom automation workflows. |
| Support for Cellular Connectivity | Provides LTE/5G support via compatible hardware. Enables failover or primary connectivity in remote locations or mobile deployments. |
| AI Integrations | N/A |
| Deployment Models Supported | Supports on-premises and hybrid models. |
| Compliance and Regulatory Certifications | While Ecessa conforms to industry best practices, Ecessa relies on partner security integrations for compliance. |
| Support and Training Options | Ecessa offers 24/7 technical support, onboarding assistance and online knowledge base, whilst customised training is available through service agreements. |
| Target-Market Customers | Focuses on Healthcare, Education, Retail, Manufacturing, Finance, Government and Technology sectors. |
Adaptiv Networks

Unranked North America Europe SMBs
Elfiq SD-WAN, now owned by Adaptiv Networks, is recognised as being one of the first pioneers in SD-WAN technology. Initially, Elfiq produced link balancing solutions, which made them well-suited to branch out into the SD-WAN market due to their prior expertise in network improvements.
Today, Elfiq SD-WAN showcases these network capabilities, supporting data centres and organisations that require high bandwidth capabilities, offering them with up to 20Gbps and edge deployments up to 1Gbps with support for 4G/5G links, broadband and MPLS circuits
However, Elfiq SD-WAN isn’t the only SD-WAN solution offered by Adaptiv Networks, who also offer Enterprise Connect - a solution designed for distributed enterprises, which has a heavy focus on user experience improvement across cloud services.
These two SD-WAN solutions therefore compliment Adaptiv Network’s wider portfolio, which includes:
Business Connect: A cloud-based connectivity solution
Cloud-managed SASE (Secure Access Service Edge) solutions
| Feature | Vendor/Provider Support |
|---|---|
| Centralised Cloud Management | Adaptiv offers their own cloud-based management platform with real-time visibility and policy control. |
| Support for Multiple Connection Types | Supports broadband, LTE, MPLS and satellite connections. Uses application-aware routing, automatic path selection, traffic steering and real-time performance metrics. |
| Integrated Security Features | Built-in firewall and support for secure VPN tunnels. Whilst Adaptiv doesn't offer a full NGFW, the solution integrates with third-party security tools and complies with security best practices. Supports multiple VPNs over a single WAN connection to segme |
| Quality of Service (QoS) | Enables traffic prioritisation for critical applications, with dynamic QoS adjustments based on real-time conditions to maintain performance. Supports granular traffic steering based on business policies and incorporates traffic shaping and deep packet in |
| Scalability and Flexibility | Suited for SMEs and distributed enterprises, offering features such as Zero-touch provisioning. Interoperates with existing MPLS, firewalls and third-party systems, reducing the complexity of migrations. |
| Cloud and Multi-Cloud Integration | Offers direct cloud on-ramps to major platforms including both AWS and Microsoft Azure. |
| Resilience and Failover Capabilities | Provides sub-second failover and multi-path redundancy ensure high availability, with link health monitoring for proactive rerouting. |
| Cost Efficiency | Leverages low-cost broadband and eliminates the need for costly MPLS in many use cases. Simple licensing reduces budgeting complexity. |
| Analytics and Reporting | Provides a cloud-based analytics dashboard with real-time and historical data, enabling bandwidth planning and traffic optimisation. |
| Programmatic APIs | Offers APIs for integration with external systems. |
| Support for Cellular Connectivity | Built-in support for LTE and 5G provides redundancy and is ideal for remote, mobile or temporary deployments. |
| AI Integrations | Uses AI for dynamic path optimisation and predictive performance analytics to reduce manual intervention. |
| Deployment Models Supported | Available as cloud-managed or hybrid deployment. |
| Compliance and Regulatory Certifications | Complies to industry best practices and supports compliance with standards such as ISO 27001 and SOC 2. |
| Support and Training Options | Offers businesses with 24/7 technical support, onboarding assistance and an online knowledge base with training materials. |
| Target-Market Customers | Primarily focuses on Finance, Healthcare, Retail, Education, Government and Transportation markets. |
Extreme Networks

Unranked North America Latin America Europe Middle East & Africa Asia-Pacific Large Enterprises
Extreme Networks have a strong focus on machine learning and artificial intelligence, and their products reflect this. They believe in making ML/AI understandable, yet still offering all the capabilities to allow faster, smarter and more efficient harnessing of data. This is done in a transparent way allowing the customer to see, verify and trust the machine’s recommendations. In 2019 they acquired Aerohive Networks, who were an emerging cloud-managed networking company.
Extreme has grown to be the biggest competitor to Cisco’s Meraki and currently hold a 10% market share in both revenue and devices managed in the cloud-managed space.
From global enterprises to small town high schools, Extreme caters to all sizes of networks allowing customers to better understand their users and develop their organisation. With over 50,000 customers all possessing the same goal of customer-driven networking. ExtremeCloudIQ is their powerful SaaS cloud-based management platform which allows users to analyse and maintain their network. Customers have a choice of four plans, each more advanced and feature heavy than the last.
| Feature | Vendor/Provider Support |
|---|---|
| Centralised Cloud Management | ExtremeCloud, the cloud-based management platform, provides real-time visibility, centralised policy control and unified orchestration. |
| Support for Multiple Connection Types | Supports broadband, MPLS, LTE and satellite connectivity. Utilises dynamic traffic steering, application-aware routing and performance metrics to optimise path selection. |
| Integrated Security Features | Built-in security includes stateful firewalling, IDS/IPS, and integration with third-party security platforms. Offers Zero Trust support and centralised policy enforcement, supporting multiple VPNs for multi-tenant and departmental use cases. |
| Quality of Service (QoS) | Offers granular QoS settings, WAN optimisation, deep packet inspection and application-specific traffic shaping to enable prioritisation of business-critical applications. |
| Scalability and Flexibility | Scales efficiently from small sites to large enterprises. Supports expansion and adapts to hybrid workforces, with automated onboarding and policy inheritance. Enables zero-touch provisioning and centralised configuration via ExtremeCloud. |
| Cloud and Multi-Cloud Integration | Offers direct cloud on-ramps and optimised routing for multi-cloud environments, whilst integrating with AWS, Azure and other major cloud platforms. |
| Resilience and Failover Capabilities | Supports sub-second failover with path redundancy and link health monitoring to maintain uptime. |
| Cost Efficiency | Reduces dependency on MPLS through broadband-first designs and consolidated network functions. |
| Analytics and Reporting | Provides detailed application-level analytics and network health reports. AI-powered insights assist in identifying issues proactively and optimising performance. |
| Programmatic APIs | Offers open APIs for integration with third-party systems and enables custom automation workflows. |
| Support for Cellular Connectivity | Full support for LTE and 5G connections for primary or backup use. |
| AI Integrations | AI is used for traffic pattern recognition, anomaly detection and automated policy recommendations. |
| Deployment Models Supported | Available as on-premises, cloud-based or hybrid deployments. Flexible options accommodate both legacy infrastructures and cloud-first strategies. |
| Compliance and Regulatory Certifications | Holds certifications such as ISO 27001 and SOC 2. |
| Support and Training Options | Offers businesses with 24/7 global support, dedicated technical account managers and a library of online training and documentation resources. |
| Target-Market Customers | Focuses on Finance, Healthcare, Retail, Manufacturing, Education, Government, Technology, Transportation, Energy and Telecommunications markets. |
FatPipe Networks

Previous Niche Player North America Europe Asia-Pacific Large Enterprises
FatPipe Networks have been acknowledged as pioneering the concept of SD-WAN, inventing the software-defined path selection that has become so integral to SD-WAN and seamless failover technologies, even before SD-WAN became widespread industry terminology.
Developing and providing WAN traffic solutions for over 20 years, FatPipe now deploy their SD-WAN solution across six continents and their solutions can manage up to 16 different network links, as well as offering sub-second failover capabilities.
Whilst FatPipe are no longer recognised by the Gartner Magic Quadrant for SD-WAN, they were formerly recognised as a niche player and are positioned as the Leader in the SPARK Matrix for SD-WAN by Quadrant Knowledge Solutions.
One of the other key benefits of FatPipe SD-WAN is its direct integration with Microsoft Azure cloud, which can be largely beneficial for businesses that already leverage Microsoft Azure’s services. Further to this, FatPipe offers enterprises with the ability to deploy as on-premises, cloud or leverage a hybrid solution.
| Feature | Vendor/Provider Support |
|---|---|
| Centralised Cloud Management | FatPipe offers a centralised management console called Orchestrator, providing real-time visibility and unified control for network functions. |
| Support for Multiple Connection Types | FatPipe supports broadband, MPLS, LTE and satellite links, allowing dynamic use of multiple WAN types. FatPipe’s SmartLink technology enables application-aware routing and dynamic path control, ensuring optimal delivery and failover. |
| Integrated Security Features | FatPipe includes a built-in firewall and supports integration with third-party security tools. Whilst not a full NGFW, FatPipe SD-WAN offers encryption, DDoS protection and compliance support for regulated industries, as well as supporting multiple encryp |
| Quality of Service (QoS) | Offers granular QoS controls with real-time adjustments, using techniques such as deep packet inspection, compression, WAN optimisation and packet duplication. |
| Scalability and Flexibility | Supports small branch rollouts to large multi-site enterprises. Offers zero-touch provisioning, centralised policy management, configuration templates and automation, all of which reduce administration complexity. |
| Cloud and Multi-Cloud Integration | FatPipe supports direct cloud access and is compatible with AWS, Azure and Google Cloud. |
| Resilience and Failover Capabilities | Offers sub-second failover and multi-path resilience with active-active link usage. |
| Cost Efficiency | Reduces MPLS dependency by using broadband links while maintaining performance and uptime. Consolidates multiple functions, reducing both CAPEX and OPEX. |
| Analytics and Reporting | Includes performance dashboards and historical analytics for bandwidth, traffic patterns and application use. |
| Programmatic APIs | Offers REST APIs for automation and integration with existing systems. |
| Support for Cellular Connectivity | Supports LTE and 5G connections for backup or primary use, ideal for remote sites or mobile operations. |
| AI Integrations | Limited AI features. Some automation is available for path selection and traffic management. |
| Deployment Models Supported | Available in on-premises, hybrid and cloud-hosted deployments. |
| Compliance and Regulatory Certifications | Supports compliance efforts and offers features suitable for meeting standards like HIPAA and PCI DSS. |
| Support and Training Options | Offers 24/7 support, professional services and online training resources. Customers also have access to detailed documentation and configuration assistance. |
| Target-Market Customers | Designed for Finance, Healthcare, Retail, Manufacturing, Education, Government, Technology, Transportation, Energy and Telecommunications markets. |
Forcepoint

Niche Player North America Europe Security
With a strong focus on security-driven SD-WAN, Forcepoint not only offers businesses with the ability to protect their network but also allows management of up to 6,000 physical or virtual engines through a single management console. This means that Forcepoint can cater for small, medium and large enterprises.
Forcepoint’s security capabilities can be extended via their SASE offering, which provides options for integrated data protection services. Forcepoint offers security for remote users via a cloud-delivered security gateway, Data Loss Prevention (DLP), and private access to applications. These DLP capabilities are considered industry-leading, with insider threat analytics helping to deliver high detection rates with low false positives. Further to this, Forcepoint offers the industry’s first commercial deployment of Messaging Layer Security (MLS).
Due to these capabilities, Forcepoint SD-WAN recently received a "AAA" rating from CyberRatings.org.
| Feature | Vendor/Provider Support |
|---|---|
| Centralised Cloud Management | Forcepoint offers a unified cloud-based management system through its Security Management Centre (SMC), enabling real-time visibility, policy control and network-wide orchestration. |
| Support for Multiple Connection Types | Supports MPLS, broadband, LTE, and satellite links. Forcepoint provides application-aware routing with intelligent path selection based on real-time analytics and path monitoring. |
| Integrated Security Features | SD-WAN is integrated with Forcepoint’s NGFW and built-in threat protection, including IPS, SSL inspection, and Zero Trust Network Access. Multiple VPNs can be run over a single WAN connection, improving segmentation and resilience. |
| Quality of Service (QoS) | Offers granular QoS controls to prioritise latency-sensitive applications via deep packet inspection and custom application policies. |
| Scalability and Flexibility | Designed to scale from small branches to large global networks. Easily supports hybrid workforces, whilst policy-driven traffic routing supports complex business needs and regulatory rules. Supports zero-touch provisioning and automated deployments and in |
| Cloud and Multi-Cloud Integration | Provides direct cloud access and optimised connectivity to major cloud providers, utilising intelligent routing and private backbone options. |
| Resilience and Failover Capabilities | Offers features including sub-second failover, active-active paths and continuous link health monitoring. |
| Cost Efficiency | Reduces costs by utilising cheaper broadband links over MPLS, consolidating firewall and SD-WAN functions, as well as offering simplified licensing. |
| Analytics and Reporting | Built-in analytics provide application-level visibility, usage trends and real-time alerts. |
| Programmatic APIs | Offers APIs for integration with SIEMs, automation platforms and third-party management tools. |
| Support for Cellular Connectivity | Includes full LTE/5G support for backup or primary links, ideal for remote, mobile or temporary locations. |
| AI Integrations | Leverages AI for predictive threat detection, dynamic policy tuning and network self-healing. |
| Deployment Models Supported | Available as physical, virtual, cloud-hosted or hybrid deployments. |
| Compliance and Regulatory Certifications | Certified for ISO 27001, SOC 2 and GDPR compliance. |
| Support and Training Options | Offers 24/7 support, online knowledge base and role-based training. Includes access to Forcepoint support engineers and service onboarding. |
| Target-Market Customers | Targets Finance, Healthcare, Retail, Government, Education, Technology, Manufacturing and Telecommunications. |
Mushroom Networks

Unranked Latin America Europe Middle East & Africa Multi-tenancy Multi-deployment
Founded in 2004, Mushroom Networks was a spin-off from the University of California, San Diego (UCSD). Mushroom Networks initially focused on community networks and WiFi signal aggregation before specialising in broadband bonding technology, all of which form the foundations of SD-WAN’s core networking capabilities.
By incorporating their patented Broadband Bonding® technology into their SD-WAN solution, Mushroom Networks garnered early recognition, earning them the position of 2016 SD-WAN Company of the Year by Quadrant Knowledge Solutions, however the company has not been ranked by Gartner’s Magic Quadrant.
In July 2017, the company launched its autopilot SD-WAN service for partners, which enables channel partners and service providers to build custom WANs for their end customers. The service provides access to application-centric overlay tunnels and virtual network functions (VNFs) that automate client networks.
| Feature | Vendor/Provider Support |
|---|---|
| Centralised Cloud Management | Offers centralised management portal with real-time visibility and unified control. |
| Support for Multiple Connection Types | Supports broadband, LTE/5G, MPLS and satellite links, which is aggregated with Mushroom Network's patented overlay bonding technology, leveraging flow-aware routing, to dynamically optimise traffic across these paths. |
| Integrated Security Features | Includes firewall capabilities and integrates with third-party security platforms. Supports multiple VPNs per WAN link to segment traffic securely. |
| Quality of Service (QoS) | Offers traffic shaping, flow control, error correction and adaptive routing for prioritising essential applications. |
| Scalability and Flexibility | Scales from small branches to large enterprises, offering Zero-touch provisioning, supported via plug-and-play deployment. |
| Cloud and Multi-Cloud Integration | Provides direct cloud connectivity with optimised routing for services such as AWS, Azure and Google Cloud, whilst supporting multi-cloud use with minimal latency. |
| Resilience and Failover Capabilities | Offers sub-second failover through link bonding. Continuity is maintained even during complete WAN link failure. |
| Cost Efficiency | Reduces dependency on MPLS by leveraging multiple lower-cost broadband links. Consolidates functions to lower total infrastructure costs. |
| Analytics and Reporting | Provides real-time and historical traffic analytics. Detailed reports include application usage, link health and bandwidth consumption. |
| Programmatic APIs | Offers APIs for integration with external systems. |
| Support for Cellular Connectivity | Built-in support for LTE/5G enables deployment in remote areas or as backup for primary links. |
| AI Integrations | AI is used to detect anomalies, auto-tune performance settings and assist in policy adjustments. |
| Deployment Models Supported | Available as on-premises, hybrid or fully cloud-managed. |
| Compliance and Regulatory Certifications | N/A |
| Support and Training Options | Provides 24/7 technical support, online documentation and onboarding assistance. |
| Target-Market Customers | Focuses on Technology, Education, Healthcare, Retail and Government sectors. |
Nokia (Nuage Networks)

Niche Player Europe Middle East & Africa Asia-Pacific Managed Services
Nuage Networks are a division of Nokia, who initially developed SDN (Software-Defined Networking) solutions for private data centres, specifically designed to extend traditional network boundaries. With a focus on automated integration of multi-cloud environments, Nuage Networks' SD-WAN solution is ideal for a wide range of businesses that need the ability to quickly onboard new cloud platforms.
Nuage Networks' SD-WAN solution offers businesses with support for direct Software-as-a-Service (SaaS) optimisations for applications, such as Office365 and Salesforce. Further to this, they have introduced SD-WAN 2.0 technology, which offers end-to-end network governance across multi-cloud environments, security features including microsegmentation and real-time threat detection and response capabilities.
With 70 certified managed service providers and 700+ enterprise customers, Nuage Networks have a long history of providing managed SD-WAN services for a range of business requirements.
| Feature | Vendor/Provider Support |
|---|---|
| Centralised Cloud Management | Offers a unified SD-WAN management platform via the Nuage Networks Virtualised Network Services (VNS) Portal. |
| Support for Multiple Connection Types | Supports broadband, LTE, MPLS and satellite links, leveraging real-time analytics to optimise traffic across hybrid WAN connections. |
| Integrated Security Features | Includes built-in stateful firewall, micro-segmentation, and integration with third-party security solutions. Supports Zero Trust models with role-based access and policy enforcement. Supports multiple VPNs per WAN link, aiding multi-tenant and department |
| Quality of Service (QoS) | Enables granular QoS settings with dynamic adjustments based on application and network conditions. Leverages deep packet inspection and application-aware policies to improve performance. |
| Scalability and Flexibility | Highly scalable architecture supporting thousands of sites, including cloud-first and hybrid environments. Provides zero-touch provisioning and centralised policy enforcement. |
| Cloud and Multi-Cloud Integration | Offers integrations with major cloud providers including AWS, Azure and Google Cloud, supporting direct cloud on-ramps and private backbone routing. |
| Resilience and Failover Capabilities | Delivers sub-second failover with intelligent link monitoring and multi-path redundancy. |
| Cost Efficiency | Reduces costs by enabling the use of lower-cost broadband and consolidating multiple network functions. |
| Analytics and Reporting | Provides detailed analytics through the VNS portal, including real-time and historical views, application visibility and link utilisation metrics. |
| Programmatic APIs | Offers REST APIs for integration with IT operations, orchestration tools and third-party systems. |
| Support for Cellular Connectivity | Supports LTE and 5G connections for primary or backup links, improving redundancy and allowing deployment in mobile or remote sites. |
| AI Integrations | Utilises both AI and machine learning for anomaly detection, predictive analytics and automated policy optimisation. |
| Deployment Models Supported | Supports on-premises, hybrid and fully cloud-hosted SD-WAN deployments. |
| Compliance and Regulatory Certifications | Holds certifications including ISO 27001 and SOC 2. |
| Support and Training Options | Offers 24/7 global support, dedicated technical account managers, online documentation and training resources. |
| Target-Market Customers | Targets Finance, Healthcare, Retail, Manufacturing, Education, Government, Technology, Transportation, Energy and Telecommunications. |
Oracle

Unranked North America Latin America Europe Middle East & Africa Asia-Pacific Enterprise-Grade Networking
Entering the SD-WAN market through its acquisition of Talari Networks in November 2018, Oracle’s SD-WAN solution is especially well-suited for those already using the Oracle Cloud Infrastructure.
Further to this, Oracle SD-WAN is ideal for enterprises and large organisations with multiple geographically dispersed locations. Oracle SD-WAN enables these organisations to utilise real time applications, such as VoIP or desktop virtualisation, which can be essential for daily operations. The offering is particularly beneficial for those with multiple WAN links, looking to add bandwidth and/or cloud connectivity whilst retaining a high Quality of Experience (QoE).
| Feature | Vendor/Provider Support |
|---|---|
| Centralised Cloud Management | Oracle offers a centralised cloud-based management platform that provides real-time visibility, policy control and network analytics through its Oracle SD-WAN Orchestrator. |
| Support for Multiple Connection Types | Oracle SD-WAN supports MPLS, broadband, LTE and satellite. It uses real-time path monitoring and adaptive policies, with dynamic path selection based on application performance and real-time conditions. |
| Integrated Security Features | Oracle’s SD-WAN integrates with third-party security platforms but does not include native NGFW or ZTNA, instead focusing on other elements of security, such as segmentation, encryption and traffic isolation. These capabilities are best-showcased by Oracl |
| Quality of Service (QoS) | Oracle offers granular QoS settings, with deep packet inspection and application-specific policies to optimise traffic routing. |
| Scalability and Flexibility | Oracle’s SD-WAN is designed for scalable deployments across large, distributed enterprises. It supports thousands of sites with consistent policy enforcement and zero-touch provisioning. |
| Cloud and Multi-Cloud Integration | Oracle provides direct cloud integration, especially with Oracle Cloud Infrastructure (OCI), offering private on-ramps and supporting multi-cloud strategies. |
| Resilience and Failover Capabilities | Oracle SD-WAN delivers sub-second failover, multipath redundancy and real-time link health analysis. |
| Cost Efficiency | Customers benefit from fewer hardware requirements and reduced transport costs, where costly MPLS can be replaced by cheaper broadband links. |
| Analytics and Reporting | Oracle provides in-depth analytics, including real-time and historical performance metrics. |
| Programmatic APIs | Oracle offers APIs for integration with third-party platforms, enabling automation of network tasks. |
| Support for Cellular Connectivity | Oracle SD-WAN supports LTE and 5G connectivity through compatible devices. |
| AI Integrations | Oracle uses machine learning for dynamic path selection and application performance monitoring. AI-driven analytics help detect anomalies, adjust policies and prevent degradation proactively. |
| Deployment Models Supported | Oracle supports on-premises, cloud-hosted and hybrid deployment models. |
| Compliance and Regulatory Certifications | Oracle holds certifications including ISO 27001, SOC 2 and PCI DSS. |
| Support and Training Options | Provides 24/7 technical support, dedicated account teams, an extensive knowledge base and online training resources. |
| Target-Market Customers | Designed for Finance, Healthcare, Retail, Manufacturing, Education, Government, Technology, Transportation, Energy and Telecommunications markets. |
Riverbed Technology

Unranked North America Latin America Europe Middle East & Africa Asia-Pacific Large Enterprises
Riverbed began as a leader in WAN optimisation with its Steelhead product line, establishing itself as the market standard for over a decade, which helped them to easily transition into the SD-WAN market, using their expertise to improve network performance. This was assisted by Riverbed’s acquisition of Ocedo in 2016, a German SD-WAN provider, to accelerate their entry into the market.
In April 2016, Riverbed launched SteelConnect as an early access offering and SteelConnect 2.0 became the first production version, which was further improved via Riverbed acquiring Xirrus and using their capabilities to improve the WiFi features of their SD-WAN solution.
In October 2019, Riverbed announced SteelConnect EX, which shifted the SD-WAN solution to a more large-scale and enterprise market focus, with industry-leading application acceleration that, BusinessWire reports, boosts performance up to 33x for cloud, SaaS, and on-premises applications.
| Feature | Vendor/Provider Support |
|---|---|
| Centralised Cloud Management | Riverbed offers a unified management platform, SteelConnect Manager, that provides real-time visibility and policy control. |
| Support for Multiple Connection Types | Supports broadband, MPLS, LTE and satellite links, with dynamic path control to switch between types. |
| Integrated Security Features | Includes built-in firewall, segmentation, and integration with third-party security tools. |
| Quality of Service (QoS) | Riverbed leverages WAN optimisation, deep packet inspection and application-aware policies to enable granular QoS controls to prioritise latency-sensitive traffic |
| Scalability and Flexibility | Easily scales from SMBs to global enterprises, supporting branch expansion and hybrid workforces. Offers zero-touch provisioning and policy-based orchestration. |
| Cloud and Multi-Cloud Integration | Integrates with AWS, Azure and other major clouds, with direct cloud access capabilities and use of a private backbone. |
| Resilience and Failover Capabilities | Provides sub-second failover, multipath redundancy and link health monitoring. |
| Cost Efficiency | Enables use of lower-cost broadband links and reduces dependency on MPLS. Consolidated management tools lower operational expenses. |
| Analytics and Reporting | Built-in analytics offer traffic visibility, usage trends and application insights |
| Programmatic APIs | Offers APIs for automation, orchestration and integration with third-party systems. |
| Support for Cellular Connectivity | Supports LTE and 5G as primary or backup WAN paths. |
| AI Integrations | Uses AI/ML to improve traffic routing, detect anomalies and automate policy updates. |
| Deployment Models Supported | Supports on-premises, hybrid and cloud-based deployments. |
| Compliance and Regulatory Certifications | Offers support for key compliance standards including ISO 27001 and SOC 2. |
| Support and Training Options | Provides 24/7 global support, knowledge base and online training. For enterprise customers, dedicated support plans are available. |
| Target-Market Customers | Focuses on customers from Finance, Healthcare, Retail, Manufacturing, Government, Education, Technology, Energy and Telecommunications markets. |
SonicWall

Unranked North America Latin America Europe Middle East & Africa Asia-Pacific SMBs
With an original focus on Apple networking products in 1991, SonicWall’s offering began with their firewall and security appliances, which were first introduced in 1997 under the name Interpol before being rebranded. SonicWall differentiates itself by integrating SD-WAN capabilities directly into their firewall appliances, however SonicWall SD-WAN is only supported on these SonicWall firewall devices and is not compatible with third-party VPN solutions.
The SonicWall's SD-WAN solution primarily targets distributed small and medium businesses (SMB) through their TZ series appliances, which offer businesses with integrations to the SonicWall Capture Cloud Platform, released in 2018, which is a security portfolio that combines features such as Advanced Threat Protection, Security Centre analytics/reporting, endpoint protection and email security.
| Feature | Vendor/Provider Support |
|---|---|
| Centralised Cloud Management | SonicWall provides centralised SD-WAN management via its Capture Security Center and Network Security Manager (NSM). |
| Support for Multiple Connection Types | SonicWall SD-WAN supports broadband, LTE, MPLS and satellite links, with performance-based path selection optimising traffic flow between these links. |
| Integrated Security Features | SonicWall offers built-in integrations of their NGFW, threat prevention and Zero Trust features, with support for multiple VPNs per WAN interface. |
| Quality of Service (QoS) | Offers granular QoS controls and application-layer intelligence to optimise throughput and reduce latency, prioritising essential application traffic. |
| Scalability and Flexibility | SonicWall supports scalable deployments from SMBs to large enterprises, with flexible architecture suited to hybrid workforces and growing site counts. For scalability, SonicWall enables zero-touch provisioning via NSM. |
| Cloud and Multi-Cloud Integration | Supports direct cloud on-ramps and optimised routing to major cloud providers including AWS and Azure. |
| Resilience and Failover Capabilities | Offers sub-second failover and path redundancy using link health metrics. |
| Cost Efficiency | Reduces dependency on MPLS by leveraging broadband and LTE links. Consolidates security and networking in one appliance, lowering TCO. |
| Analytics and Reporting | NSM provides detailed traffic analytics, application-level visibility and historical reporting. |
| Programmatic APIs | Offers REST APIs for automation and integration into existing IT systems. |
| Support for Cellular Connectivity | Supports 4G/5G LTE via USB or built-in modems. |
| AI Integrations | Provides AI-powered threat detection and dynamic policy adjustments improve network resilience and performance. |
| Deployment Models Supported | Available in on-premises, cloud-managed and hybrid models. |
| Compliance and Regulatory Certifications | Holds certifications for ISO 27001, SOC 2 and GDPR. |
| Support and Training Options | Offers businesses with 24/7 global support, a customer success programme, online training portals and dedicated account management. |
| Target-Market Customers | Designed for Finance, Healthcare, Retail, Education, Government and Technology markets. |
Sophos

Niche Player North America Latin America Europe Middle East & Africa Asia-Pacific SMBs
Sophos made its debut in the 2024 Gartner Magic Quadrant for SD-WAN as a Niche Player. Catering to 18,000 SD-WAN enterprise customers globally, Sophos are well-known for their competitive pricing and simplified design for smaller businesses.
Sophos SD-WAN primarily focuses on these smaller and midmarket organisations who are prioritising security, which is highlighted by Sophos being recognised for having limited SD-WAN market visibility for enterprise customers.
Whilst Sophos has limited third-party SSE integrations, Sophos currently partners with Zscaler for SSE capabilities and Sophos indicates they are taking a "pragmatic approach" to cloud-hosted security services, implementing SASE services gradually to add value to hybrid networks.
The second-generation XGS Series firewalls now offer integrated SD-WAN features with flexible ISP and WAN connectivity options, 5G connectivity support and Zero-impact failover with support for up to eight gateways.
| Feature | Vendor/Provider Support |
|---|---|
| Centralised Cloud Management | Sophos provides centralised cloud management through Sophos Central. |
| Support for Multiple Connection Types | Supports broadband, LTE/5G, MPLS, and satellite connections, with real-time performance metrics used for automatic link selection. |
| Integrated Security Features | Includes integrated NGFW, IPS, anti-malware and ZTNA, whilst supporting multiple VPNs over a single WAN link. |
| Quality of Service (QoS) | Offers application-aware traffic shaping, deep packet inspection and policy-based routing to optimise performance for SaaS and cloud applications. |
| Scalability and Flexibility | Scales from small sites to large distributed networks and supports hybrid workforce environments. Enables zero-touch provisioning via Sophos Central. |
| Cloud and Multi-Cloud Integration | Provides direct cloud access and optimised routing to major cloud platforms, such as Microsoft Azure. |
| Resilience and Failover Capabilities | Delivers automatic WAN failover with sub-second detection and multi-path redundancy to maintain uptime during link failures. |
| Cost Efficiency | Leverages low-cost broadband links and eliminates the need for multiple point solutions by combining SD-WAN with embedded security, reducing total cost of ownership. |
| Analytics and Reporting | Offers real-time analytics, application-level visibility, and historical reporting via Sophos Central. |
| Programmatic APIs | Provides APIs for integration with third-party platforms and automation tools. |
| Support for Cellular Connectivity | Supports LTE and 5G connections, enabling quicker site deployments and ensuring connectivity in remote locations. |
| AI Integrations | Uses AI-driven threat intelligence and automated policy responses to maintain performance and security |
| Deployment Models Supported | Available as cloud-managed, hybrid or on-premises solutions. |
| Compliance and Regulatory Certifications | Holds certifications such as ISO 27001 and SOC 2, whilst supporting GDPR compliance. |
| Support and Training Options | Offers 24/7 global support, online documentation, training resources and access to Sophos partners for tailored assistance and onboarding. |
| Target-Market Customers | Targets Finance, Healthcare, Retail, Education, Government, Technology, Manufacturing and Telecommunications. |
Turnium

Unranked North America Latin America Europe Middle East & Africa Asia-Pacific Managed Services
Turnium initially operated with two distinct brands - Turnium for managed SD-WAN-as-a-service and Multapplied for white-labelled OEM solutions, which enabled their channel partners to launch managed Network-as-a-Service SD-WAN solutions.
Since then, Turnium's SD-WAN solution now operates as a disaggregated SASE solution, where Turnium provides the networking element whilst partners handle security, management, orchestration and other managed services.
Turnium can be deployed on any x86 device as bare metal, in virtual environments and in containers, supporting public and private clouds while enabling hybrid networks. Further to this, Turnium offers integrations via its open API that enables integration with existing OSS/BSS systems, including platforms such as Check Point, Thales and Console Connect.
| Feature | Vendor/Provider Support |
|---|---|
| Centralised Cloud Management | Turnium offers a centralised management portal via a web-based dashboard, with real-time visibility and unified control across deployments. |
| Support for Multiple Connection Types | Supports broadband, LTE, MPLS and satellite links, with intelligent traffic distribution based on real-time performance. |
| Integrated Security Features | Includes integrated firewall, traffic segmentation and secure tunnelling. While not positioned as a full security stack, it allows integration with third-party security solutions and enables multiple encrypted tunnels per WAN link. |
| Quality of Service (QoS) | Turnium enables traffic shaping, packet-based link aggregation and loss recovery to improve application performance and ensure Quality of Service. |
| Scalability and Flexibility | Built to scale with MSPs and distributed enterprises. Modular design allows easy expansion across branches, remote sites and verticals. Offers zero-touch provisioning via automated deployment tools to assist with this expansion. |
| Cloud and Multi-Cloud Integration | Turnium can be deployed in public and private cloud environments, however lacks direct cloud on-ramps. |
| Resilience and Failover Capabilities | Offers sub-second failover, multi-path redundancy and continuous link health checks. |
| Cost Efficiency | Reduces costs by using low-cost broadband and virtualising WAN functions. |
| Analytics and Reporting | Provides real-time traffic monitoring and usage reports. Enables visibility into application behaviour, link performance and historical trends. |
| Programmatic APIs | Offers APIs for integration with billing, provisioning and monitoring platforms. Facilitates automation and multi-tenant management for service providers. |
| Support for Cellular Connectivity | Supports LTE and 5G for primary or backup connectivity. |
| AI Integrations | N/A |
| Deployment Models Supported | Available as on-premises, virtual and cloud-hosted solutions. |
| Compliance and Regulatory Certifications | Supports compliance with ISO 27001. |
| Support and Training Options | Provides 24/7 support for partners, online documentation and training modules. |
| Target-Market Customers | Focuses on Finance, Healthcare, Retail, Manufacturing, Education, Technology, Telecommunications, Government, Energy and Transportation businesses. |
VMware VeloCloud

Leader North America Latin America Europe Middle East & Africa Asia-Pacific Large Enterprises
VeloCloud was founded in 2012 and since 2017 they have been recognised as an SD-WAN market leader. VeloCloud's position is supported by their extensive global network of over 3,700 gateways across 200+ Points of Presence (PoPs) and their cloud-native architecture. Further to this, it should be noted that VeloCloud leads the global market for unified SASE with a 44% market share.
VMware VeloCloud offers businesses with a global backbone, as well as the ability to implement external security services and multiple cloud environments, which provides their solution with a wider range of functionality than other vendors (albeit at the cost of greater management complexity).
Due to this, VMware SD-WAN provides cloud integration capabilities, which enables easy connectivity for multiple cloud environments. This is backed up by VeloCloud’s asymmetric routing capabilities enabling connections to cloud services using multiple internet service providers (ISPs) or paths.
VMware's improved performance enables businesses to carry out tasks such as VoIP and multiple virtual desktops company wide without traffic degradation affecting operations.
| Feature | Vendor/Provider Support |
|---|---|
| Centralised Cloud Management | VMware offers a centralised orchestrator that provides real-time visibility, policy management and configuration control across all sites. |
| Support for Multiple Connection Types | Supports broadband, MPLS, LTE and satellite links. VMware leverages dynamic multipath optimisation (DMPO) and real-time performance metrics to select between these links. |
| Integrated Security Features | Integrates with VMware SASE for NGFW, ZTNA and secure web gateways. Security is cloud-delivered, reducing local complexity, whilst VMware also supports multiple VPNs per WAN link, improving traffic segmentation and resilience. |
| Quality of Service (QoS) | Offers application-aware QoS, with deep packet inspection, app-specific policies and real-time prioritisation for granular control across branches and cloud services. |
| Scalability and Flexibility | Scales from small branches to global enterprises. Fast onboarding and multi-tenant support make it suitable for growing organisations and service providers. Also offers zero-touch provisioning with central policy control and pre-configured edge devices wi |
| Cloud and Multi-Cloud Integration | Offers direct cloud on-ramps to AWS, Azure and Google Cloud, whilst also integrating with VMware Cloud and their private backbone for multi-cloud . |
| Resilience and Failover Capabilities | Sub-second failover with link health monitoring and path conditioning. |
| Cost Efficiency | Reduces reliance on MPLS by prioritising cheaper broadband connectivity. |
| Analytics and Reporting | Built-in analytics offer real-time and historical visibility, app-level insights and bandwidth usage metrics. |
| Programmatic APIs | Offers REST APIs for automation, orchestration and integration with third-party systems. |
| Support for Cellular Connectivity | LTE/5G supported for primary or backup connectivity. |
| AI Integrations | Both AI and machine learning used for anomaly detection, automated link remediation and policy optimisation. |
| Deployment Models Supported | Supports on-premises, hybrid and cloud-based models. |
| Compliance and Regulatory Certifications | Holds ISO 27001, SOC 2 and PCI DSS certifications. |
| Support and Training Options | Offers 24/7 global support, customer success managers and extensive online training resources via VMware Learning. |
| Target-Market Customers | Focus on Finance, Healthcare, Retail, Manufacturing, Education, Government, Technology, Transportation, Energy and Telecommunications markets. |
WatchGuard Technologies

Unranked North America Latin America Europe Middle East & Africa Asia-Pacific SMBs
Headquartered in Seattle, Washington, WatchGuard Technologies are a global leader in network security and serves more than 250,000 small and midsize enterprises worldwide.
Introducing their initial SD-WAN solution into their Fireware security software suite, replacing their previous policy-based routing solution. This has continued across later iterations, with WatchGuard offering their SD-WAN functionality embedded directly in their Firebox appliances, combining security and SD-WAN in a single platform, which provides a significant cost advantage to small and midsize businesses.
Further security features can be integrated through their Total Security Suite and, as of 2025, WatchGuard are recognised as being well-positioned to meet SD-WAN 3.0 requirements, creating a unified infrastructure for cloud, mobility, and as-a-service technologies.
| Feature | Vendor/Provider Support |
|---|---|
| Centralised Cloud Management | WatchGuard offers centralised management via its Cloud platform, providing unified visibility and policy control. |
| Support for Multiple Connection Types | Supports broadband, LTE and MPLS, with real-time performance monitoring to route traffic based on link quality. |
| Integrated Security Features | Includes a built-in Next-Generation Firewall, intrusion prevention, web filtering and antivirus. Supports multiple VPNs over a single WAN connection for improved segmentation capabilities. |
| Quality of Service (QoS) | Offers configurable QoS settings to prioritise critical applications, with QoS rules defined by application, port or protocol. Techniques supported include traffic shaping and application-layer visibility using deep packet inspection. |
| Scalability and Flexibility | Scales from small businesses to multi-site enterprises. Zero-touch deployment is supported via WatchGuard Cloud |
| Cloud and Multi-Cloud Integration | Provides integration with major cloud platforms through secure VPNs and supports cloud-hosted management, however it lacks dedicated cloud on-ramps. |
| Resilience and Failover Capabilities | Offers link monitoring, multi-path redundancy and sub-second failover to maintain service continuity. |
| Cost Efficiency | Enables cost savings by reducing reliance on MPLS, combining network and security functions into a single appliance and using broadband as a primary transport. |
| Analytics and Reporting | WatchGuard Cloud includes reporting tools with application-level insights and bandwidth usage metrics. |
| Programmatic APIs | Provides APIs for integration with third-party tools and for automating tasks such as provisioning, monitoring and policy updates. |
| Support for Cellular Connectivity | LTE support is available via compatible external modems. |
| AI Integrations | AI is used primarily in threat detection within the security features. |
| Deployment Models Supported | Supports on-premises and hybrid models. Cloud-based control is available but full cloud-native SD-WAN deployment is limited. |
| Compliance and Regulatory Certifications | Holds certifications including ISO 27001, SOC 2 and GDPR compliance. |
| Support and Training Options | Offers 24/7 support, online documentation, video tutorials and optional training courses. Premium support and account management are available for enterprise customers. |
| Target-Market Customers | Markets include Finance, Healthcare, Retail, Education, Government, Technology and Manufacturing. |
Zyxel

Unranked North America Europe Asia-Pacific SMBs
First launching it’s SD-WAN solution in 2018, Zyxel states that they "believe that this type of technology should be for everyone". This ethos has determined their market focus, as Zyxel SD-WAN primarily targets small and medium-sized businesses (SMBs), as well as catering to Managed Service Providers (MSPs).
For Managed Service Providers, Zyxel SD-WAN creates new service opportunities by allowing them to deploy multiple endpoints across client sites to create high-availability network clouds.
Zyxel has been awarded the "VPN Champion," "Network Firewall Best in ROI," and "Network Firewall Champion" from Security Solutions Professional User Rating 2025 in Germany and, whilst these aren’t specific to their SD-WAN solution, it does highlight Zyxel’s expertise in networking and security – both of which are the core of SD-WAN functionality.
| Feature | Vendor/Provider Support |
|---|---|
| Centralised Cloud Management | Zyxel’s SD-WAN is managed through the Nebula cloud platform. |
| Support for Multiple Connection Types | Zyxel supports broadband, LTE and MPLS transport types, with intelligent load balancing, application-aware routing and link failover to switch between these paths. |
| Integrated Security Features | Integrated with Zyxel’s Unified Security Gateway, the solution includes firewall, content filtering, and intrusion detection. It also supports multiple IPsec VPNs on a single WAN interface, improving security and segmentation. |
| Quality of Service (QoS) | QoS policies can be centrally defined through Nebula and enforced via deep packet inspection. |
| Scalability and Flexibility | Zyxel is well-suited for SMBs and mid-sized enterprises, allowing expansion via Nebula. New branches or remote offices can be brought online via zero-touch provisioning and centralised policy templates. |
| Cloud and Multi-Cloud Integration | Zyxel SD-WAN provides direct cloud connectivity to major platforms, such as AWS, Google Cloud and Microsoft Azure. |
| Resilience and Failover Capabilities | Offers support for link failover with sub-second detection, automatic rerouting and path redundancy. |
| Cost Efficiency | Zyxel prioritises use of broadband and LTE, which reduces reliance on costly MPLS circuits. |
| Analytics and Reporting | Nebula provides real-time and historical analytics on bandwidth usage, traffic patterns and application performance. |
| Programmatic APIs | Nebula offers open APIs that enable integration with third-party systems and automation tools. |
| Support for Cellular Connectivity | LTE and 5G connections are supported via Zyxel’s cellular-enabled routers. |
| AI Integrations | Zyxel offers basic AI-driven features in Nebula, including automated bandwidth allocation and traffic prioritisation alerts. |
| Deployment Models Supported | Offers on-premises, hybrid and cloud-managed models. |
| Compliance and Regulatory Certifications | Zyxel adheres to ISO 27001 and GDPR compliance across its cloud services. |
| Support and Training Options | Offers 24/7 online support, regional helpdesks and access to product documentation and training materials via the Zyxel Education Centre. For partners, Zyxel also offers further levels of technical assistance. |
| Target-Market Customers | Focuses on Education, Retail, Healthcare and Hospitality. |
Bigleaf Networks

Unranked North America Europe SMBs
Founded in 2012, Bigleaf Networks have since grown significantly, now offering an extensive backbone with multiple points of presence. The latest edition for these came in 2021, where an eleventh worldwide PoP was delivered in Denver, Colorado – meanwhile, data centers in Seattle, Los Angeles, Dallas, Chicago and New York highlighting Bigleaf’s ability to cater to SMBs.
This makes Bigleaf ideal for businesses that lack extensive IT resources and personnel but need reliable internet connectivity for cloud-based applications, especially when considering that Bigleaf peers with over 150 different cloud, content, and carrier networks.
Whilst Bigleaf does not meet the criteria to gain a Gartner magic quadrant status, Businesswire recognised Bigleaf Networks as a leader in the SD-WAN market, winning multiple G2 Winter 2025 Awards for categories such as Best Estimated ROI, Fastest Implementation and Best Usability.
| Feature | Vendor/Provider Support |
|---|---|
| Centralised Cloud Management | Bigleaf provides a centralised web-based portal offering real-time visibility and proactive alerts into network activity. |
| Support for Multiple Connection Types | Supports broadband, LTE, satellite and MPLS. Switches between these links via application-aware, dynamic path control with automatic failover and traffic steering. |
| Integrated Security Features | N/A (Customers are expected to integrate their own firewalls or third-party security tools.) |
| Quality of Service (QoS) | Offers application-aware QoS that prioritises traffic automatically via automatic failover, session re-routing and real-time link assessments. |
| Scalability and Flexibility | Scales well for small to mid-sized businesses and distributed enterprises -however, not typically used in very large, global networks.Offers zero touch provisioning for plug-and-play deployment with automatic configuration. |
| Cloud and Multi-Cloud Integration | Provides automatic cloud prioritisation with direct access to its own backbone. |
| Resilience and Failover Capabilities | Offers sub-second failover with session preservation, automatic rerouting and continuous link quality monitoring. |
| Cost Efficiency | Enables use of affordable broadband links instead of MPLS. |
| Analytics and Reporting | Provides live and historical reporting on circuit performance, application behaviour and outage history. |
| Programmatic APIs | N/A |
| Support for Cellular Connectivity | Supports LTE as a WAN connection. |
| AI Integrations | N/A |
| Deployment Models Supported | Offers cloud-based models only. |
| Compliance and Regulatory Certifications | N/A |
| Support and Training Options | Provides 24/7 customer support, onboarding help, online documentation and responsive technical assistance. |
| Target-Market Customers | Primarily targets businesses from Healthcare, Retail, Education, Technology and Manufacturing markets. |
Checkpoint Software Technologies

Unranked North America Latin America Europe Middle East & Africa Asia-Pacific Large Enterprises
In 1993 Check Point Software Technologies were well-known for initially introducing FireWall-1, the IT industry's first stateful inspection firewall technology. However, it took until February 2023 for Check Point's Quantum SD-WAN solution be released.
Much was made of this fact, however, Check Point had previously considered acquiring an SD-WAN vendor but ultimately walked away due to concerns over the quality of the technology and the belief that the integration with both their firewalls and networking code would be far stronger when built from the ground-up.
This delayed entry into the SD-WAN market represents Check Point's strategic decision to prioritise security integration over speed to market, which should be viewed positively by enterprises that are concerned with security capabilities of a chosen SD-WAN solution.
Further to this, Check Point's Quantum SD-WAN supports more than 1,000 applications and is positioned as part of a complete SASE package, when combined with their Harmony Connect (SSE) product – extending the range of security features that the solution has to offer.
| Feature | Vendor/Provider Support |
|---|---|
| Centralised Cloud Management | Managed through Check Point Infinity Portal, offering a unified cloud-native interface for SD-WAN, security and policy management. |
| Support for Multiple Connection Types | Supports broadband, LTE/5G, MPLS and satellite links, with application-aware routing and real-time link assessment to switch between links. |
| Integrated Security Features | Integrates a full NGFW, IPS, antivirus, anti-bot, URL filtering and Zero Trust controls. |
| Quality of Service (QoS) | Provides granular QoS with dynamic bandwidth allocation, application-layer awareness, deep packet inspection and traffic shaping. |
| Scalability and Flexibility | Supports thousands of sites with centralised control. Easily scales, leveraging zero-touch provisioning via the Infinity portal, for distributed enterprises, hybrid workforces and branch expansion. |
| Cloud and Multi-Cloud Integration | Direct cloud access supported via secure cloud connectors that integrates with AWS, Azure and Google Cloud. |
| Resilience and Failover Capabilities | Offers sub-second failover, WAN link monitoring and active-active configurations for continuous uptime. |
| Cost Efficiency | Reduces costs by consolidating network and security into one platform. Enables use of affordable broadband while reducing dependency on MPLS. |
| Analytics and Reporting | Provides real-time and historical analytics through Infinity Portal. |
| Programmatic APIs | RESTful APIs allow automation of provisioning, monitoring, and policy management. |
| Support for Cellular Connectivity | Offers businesses with LTE/5G support with integrated security, enabling remote site and mobile connectivity. |
| AI Integrations | Uses AI to analyse traffic patterns, auto-adjust policies and detect anomalies. |
| Deployment Models Supported | Available as on-premises, hybrid or cloud-delivered SD-WAN. |
| Compliance and Regulatory Certifications | Complies with ISO 27001, SOC 2, PCI DSS, HIPAA and other industry regulations. |
| Support and Training Options | Offers 24/7 support, online knowledge base, dedicated account management and training through Check Point’s Infinity Training portal. |
| Target-Market Customers | Targets Finance, Healthcare, Retail, Government, Education, Technology, Manufacturing and Telecommunications markets. |
Cloudflare

Unranked North America Latin America Europe Middle East & Africa Asia-Pacific Large Enterprises
Cloudflare doesn't offer a traditional SD-WAN solution, but rather an alternative called Magic WAN. Magic WAN is a software-defined underlay built on the company's private backbone network. While SD-WAN typically relies on physical or virtual appliances at each site, Magic WAN minimises on-premises hardware requirements by leveraging Cloudflare's global edge network.
Magic WAN forms part of Cloudflare One, their complete SASE platform, integrating with other security features such as Magic Firewall for enforcing network policies at Cloudflare's edge.
| Feature | Vendor/Provider Support |
|---|---|
| Centralised Cloud Management | Cloudflare One provides unified SD-WAN and security management via a single cloud dashboard. |
| Support for Multiple Connection Types | Supports broadband, LTE/5G, MPLS and satellite, offering application-aware routing to switch between these links. |
| Integrated Security Features | Provides built-in Zero Trust security with secure web gateway, next generation firewall and zero trust network architecture. |
| Quality of Service (QoS) | Offers configurable QoS policies, enabling prioritisation of latency-sensitive apps via deep packet inspection and traffic shaping. |
| Scalability and Flexibility | Fully cloud-based and scalable across thousands of sites. Offers zero-touch provisioning and automatic policy enforcement that easily integrates with existing networks via Cloudflare’s global edge. |
| Cloud and Multi-Cloud Integration | Direct on-ramps to AWS, Azure, Google Cloud and other cloud platforms. Leverages Cloudflare’s private backbone for consistent, low-latency cloud performance. |
| Resilience and Failover Capabilities | Cloudflare offers sub-second failover, intelligent path monitoring and multi-path redundancy capabilities. |
| Cost Efficiency | Replaces MPLS with cost-effective broadband. |
| Analytics and Reporting | Offers real-time and historical analytics with application-level insights. |
| Programmatic APIs | Provides APIs for automation and third-party integration. |
| Support for Cellular Connectivity | Supports LTE/5G as a primary or backup WAN link. |
| AI Integrations | Uses AI for predictive performance optimisation, automatic policy tuning and anomaly detection to prevent outages. |
| Deployment Models Supported | Fully cloud-delivered model, with hybrid support via existing infrastructure. |
| Compliance and Regulatory Certifications | Holds ISO 27001, SOC 2 Type II, PCI DSS and HIPAA certifications. |
| Support and Training Options | Offers 24/7 support, onboarding assistance, online training and a knowledge base. Enterprise plans can also benefit from dedicated account management. |
| Target-Market Customers | Focuses on businesses within Finance, Healthcare, Retail, Technology, Education, Government, Manufacturing and Transportation markets. |
FlexiWAN

Unranked North America Latin America Europe Middle East & Africa Asia-Pacific Open-Source Market
FlexiWAN is the industry's first open-source SD-WAN solution, removing vendor lock-in and enabling both dynamic third-party applications and integrations with cloud security SASE solutions.
Officially launched in April 2019 at the MPLS+SDN+NFV World event in Paris, FlexiWAN offers a hardware-agnostic model that works on a variety of open computing platforms. This makes it a cost-effective solution, enabling the use of a variety of hardware resources and allows the scaling of small deployments (2 CPU cores and 4 GB RAM) to large servers and cloud platforms.
Since its launch, flexiWAN has grown significantly, with more than 4,000 accounts created on the platform, as of 2025, and with the addition of Adtran's SmartWAN capabilities, FlexiWAN now brings several AI-driven features to improve performance and reliability for businesses.
| Feature | Vendor/Provider Support |
|---|---|
| Centralised Cloud Management | Flexiwan provides a modular, cloud-based management system with real-time visibility, centralised policy control and open architecture. |
| Support for Multiple Connection Types | Supports broadband, LTE/5G, MPLS and satellite, switching links via application-aware routing and dynamic path selection capabilities. |
| Integrated Security Features | Offers integrated firewall capabilities and supports third-party security services. Users can choose their preferred security stack, aligning with Flexiwan’s modular design. |
| Quality of Service (QoS) | Allows application-based prioritisation and dynamic traffic shaping. Enables traffic steering and performance monitoring for specific applications. |
| Scalability and Flexibility | Scales from small sites to large/global networks. Offers zero-touch provisioning via its cloud manager. Centralised templates and open APIs simplify configuration. |
| Cloud and Multi-Cloud Integration | Supports direct cloud access via integrations with AWS, Azure and other public clouds. |
| Resilience and Failover Capabilities | Provides multi-path redundancy with failover in under a second. |
| Cost Efficiency | Reduces costs by using low-cost internet and consolidating network functions. Open-source licensing avoids vendor lock-in and allows budget-friendly scaling. |
| Analytics and Reporting | Offers real-time dashboards and historical data on bandwidth, application usage and network health. |
| Programmatic APIs | Open source solution that provides open APIs and SDKs for full network programmability. |
| Support for Cellular Connectivity | LTE/5G support is available for primary or backup use. |
| AI Integrations | N/A |
| Deployment Models Supported | Supports cloud-managed, hybrid and on-premises deployments. |
| Compliance and Regulatory Certifications | N/A |
| Support and Training Options | Offers online documentation, community support and partner-led training. |
| Target-Market Customers | Designed for Technology, Telecommunications, Education, Retail and Transportation. |
Netskope

Leader North America Latin America Europe Middle East & Africa Asia-Pacfic Remote Workforces
In July 2024, Netskope debuted as a Leader in the 2024 Magic Quadrant for Single-Vendor SASE, which includes both Netskope's Borderless SD-WAN and their Intelligent SSE (Security Service Edge) solution.
Netskope's SD-WAN journey began with the acquisition of Infiot in 2022, which led to the introduction of Netskope Borderless SD-WAN. Netskope's NewEdge network, which is where their SD-WAN services reside, spans 71+ regions worldwide, supporting both the hybrid and cloud-first enterprise markets.
Netskope's approach allows customers to make best-of-breed security and networking decisions without trade-offs, supporting over 75,000 applications with context-aware policies.
| Feature | Vendor/Provider Support |
|---|---|
| Centralised Cloud Management | Netskope provides a unified cloud-based management console offering real-time visibility, policy control and analytics across SD-WAN and SSE services. |
| Support for Multiple Connection Types | Supports broadband, LTE/5G, MPLS, and satellite links. Netskope uses real-time analytics to monitor performance and dynamically select the appropriate path. |
| Integrated Security Features | Netskope’s SD-WAN includes embedded NGFW, SWG, CASB, ZTNA and supports multiple VPN overlays per WAN link, for improved segmentation. |
| Quality of Service (QoS) | Provides dynamic adjustments via deep packet inspection and application-based policies to offer Quality of Service. |
| Scalability and Flexibility | Cloud-native architecture built for large-scale deployment with support for hybrid workforces. Offers zero-touch provisioning to quickly bring new sites online. |
| Cloud and Multi-Cloud Integration | Integrates directly with major cloud providers using private backbones and local cloud on-ramps, enabling multi-cloud environments. |
| Resilience and Failover Capabilities | Provides sub-second failover with continuous link monitoring and multi-path redundancy. |
| Cost Efficiency | Reduces reliance on MPLS by using broadband and cellular links. |
| Analytics and Reporting | Offers analytics with AI-powered insights, historical trend data and detailed traffic reports. |
| Programmatic APIs | Provides open APIs for orchestration and integration with ITSM, SIEM and third-party systems. |
| Support for Cellular Connectivity | Full support for LTE and 5G links, enabling remote workforces. |
| AI Integrations | Utilises AI to automate traffic routing, detect anomalies and recommend policy changes. |
| Deployment Models Supported | Supports cloud-native, hybrid and on-premises deployments |
| Compliance and Regulatory Certifications | Holds certifications including ISO 27001, SOC 2 Type II and supports compliance with GDPR, HIPAA and PCI DSS. |
| Support and Training Options | Offers 24/7 global support, dedicated account management, online training and customer success programmes. |
| Target-Market Customers | Focuses on Finance, Healthcare, Retail, Manufacturing, Education, Government, Technology, Transportation, Energy and Telecommunications markets. |
Zscaler

Unranked North America Latin America Europe Middle East & Africa Asia-Pacific SMBs
At Zenith Live 2023, Zscaler introduced its first networking appliance as part of its Zero Trust Branch Connectivity product, which moved away from their previous enteries into the SD-WAN market – which had been not as a vendor but as a security partner for existing SD-WAN solutions.
Since then, Zscaler has broaden their solution into a full SASE solution and has become a significant player in the SASE market. Zscaler are now the overall leader in the SASE market, extending their market share to become only the second vendor (after Cisco in Q3 2019) to achieve 20% or more revenue share.
| Feature | Vendor/Provider Support |
|---|---|
| Centralised Cloud Management | Offers a unified, cloud-native management platform with real-time visibility and policy control via the Zscaler Central Authority. |
| Support for Multiple Connection Types | Supports broadband, LTE/5G, MPLS and satellite connections, whilst using cloud intelligence to optimise this traffic routing. |
| Integrated Security Features | Fully integrates Zero Trust Network Access, Cloud Firewall and advanced threat protection, whilst also offering support for multiple VPNs over a single WAN. |
| Quality of Service (QoS) | Enables granular QoS with dynamic adjustment based on real-time application requirements, application-aware routing and cloud proximity for improved Software-as-a-Service and web application performance. |
| Scalability and Flexibility | Scales easily across global enterprises, enabling zero-touch provisioning and central policy control. |
| Cloud and Multi-Cloud Integration | Offers direct cloud on-ramps to AWS, Azure, Google Cloud and other platforms via Zscaler Cloud Connect - utilising private backbones to improve this connectivity. |
| Resilience and Failover Capabilities | Provides sub-second failover with multi-path redundancy and real-time link health monitoring. |
| Cost Efficiency | Reduces dependency on MPLS by utilising both broadband and mobile links, which are cheaper. |
| Analytics and Reporting | Includes AI-driven analytics for real-time insights and historical trends. |
| Programmatic APIs | Provides RESTful APIs for integration with third-party tools and automation systems. |
| Support for Cellular Connectivity | Supports LTE and 5G as primary or backup connectivity options. |
| AI Integrations | Utilises AI for threat detection, policy automation and performance tuning capabilities. |
| Deployment Models Supported | Cloud-delivered by design but supports hybrid scenarios through integration with on-premises infrastructure and SD-WAN partners. |
| Compliance and Regulatory Certifications | Holds ISO 27001, SOC 2 Type II, PCI DSS and HIPAA certifications. |
| Support and Training Options | Offers 24/7 global support, onboarding assistance, knowledge base and online training resources. Premium support includes dedicated account teams. |
| Target-Market Customers | Targets Finance, Healthcare, Retail, Manufacturing, Education, Government, Technology, Transportation, Energy and Telecommunications markets. |
Managed Telco SD-WAN Providers
AT&T

Cisco Catalyst Vmware VeloCloud HPE Aruba EdgeConnect FatPipe Fortinet Palo Alto Prisma North America
AT&T offers a range of managed SD-WAN services, partnering with multiple vendors including Cisco Catalyst, VMware VeloCloud, HPE Aruba EdgeConnect and FatPipe. Providing fully managed and co-managed SD-WAN options, AT&T's own network-based SD-WAN platform offers features such as direct cloud on-ramps and extensive interoperability. AT&T also offers a self-service SD-WAN option for SMBs through AT&T Business Wi-Fi with Cisco Meraki, providing simplified network management with cloud-based controls.
Since 2022, AT&T has offered its next-generation SD-WAN service to deliver up to 10 Gbps speeds with improved orchestration, allowing customers to run multiple virtual network functions.
AT&T has consistently been recognised as a leader in the managed SD-WAN space, ranking first in the 2019 U.S. Carrier Managed Leaderboard report for SD-WAN Services by Vertical Systems Group.
| Feature | Vendor/Provider Support |
|---|---|
| Partnered SD-WAN Vendors | AT&T collaborates with multiple SD-WAN vendors, including Cisco (Cisco SD-WAN), Fortinet, Palo Alto Networks, HPE Aruba EdgeConnect and Vmware VeloCloud. |
| Integrated Security Features | AT&T's SD-WAN solutions incorporate security features such as Next-Generation Firewalls (NGFWs), Secure Access Service Edge (SASE) frameworks, and Zero Trust Network Access (ZTNA). |
| Cloud and Multi-Cloud Integration | AT&T's SD-WAN solutions support integration with leading public cloud platforms (AWS, Azure and Google Cloud), offering direct cloud connectivity and optimised routing, as well as offering multi-cloud capabilities for businesses that utilise a wider rang |
| Cost Efficiency | Optimised transport and operational costs through reduced MPLS reliance, centralised managed, Zero-Touch Deployment and improved application performance. |
| Support for Cellular Connectivity | AT&T's SD-WAN solutions support LTE and 5G connectivity, implemented through wireless/LTE transport options, adding redundancy, increasing deployment flexibility and improving connectivity in remote or mobile scenarios. |
| Deployment Models Supported | AT&T offers on-premises, hybrid and fully cloud-based SD-WAN deployment options, allowing organisations to choose deployment models that best-align with their infrastructure strategies, whether they require legacy-compatible, hybrid or cloud-first approac |
| Performance Guarantees or SLAs | AT&T offers SD-WAN SLAs for network availability, packet loss, congestion, jitter and latency. |
| Support and Training Options | AT&T offers 24/7 helpdesk support, dedicated account managers and online training resources. |
| Target-Market Customers | Finance, Healthcare, Retail, Manufacturing, Education, Government, Technology, Transportation, Energy, Telecommunications. |
BT

Versa Networks Cisco Catalyst Cisco Meraki Nuage Networks VNS Palo Alto Prisma Fortinet VMware VeloCloud Europe
BT partners with Cisco Catalyst, Cisco Meraki, Nuage Networks VNS, Palo Alto Prisma, Fortinet, and VMware VeloCloud for its managed SD-WAN services. For businesses with a focus on security and network performance, BT has launched a global managed service with Cisco, as well as security-focused SD-WAN through Fortinet. Their Agile Connect SD-WAN solution, which utilises Nokia Nuage Networks, provides pre-built gateways for businesses requiring regional performance optimisation.
BT is listed in fourth place amongst the top companies for managed SD-WAN services according to Vertical Systems Group's Global Provider Carrier Managed SD-WAN Leaderboard.
| Feature | Vendor/Provider Support |
|---|---|
| Partnered SD-WAN Vendors | BT collaborates with leading SD-WAN vendors, including Cisco, VMware VeloCloud, Fortinet and Palo Alto Networks. |
| Integrated Security Features | BT's SD-WAN solutions incorporate advanced security measures such as Next-Generation Firewall (NGFW), Zero Trust Network Access (ZTNA), Secure Web Gateway (SWG) and Cloud Access Security Broker (CASB) functionalities. |
| Cloud and Multi-Cloud Integration | BT's SD-WAN solutions offer direct connectivity to major cloud platforms such as AWS, Microsoft Azure and Google Cloud, supporting multi-cloud environments. |
| Cost Efficiency | Optimised transport and operational costs through reduced MPLS reliance, centralised managed, Zero-Touch Deployment and improved application performance. |
| Support for Cellular Connectivity | BT's SD-WAN solutions support LTE and 5G connectivity, implemented through wireless/LTE transport options, adding redundancy, increasing deployment flexibility and improving connectivity in remote or mobile scenarios. Deployment Models Supported |
| Deployment Models Supported | BT offers on-premises, hybrid and fully cloud-based SD-WAN deployment options, allowing organisations to choose deployment models that best-align with their infrastructure strategies, whether they require legacy-compatible, hybrid or cloud-first approach. |
| Performance Guarantees or SLAs | BT offers a market-leading SLA for their BTnet Leased Line service with a 100% target availability guarantee, including financial compensation if they fail to meet this commitment. |
| Support and Training Options | BT offers comprehensive customer support, including 24/7 helpdesks, dedicated account managers and online training resources. |
| Target-Market Customers | BT's SD-WAN solutions are suitable for various sectors, including Finance, Healthcare, Retail, Manufacturing, Education, Government, Technology, Transportation, Energy, and Telecommunications. |
Lumen Technologies (CenturyLink)

Versa Networks VMware VeloCloud Cisco Catalyst Cisco Meraki Fortinet North America Europe Asia-Pacific
Previously known as CenturyLink, Lumen Technologies delivers fully managed SD-WAN solutions, including partnerships with VMware VeloCloud, Cisco Catalyst, Cisco Meraki, Versa Networks and Fortinet. Lumen integrates AI-driven analytics and automation, also offering co-managed solutions with improved network visibility and control. One of the key benefits of utilising Lumen is their Sovereign Secure SASE solution with Versa, which significantly improves security at the network edge for more rigorously regulated industries - such as financial services.
| Feature | Vendor/Provider Support |
|---|---|
| Partnered SD-WAN Vendors | Lumen collaborates with leading SD-WAN vendors, including Versa Networks, VMware (VeloCloud), Cisco Meraki and Cisco Catalyst. |
| Integrated Security Features | Lumen's SD-WAN solutions incorporate advanced security measures such as stateful firewalls, intrusion detection and prevention systems (IDS/IPS), URL filtering and content filtering. |
| Cloud and Multi-Cloud Integration | Lumen's SD-WAN integrates with major cloud platforms, such as Microsoft Azure, Google Cloud and AWS, Lumen offers direct cloud connectivity via MPLS/Ethernet across 21 countries. |
| Cost Efficiency | Optimised transport and operational costs through reduced MPLS reliance, centralised managed, Zero-Touch Deployment and improved application performance. |
| Support for Cellular Connectivity | Lumen's SD-WAN solutions support LTE and 5G connectivity, implemented through wireless/LTE transport options, adding redundancy, increasing deployment flexibility and improving connectivity in remote or mobile scenarios. Deployment Models Supported |
| Deployment Models Supported | Lumen offers flexible deployment options, including on-premises, hybrid and fully cloud-based. |
| Performance Guarantees or SLAs | Lumen offers end-to-end SLA guarantees for Performance Assurance, which includes metrics for frame delivery, frame delay, and delay variation. |
| Support and Training Options | Lumen offers customer support, including 24/7 helpdesks, dedicated account managers and online training resources. |
| Target-Market Customers | Lumen's SD-WAN solutions cater to various sectors, including finance, healthcare, retail, manufacturing, education, government, technology, transportation, energy and telecommunications. |
China Mobile

China Mobile International North America Europe Middle East & Africa Asia-Pacific
China Mobile offers SD-WAN services through its subsidiary China Mobile International (CMI), delivering solutions for businesses requiring cross-border network connectivity. The CMI SD-WAN platform integrates with a global backbone for improved performance and connectivity, whilst bilingual support ensures your business can get the help they need, regardless of the region and direct connectivity options between China and international markets, which is hugely beneficial for businesses that operate in China, such as manufacturers.
| Feature | Vendor/Provider Support |
|---|---|
| Partnered SD-WAN Vendors | N/A (Only utilises China Mobile International) |
| Integrated Security Features | China Mobile's SD-WAN solutions offer traffic encryption. |
| Cloud and Multi-Cloud Integration | The SD-WAN solution supports access to public cloud platforms. |
| Cost Efficiency | By utilising broadband, internet and LTE, China Mobile's SD-WAN provides cost-efficiencies by reducing reliance on traditional MPLS circuits. |
| Support for Cellular Connectivity | China Mobile supports LTE connectivity for redundancy and more rural requirements. |
| Deployment Models Supported | China Mobile offers flexible deployment options, including on-premises, hybrid and cloud-based SD-WAN solutions. |
| Performance Guarantees or SLAs | China Mobile Americas provides a specific SLA of 99.95% between CGW to CGW (Customer Gateway to Customer Gateway), with latency guarantees available upon request. |
| Support and Training Options | China Mobile offers bilingual customer support to assist clients with implementation and ongoing management of their SD-WAN and has been known to host big data training camps |
| Target-Market Customers | Retail, Manufacturing, Technology, Transportation |
China Telecom

Versa Networks North America Europe Middle East & Africa Asia-Pacific
China Telecom provides managed and self-managed SD-WAN solutions through its partnership with Versa Networks. Operating via 15 global cloud hubs, China Telecom offer an SD-WAN platform that is designed for compliance with Chinese regulatory requirements whilst also still integrating with mainstream SaaS applications. This functionality is essential for businesses operating in and around the China region and China Telecom enables secure, cross-border connectivity for these businesses.
| Feature | Vendor/Provider Support |
|---|---|
| Partnered SD-WAN Vendors | China Telecom partners with Versa Networks |
| Integrated Security Features | China Telecom offers security integrations such as Next-Generation Firewall (NGFW), Unified Threat Management (UTM), Intrusion Detection Systems (IDS), and Intrusion Prevention Systems (IPS). |
| Cloud and Multi-Cloud Integration | China Telecom's SD-WAN solutions offer integratiosn with major cloud platforms and supports multi-cloud environments. |
| Cost Efficiency | The solutions leverage cost-effective broadband options and consolidate network functions, leading to reduced reliance on expensive MPLS circuits and lower operational expenses. |
| Support for Cellular Connectivity | China Telecom's SD-WAN solutions support LTE and 5G connectivity, enabling remote or mobile workforces. |
| Deployment Models Supported | The SD-WAN offerings include on-premises, hybrid, and fully cloud-based options. |
| Performance Guarantees or SLAs | China Telecom provides performance Service Level Agreements (SLAs), including uptime guarantees and latency thresholds. |
| Support and Training Options | China Telecom offers support through 24/7 helpdesks, dedicated account managers and online training resources. |
| Target-Market Customers | China Telecom's SD-WAN solutions are tailored for various industries, including Finance, Healthcare, Retail, Manufacturing, Education, Government, Technology, Transportation, Energy and Telecommunications. |
China Unicom

Cisco Catalyst Huawei Ngena North America Europe Middle East & Africa Asia-Pacific
Partnering with Cisco, Huawei and Ngena for their SD-WAN services, China Unicom delivers managed SD-WAN with a focus on cross-border networking and hybrid cloud integration. Their SD-WAN platform supports multi-cloud connectivity and is tailored for businesses that require high-performance links between China and other regions.
Previously, China Unicom has received the "SD-WAN Project Excellent Service Award" and the "SD-WAN Excellent Industry Application Award", awarded by CITIC telecom.
| Feature | Vendor/Provider Support |
|---|---|
| Partnered SD-WAN Vendors | China Unicom offers SD-WAN partnerships with Cisco Catalyst, Huawei and Ngena. |
| Integrated Security Features | China Unicom's SD-WAN solutions offer end-to-end encrypted IPsec VPN tunnels. |
| Cloud and Multi-Cloud Integration | The SD-WAN solutions integrate seamlessly with major cloud platforms, including Alibaba Cloud, Tencent Cloud, AWS, and Huawei Cloud. |
| Cost Efficiency | By leveraging a combination of MPLS,VPN and LTE, China Unicom's SD-WAN solutions enable more efficient bandwidth utilisation, reducing reliance on expensive MPLS circuits |
| Support for Cellular Connectivity | China Unicom supports LTE connectivity. |
| Deployment Models Supported | China Unicom offers flexible deployment options, including on-premises setups, hybrid models and fully cloud-based SD-WAN solutions. |
| Performance Guarantees or SLAs | N/A |
| Support and Training Options | China Unicom collaborates with educational institutions such as Huawei ICT Academy to provide training programs. China Unicom also offers consultation services where their professional team gets involved at the early stages of business planning to design |
| Target-Market Customers | China Unicom's targets finance, healthcare, retail, manufacturing, education, government, technology, transportation, energy and telecommunications markets. |
Comcast Business

Versa Networks Fortinet HPE Aruba EdgeConnect Cisco Catalyst Cisco Meraki North America
Comcast Business offers fully managed SD-WAN solutions through partnerships with Versa Networks, Fortinet, HPE Aruba EdgeConnect, Cisco Catalyst and Cisco Meraki. Their ActiveCore platform has been a key feature for their SD-WAN solution, providing cloud-based management and network automation capabilities.
In 2023, Comcast Business was recognised as a Leader in Managed SD-WAN Services and SDN Transformation Services by Information Services Group (ISG) in their ISG Provider Lens report.
| Feature | Vendor/Provider Support |
|---|---|
| Partnered SD-WAN Vendors | Comcast Business partners with Versa Networks, Fortinet, HPE Aruba EdgeConnect, Cisco Catalyst and Meraki. |
| Integrated Security Features | Comcast Business' SD-WAN solutions integrate security features such as Next-Generation Firewall (NGFW), Secure Web Gateway (SWG) and Unified Threat Management (UTM). |
| Cloud and Multi-Cloud Integration | The solutions offer seamless integration with leading cloud platforms, supporting multi-cloud environments. Features include direct cloud on-ramps and private backbone usage. |
| Cost Efficiency | Comcast Business's SD-WAN leverages cost-effective broadband options, reducing reliance on expensive MPLS circuits. |
| Support for Cellular Connectivity | The SD-WAN solutions support LTE and 5G connectivity, enabling remote workforces and adding redundancy capabilities. |
| Deployment Models Supported | Comcast Business offers on-premises, hybrid, and fully cloud-based SD-WAN options. |
| Performance Guarantees or SLAs | Comcast Business's managed SD-WAN solution offers a 99.99% uptime SLA, delivered through their extensive IP backbone network. |
| Support and Training Options | Comcast Business offers 24/7 customer support, dedicated account managers and online training resources. |
| Target-Market Customers | Comcast Business's SD-WAN solutions are suitable for various sectors, including finance, healthcare, retail, manufacturing, education, government, technology, transportation, energy and telecommunications. |
Deutsche Telekom

Juniper Networks Telekom SD-X Europe Middle East & Africa Asia-Pacific
Deutsche Telekom’s SD-WAN solutions are built in partnership with Juniper Networks, offering managed services under the Telekom SD-X (Software Defined Everything) platform. Deutsche Telekom SD-X acts as a marketplace where customers can select and combine services in a store with modular components - creating a multivendor service edge, supporting and enabling improvements to various network capabilities, such as internet connectivity, security, stable fast local networks, WiFi, VPN and remote access.
| Feature | Vendor/Provider Support |
|---|---|
| Partnered SD-WAN Vendors | Deutsche Telekom supports Juniper Networks, as well as offering their own Telekom SD-X. |
| Integrated Security Features | Deutsche Telekom offers integrations for Secure Access Service Edge (SASE) frameworks, including Secure Web Gateway (SWG) and Cloud Access Security Broker (CASB). |
| Cloud and Multi-Cloud Integration | Deutsche Telekom's SD-WAN solutions integrate with leading cloud platforms and support multi-cloud environments. They offer direct cloud on-ramps and utilise private backbones. |
| Cost Efficiency | By leveraging low-cost broadband options and offering flexible licensing models, Deutsche Telekom's SD-WAN solutions reduce reliance on expensive MPLS circuits and reduces operational expenses. |
| Support for Cellular Connectivity | Deutsche Telekom supports both LTE and 5G connectivity, improving redundancy, deployment flexibility and ensuring connectivity in remote or mobile scenarios. |
| Deployment Models Supported | Deutsche Telekom offers flexible deployment models, including on-premises, hybrid and fully cloud-based SD-WAN options. |
| Performance Guarantees or SLAs | Deutsche Telkom provides service and performance SLAs. |
| Support and Training Options | Support and training options are available, such as 24/7 helpdesks, dedicated account managers and online training resources. |
| Target-Market Customers | Deutsche Telekom's managed SD-WAN solutions are suitable for a wide range of industries, including finance, healthcare, retail, manufacturing, education, government, technology, transportation, energy and telecommunications. |
GTT Communications

Fortinet HPE Aruba EdgeConnect VMware VeloCloud North America Europe
GTT Communications partners with Fortinet, HPE Aruba EdgeConnect and VMware VeloCloud for managed SD-WAN services. With a global backbone network composed of over 450 points of presence, GTT provides secure, scalable and cloud-ready solutions tailored for distributed enterprises.
GTT Communications have been awarded the title of Leader in the Managed SD-WAN for Germany by the Information Services Group (ISG) in their ISG Provider Lens Network report.
| Feature | Vendor/Provider Support |
|---|---|
| Partnered SD-WAN Vendors | GTT Communications partners with Fortinet, HPE Aruba EdgeConnect and VMware VeloCloud |
| Integrated Security Features | GTT's SD-WAN integrates security measures such as unified firewall capabilities. |
| Cloud and Multi-Cloud Integration | GTT's SD-WAN solution supports integration with leading cloud platforms such as Azure, AWS and Google Cloud. |
| Cost Efficiency | GTT's SD-WAN leverages broadband, VPN and MPLS, to optimise connectivity and scalability, reducing reliance on expensive MPLS circuits and simplifying infrastructure requirements. |
| Support for Cellular Connectivity | GTT Communications' managed SD-WAN services support both LTE and 5G connectivity options |
| Deployment Models Supported | GTT offers flexible deployment options, including on-premises, hybrid and fully cloud-based SD-WAN solutions. |
| Performance Guarantees or SLAs | GTT provides 99.999% availability SLAs, with a ≤0.1% frame/packet loss ratio and frame jitter guaranteed to be ≤2ms. |
| Support and Training Options | GTT offers ongoing local support from certified experts and basic strategic guidance for optimising SD-WAN deployment. |
| Target-Market Customers | GTT's SD-WAN solutions are suitable for various sectors, including finance, healthcare, retail, manufacturing, education, government, technology, transportation, energy and telecommunications. |
Hughes Network Systems

VMware VeloCloud Fortinet Cisco Meraki Cradlepoint North America Latin America Europe Asia-Pacific
Hughes Network Systems introduced its managed SD-WAN solution for the public sector in 2017, adding it to their large portfolio of HughesON managed services for multi-site organisations and complimenting their previously developed proprietary ActiveTechnologies, which forms the backbone of their SD-WAN solution.
As a global leader in managed SD-WAN, Hughes has implemented and manages thousands of SD-WAN deployments for more than 100 customers across North America and internationally.
In 2018, HughesON Managed SD-WAN won the SD-WAN Product of the Year Award from Internet Telephony magazine, showcasing their SD-WAN capabilities.
| Feature | Vendor/Provider Support |
|---|---|
| Partnered SD-WAN Vendors | Hughes Network Systems partners with VMware VeloCloud, Fortinet, Cisco Merkai and Cradlepoint |
| Integrated Security Features | Security offerings include Next-Generation Firewall (NGFW), Secure Web Gateway (SWG) and encryption capabilities. |
| Cloud and Multi-Cloud Integration | Direct cloud on-ramps to AWS, Azure, and Google Cloud. Supports multi-cloud networking with private backbone access. |
| Cost Efficiency | Supports both broadband and LTE to reduce MPLS dependency. |
| Support for Cellular Connectivity | Supports LTE and 5G connectivity with automatic failover. |
| Deployment Models Supported | Deployment for on-premises, hybrid and cloud-based architectures. |
| Performance Guarantees or SLAs | Although no SLAs, Hughes features ActivePath technology which uses Intelligent Multipath Replication (IMR) to automatically replicate application traffic across available WAN paths to prevent brownout and blackout for applications such as VoIP. |
| Support and Training Options | Provides 24/7 support, online training and dedicated account management. |
| Target-Market Customers | Used in sectors such as Finance, Healthcare, Retail, Government, Technology, Transportation, Telecommunications. |
KDDI

Cisco Catalyst HPE Aruba EdgeConnect Fortinet Latin America Europe Asia-Pacific
The KDDI Corporation is a large Japanese telecommunications provider. KDDI has established a global presence by deploying managed SD-WAN services across multiple regions, including Europe, the Americas and ASEAN, partnering with vendors such as Cisco to deliver these solutions.
All Nippon Airways (ANA) implemented KDDI's SD-WAN, enabling new work styles for employees across global locations and providing consistent service quality across geographical boundaries.
| Feature | Vendor/Provider Support |
|---|---|
| Partnered SD-WAN Vendors | KDDI partners with Cisco Catalyst, HPE Aruba EdgeConnect and Fortinet. |
| Integrated Security Features | Offers KDDI Security Cloud based on Symantec Blue Coat technology, next-generation firewall (NGFW), secure web gateway, advanced threat prevention and managed threat detection and response (MDR) services. |
| Cloud and Multi-Cloud Integration | KDDI's SD-WAN solutions facilitate integration with leading cloud platforms, including Microsoft 365, AWS, Google Cloud and with particular emphasis on Microsoft Azure |
| Cost Efficiency | Reduces WAN costs by utilising less expensive broadband connections instead of costly MPLS circuits. |
| Support for Cellular Connectivity | KDDI's SD-WAN solutions support both LTE and 5G. |
| Deployment Models Supported | KDDI offers flexible deployment options, including on-premises, hybrid and fully cloud-based SD-WAN. |
| Performance Guarantees or SLAs | KDDI provides Service Level Agreements (SLAs) that guarantee service availability, performance, and support response times for their SD-WAN solutions |
| Support and Training Options | Support services include a 24/7 dedicated service desk and both remote / on-site technical support. |
| Target-Market Customers | KDDI's SD-WAN solutions are suitable for various sectors, including finance, healthcare, retail, manufacturing, education, government, technology, transportation, energy and telecommunications. |
Macquarie Technology Group

VMware VeloCloud Asia-Pacific
Based in Australia, Macquarie Technology Group has demonstrated significant growth in their SD-WAN deployment, serving over 6,000 sites and securing major contracts with pharmaceutical and financial services businesses. Macquarie selected VeloCloud after spending a year researching and evaluating 28 different SD-WAN providers worldwide, which has proven to be a successful choice, as Macquarie have been recognised as the Best SD-WAN Supplier in APAC and winning VMware's Partner Innovation Award for SD-WAN in the Asia-Pacific region.
| Feature | Vendor/Provider Support |
|---|---|
| Partnered SD-WAN Vendors | VMware (VeloCloud) |
| Integrated Security Features | Dynamic key encryption at the packet level ensures end-to-end data security across all links. |
| Cloud and Multi-Cloud Integration | Integrations with private, public and hybrid cloud environments, facilitated by strategically deployed gateways across Australia. |
| Cost Efficiency | Utilises multiple links, including low-cost broadband and 4G, to create a faster, more reliable connection, reducing reliance on expensive MPLS circuits and cutting operational expenses. |
| Support for Cellular Connectivity | 4G and LTE supported for resiliancy and backup. |
| Deployment Models Supported | Offers flexible deployment options, including on-premises, hybrid and cloud-based SD-WAN solutions. |
| Performance Guarantees or SLAs | Provides a network uptime guarantee of over 99.9%, backed by a service level agreement. |
| Support and Training Options | Offers 24/7 local support with a team that answers 95% of calls within one minute. Further to this, they provide personalised training sessions to assist customers in adopting and managing the SD-WAN solution effectively. |
| Target-Market Customers | Suitable for Finance, Healthcare, Retail, Manufacturing, Education, Government, Technology, Transportation, Energy and Telecommunications. |
TPx Communications

VMware VeloCloud Fortinet HPE Aruba EdgeConnect North America
TPx Communications is a leading nationwide managed services provider in the United States, with over five years of experience in the field, and serving 50,000 customers across the US with upwards of 15,000 edges under management.
As an early adopter (2015) of VMware SD-WAN technology, TPx has developed expertise in establishing effective business policies for a wide range of industries and this was showcased on Vertical Systems Group's U.S. Carrier Managed SD-WAN Leaderboard.
| Feature | Vendor/Provider Support |
|---|---|
| Partnered SD-WAN Vendors | TPx partners with VMware VeloCloud, Fortinet and HPE Aruba EdgeConnect |
| Integrated Security Features | Integrated security measures include VPN encryption and next-generation firewall (NGFW) capabilities. |
| Cloud and Multi-Cloud Integration | TPx's SD-WAN integrates with leading cloud platforms (AWS, Azure and Google Cloud), offering direct cloud access and optimised data paths to applications, data centres and the cloud. |
| Cost Efficiency | By leveraging economical bandwidth options and eliminating the need for expensive MPLS circuits. |
| Support for Cellular Connectivity | TPx offers SD-WAN over 4G/LTE as primary, secondary and redundant options. |
| Deployment Models Supported | TPx provides flexible deployment options, including on-premises, hybrid and fully cloud-based SD-WAN solutions. |
| Performance Guarantees or SLAs | TPx offers SLAs backed by a 100-percent uptime guarantee for UCaaS when paired with their managed SD-WAN solution. |
| Support and Training Options | TPx provides 24/7 helpdesks, dedicated account managers and online training resources. |
| Target-Market Customers | TPx's SD-WAN solutions are suitable for various sectors, including finance, healthcare, retail, manufacturing, education, government, technology, transportation, energy and telecommunications. |
MetTel

VMware VeloCloud North America
MetTel currently delivers SD-WAN as a fully managed service across North America using its own cloud network with 20 data centres and points of presence (PoPs). MetTel has established relationships with approximately 120 carriers through interconnections or wholesale relationships and has recently become an authorised Starlink reseller to extend its managed network services globally.
| Feature | Vendor/Provider Support |
|---|---|
| Partnered SD-WAN Vendors | MetTel has partnered with VMware VeloCloud. |
| Integrated Security Features | MetTel's SD-WAN integrates their own stateful, context-aware next-generation firewalls (NGFWs) and segmentation capabilities for communications between sites without ever leaving the MetTel network. |
| Cloud and Multi-Cloud Integration | The solution offers private connections to popular cloud SaaS/IaaS providers, including AWS, Azure, Salesforce and over 60 other top application providers. |
| Cost Efficiency | By combining existing and available circuits such as DSL, LTE and 4G, MetTel's SD-WAN reduces reliance on expensive MPLS circuits. |
| Support for Cellular Connectivity | MetTel's SD-WAN supports 4G and LTE connectivity, providing redundancy capabilities. |
| Deployment Models Supported | MetTel offers flexible deployment options, including on-premises, hybrid and fully cloud-based SD-WAN solutions. |
| Performance Guarantees or SLAs | Whilst MetTel offers sub-second blackout and brownout protection capabilities, they do not offer direct SLAs for their managed SD-WAN. |
| Support and Training Options | MetTel provides dedicated response teams alongside AI to detect incidents, as well as offering educational webinars. |
| Target-Market Customers | MetTel's SD-WAN solutions are suitable for various sectors, including finance, healthcare, retail, manufacturing, education, government, technology, transportation, energy and telecommunications. |
NTT Communications

Cisco Catalyst Cisco Meraki HPE Aruba EdgeConnect North America Latin America Europe Asia-Pacific
NTT Communications is a global telecommunications provider that has been recognised as launching the world's first SD-WAN platform with coverage spanning over 190 countries.
NTT Communications operates a 100% software-defined network infrastructure and maintains 75+ local cloud centres worldwide for optimised network, mobility and security services.
| Feature | Vendor/Provider Support |
|---|---|
| Partnered SD-WAN Vendors | NTT Communications partners with Cisco Catalyst, Cisco Meraki and HPE Aruba EdgeConnect. |
| Integrated Security Features | NTT offers Secure Web Gateways located at over 75 globally distributed Local Cloud Centers (LCCs), providing Web URL filtering, firewall protection, intrusion prevention and malware detection reporting. |
| Cloud and Multi-Cloud Integration | NTT's SD-WAN supports major cloud providers, including Amazon Web Services (AWS), Microsoft Azure and Oracle Cloud. |
| Cost Efficiency | By supporting a mix of network connectivity options such as Broadband, Wireless and 4G/LTE, NTT's SD-WAN solutions allow businesses to reduce reliance on expensive MPLS circuits. |
| Support for Cellular Connectivity | NTT supports both 4G and LTE to provide redundancy and enable mobile workforces. |
| Deployment Models Supported | NTT offers flexible deployment options, including on-premises, hybrid and fully cloud-based SD-WAN solutions. |
| Performance Guarantees or SLAs | NTT Com provides a guaranteed bandwidth SLA and guarantees 99.999% network access using MPLS-TP. Further to this NTT offers SLAs for delay of provision, failure recovery, failure notification and duplicate failures. |
| Support and Training Options | NTT provides support through its Global Operation Centers which serve as the single point of contact for all services in the SD-WAN platform, however they no longer offer courses on SD-WAN. |
| Target-Market Customers | NTT's SD-WAN solutions are suitable for various industries, including Finance, Healthcare, Retail, Manufacturing, Education, Government, Technology, Transportation, Energy and Telecommunications. |
Orange Business Services

VMware VeloCloud Cisco Catalyst Fortinet Palo Alto Prisma Latin America Europe Asia-Pacific
Orange Business is the Orange Group entity dedicated to businesses and organisations - boasting the number 1 voice and data network worldwide, 70+ cloud data centres and 50+ partnerships with technologies providers.
Orange Business leverages AI-driven networking capabilities and provides unified network solutions that combine SD-WAN with SD-LAN, reinforced by 4G/5G connectivity. Recently, they launched SD-WAN Essentials, a co-managed solution that provides businesses with control, reliability, performance, application-level routing, and security features.
| Feature | Vendor/Provider Support |
|---|---|
| Partnered SD-WAN Vendors | Orange Business Services partners with VMware VeloCloud, Cisco Catalyst, Fortinet and Palo Alto Networks Prisma. |
| Integrated Security Features | Orange's managed SD-WAN solutions offer Next-Generation Firewall (NGFW), secure web gateways and encrypted VPN tunnels. |
| Cloud and Multi-Cloud Integration | Securely accesses cloud resources with multi-cloud connectivity, with support for major public providers. |
| Cost Efficiency | Utilises cost-effective connectivity options, such as broadband and LTE, reducing reliance on expensive MPLS circuits. |
| Support for Cellular Connectivity | Supports LTE and 5G connectivity. |
| Deployment Models Supported | Offers on-premises, hybrid, and fully cloud-based SD-WAN options. |
| Performance Guarantees or SLAs | Orange provides clear SLAs that guarantee performance and connectivity for their SD-WAN services, even in remote locations. These include Site Availability, site Device Availability, EMS Availability, Guaranteed Time to Repair, Defined Time to Repair. |
| Support and Training Options | Orange offers global support through 5 major Service Centers located in Rio, Cairo, Paris, New Delhi and Mauritius, with support in 32 different languages and access to 500+ consultants and 800+ ITIL certified experts to assist with technical issues. Oran |
| Target-Market Customers | Orange's Target Markets include Finance, Healthcare, Retail, Manufacturing, Education, Government, Technology, Transportation, Energy and Telecommunications. |
Singtel

Fortinet HPE Aruba EdgeConnect Asia-Pacific
Singtel is Asia's leading communications technology group, providing services for network deployment, backed by 24/7 technical support and SLA-guaranteed performance. Singtel has a significant presence across Asia, Australia and Africa, serving over 760 million mobile users in 21 countries.
| Feature | Vendor/Provider Support |
|---|---|
| Partnered SD-WAN Vendors | Singtel partners with Fortinet and HPE Aruba EdgeConnect for its managed SD-WAN offerings. |
| Integrated Security Features | Singtel's SD-WAN solutions incorporate security measures such as integrated firewalls, antivirus protection, intrusion prevention systems (IPS), web filtering, and data encryption. |
| Cloud and Multi-Cloud Integration | Singtel's SD-WAN service enables integration with public cloud platforms directly. |
| Cost Efficiency | By leveraging hybrid networking, including both MPLS and internet connections, Singtel's SD-WAN optimises bandwidth usage and reduces reliance on expensive circuits. |
| Support for Cellular Connectivity | Singtel supports both 4G and LTE for remote locations or redundancy. |
| Deployment Models Supported | Singtel offers flexible deployment options, including on-premises, hybrid and cloud-based SD-WAN solutions. |
| Performance Guarantees or SLAs | Provides SLA-guaranteed network performance backed by a dedicated business-grade network. |
| Support and Training Options | Singtel does not offer direct SLAs or training programs, however they do offer partnership assistance to help enterprises define requirements, assess needs and discuss migration strategies. Further to this, Singtel offers 24/7 proactive monitoring and sup |
| Target-Market Customers | Singtel's SD-WAN solutions are suitable for various sectors, including finance, healthcare, retail, manufacturing, education, government, technology, transportation, energy and telecommunications. |
Spectrum Enterprise

Nokia Nuage Networks Cisco Catalyst Fortinet Netcracker Cisco Meraki North America
First announcing the national rollout of its Managed SD-WAN service in March 2019, Spectrum Enterprise offers managed SD-WAN services via their next-generation software-defined networking and network function virtualisation platform, that is integrated into their own fibre network across the United States.
By utilising their fibre network, Spectrum offers highly available, scalable and geo-redundant connectivity, enabling efficient delivery of high-performance WAN solutions with low-latency access from any client location.
In 2019, Spectrum Enterprise received the SD-WAN Implementation Award for its work with the Town of Addison, Texas, which served as an early adopter of the service.
| Feature | Vendor/Provider Support |
|---|---|
| Partnered SD-WAN Vendors | Spectrum Enterprise partners with Nokia Nuage Networks, Cisco Catalyst, Fortinet, Cisco Meraki and Netcracker for its SD-WAN offerings. |
| Integrated Security Features | Offers security measures such as firewalls and unified threat management (UTM), URL content filtering and intrusion prevention. |
| Cloud and Multi-Cloud Integration | Spectrum Enterprise's SD-WAN solution integrates major public cloud platforms, including AWS, Azure and Google Cloud. |
| Cost Efficiency | The solution leverages various connectivity options, such as broadband and LTE, allowing businesses to optimise costs by selecting the most appropriate and cost-effective transport types. Additionally, the managed service model reduces the need for signif |
| Support for Cellular Connectivity | Spectrum Enterprise's Managed SD-WAN service supports cellular connectivity through LTE integration. The service can incorporate multiple 4G LTE connections into the WAN transport mix, allowing for packet-based link bonding and dynamic path control across |
| Deployment Models Supported | Spectrum's managed SD-WAN solution offers flexible deployment models, including internet-based SD-WAN and hybrid configurations that integrate with existing Ethernet services. |
| Performance Guarantees or SLAs | Spectrum offers a 100% network uptime guarantee SLA, with round-the-clock US-based support and SLAs for metrics such as uptime, latency and packet delivery. |
| Support and Training Options | The service includes white-glove installation, a premium service that includes the delivery, assembly, and installation of a product, as part of the implementation process, |
| Target-Market Customers | Spectrum Enterprise's managed SD-WAN solutions cater to various industries including finance, healthcare, retail, manufacturing, education, government, technology, transportation, energy and telecommunications. |
Sprint

VMware VeloCloud Versa Networks Cisco Meraki North America Latin America Europe Asia-Pacific
Sprint Networks was the first company to introduce SD-WAN to the Pacific region. Nowadays, Sprint's SD-WAN coverage encompasses more than 100 countries globally, offering three SD-WAN solutions: SD-WAN Complete, SD-WAN Complete with Co-Management and SD-WAN Service, making use of Cisco Meraki, Versa Networks and VMware VeloCloud's SD-WAN solutions.
SD-WAN Complete offers a fully managed solution with end-to-end support, while SD-WAN Complete with Co-Management allows enterprises to retain some control over policy configurations. SD-WAN Service, on the other hand, provides network optimisation without full management, catering to organisations that prefer a more hands-on approach.
| Feature | Vendor/Provider Support |
|---|---|
| Partnered SD-WAN Vendors | Sprint partners with VMware VeloCloud, Versa Networks and Cisco Meraki. |
| Integrated Security Features | Sprint's SD-WAN integrates security measures including Next-Generation Firewall (NGFW) and Unified Threat Management (UTM). |
| Cloud and Multi-Cloud Integration | The solution supports integrations with various cloud platforms, offering direct cloud on-ramps. |
| Cost Efficiency | By utilising a combination of MPLS and broadband internet connections, Sprint's SD-WAN optimises bandwidth usage, potentially lowering operational expenses. |
| Support for Cellular Connectivity | The SD-WAN solution supports LTE/5G connectivity, providing redundancy and enabling remote or mobile scenarios. |
| Deployment Models Supported | Sprint offers flexible deployment options, including on-premises, cloud-based and hybrid models. |
| Performance Guarantees or SLAs | Sprint offers SLAs for each of Network Node-to-Node, End-to-End and Managed SLAs for fulfillment within 24 hrs. |
| Support and Training Options | Whilst Sprint doesn't offer training programs, Sprint provides 24/7 network monitoring and general support. |
| Target-Market Customers | Sprint's SD-WAN solutions are suitable for various sectors, including finance, healthcare, retail, manufacturing, education, government, technology, transportation, energy and telecommunications. |
Tata Communications

Versa Networks Tata IZO North America Europe Middle East & Africa Asia-Pacific
Tata Communications is a leading Indian telecommunications company that provides global network services. The company has successfully implemented SD-WAN projects in over 5,000 locations across 120+ countries, managing over 3,000 customer SD-WAN sites worldwide. Most recently, Tata Communications launched a unified Hosted Secure Access Service Edge (SASE) solution that combines SD-WAN with Secure Service Edge (SSE) capabilities. Tata also offers its own IZO SD-WAN, a managed solution that serves over 130 countries.
| Feature | Vendor/Provider Support |
|---|---|
| Partnered SD-WAN Vendors | Tata collaborates with Versa Networks, as well as offering their own Tata IZO SD-WAN. |
| Integrated Security Features | Tata's managed SD-WAN incorporates advanced security measures such as next-generation firewall (NGFW), secure web gateways, and micro-segmentation. |
| Cloud and Multi-Cloud Integration | Tata Communications' SD-WAN integrates seamlessly with major cloud platforms such as AWS, Azure, Google Cloud, IBM, Alibaba and Oracle. |
| Cost Efficiency | The solution leverages existing internet connections, reducing reliance on expensive MPLS circuits. It also offers a fully managed service with a single SLA, simplifying management and potentially lowering operational costs. |
| Support for Cellular Connectivity | Tata Communications' SD-WAN supports LTE and 5G connectivity, providing redundancy and ensuring continuous connectivity in remote or mobile scenarios. |
| Deployment Models Supported | The solution supports various deployment models, including on-premises, hybrid and fully cloud-based options. |
| Performance Guarantees or SLAs | Tata offers end-to-end Service Level Agreement (SLA) guarantees for its internet-based WAN and uptime guarantees as part of their SLA framework. |
| Support and Training Options | Customers have access to 24/7 support, dedicated account managers and online training resources. |
| Target-Market Customers | The solution is suitable for various sectors, including finance, healthcare, retail, manufacturing, education, government, technology, transportation, energy and telecommunications. |
Telefónica

Nokia Nuage Networks Latin America Europe
Telefónica is a Spanish multinational telecommunications company headquartered in Madrid. Telefónica has implemented multiple SD-WAN solutions, including partnerships with Nokia's Nuage Networks for virtualized network services.
The partnership began in 2017 when Telefónica selected Nuage Networks' Virtualised Network Services (VNS) platform to deliver automated end-to-end services to thousands of enterprise customers. This enabled Telefónica to offer self-service portals for customers to order and customise their network services.
As of 2024, the partnership has further improved through the integration of Nokia's Network Exposure Function (NEF) in Spain, leveraging Nokia's Network as Code platform and the development of private 5G network capabilities for Spanish businesses.
| Feature | Vendor/Provider Support |
|---|---|
| Partnered SD-WAN Vendors | Telefónica partners with Nokia Nuage Networks. |
| Integrated Security Features | Telefónica's SD-WAN solutions incorporate security measures such as Next-Generation Firewall (NGFW), Secure Access Service Edge (SASE) and Zero Trust Network Access (ZTNA). |
| Cloud and Multi-Cloud Integration | The solutions offer seamless integration with major cloud platforms, supporting multi-cloud environments. They provide direct cloud on-ramps and utilise private backbones. |
| Cost Efficiency | By leveraging low-cost broadband options and consolidating network functions, Telefónica's SD-WAN solutions help reduce reliance on expensive MPLS circuits. |
| Support for Cellular Connectivity | The solutions support LTE and 5G connectivity, adding redundancy, increasing deployment flexibility and ensuring reliable connectivity in remote or mobile scenarios. |
| Deployment Models Supported | Telefónica offers flexible deployment models, including on-premises, hybrid, and fully cloud-based SD-WAN options. |
| Performance Guarantees or SLAs | Telefonica offers multiple guarantees, including end-to-end traffic guarantees and transit through the TGS International Network, as well as global SLAs. |
| Support and Training Options | Telefónica provides full project management and deployment support. |
| Target-Market Customers | Telefónica's SD-WAN solutions are suitable for various sectors, including Finance, Healthcare, Retail, Manufacturing, Education, Government, Technology, Transportation, Energy and Telecommunications |
Telia

Cisco Catalyst Nokia Nuage Networks North America Europe Asia-Pacific
Telia's managed SD-WAN services allow enterprises to attach their WAN overlay to Telia Carrier's backbone internet network. For security integration with their SD-WAN offerings, Telia has existing relationships with Fortinet and Check Point.
This has led to Telia being recognised by Vertical Systems Group's SD-WAN Coverage Analysis leaderboard, who ranked Telia for their Global Provider SD-WAN.
| Feature | Vendor/Provider Support |
|---|---|
| Partnered Vendors | Telia partners with both Cisco Catalyst and Nokia Nuage Networks for SD-WAN. |
| Integrated Security Features | Telia's SD-WAN provides firewall for direct internet access from offices. |
| Cloud and Multi-Cloud Integration | The service integrates seamlessly with leading cloud platforms such as Azure, AWS and Google Cloud. |
| Cost Efficiency | Telia's SD-WAN allows the use of both private (DataNet) and internet connections flexibly at the same location. This enables organisations to reserve private connections for critical traffic while utilising the internet for less important traffic, optimis |
| Support for Cellular Connectivity | Telia supports both LTE and 5G, which is essential for remote or mobile locations. |
| Deployment Models Supported | Telia offers both fully managed and co-managed SD-WAN services. |
| Performance Guarantees or SLAs | The service includes a 24-hour service level for customer devices, ensuring predictable service levels. |
| Support and Training Options | Telia provides full support and 24/7 monitoring of SD-WAN edge devices, including configuration, change request management, and a user-friendly customer portal. |
| Target-Market Customers | Telia is well-designed for Finance, Healthcare, Retail, Manufacturing, Education, Government, Technology, Transportation, Energy and Telecommunications markets. |
Telstra

Cisco Meraki Cisco Catalyst VMware VeloCloud Asia-Pacific
Telstra is Australia's largest telecommunications company and one of the top 20 telecommunications providers globally. Telstra provides fully managed services including project management, design, provisioning and maintenance of network infrastructure with Service Level Agreements (SLAs) for performance and uptime
Telstra's SD-WAN offering combines Australia-wide gateways, as well as partnerships with Cisco Meraki, Cisco Catalyst and VMware Velocloud in order to meet varied customer requirements.
| Feature | Vendor/Provider Support |
|---|---|
| Partnered Vendors | Telstra partners with Cisco Meraki, Cisco Catalyst and Vmware VeloCloud for SD-WAN. |
| Integrated Security Features | Their solution integrates Next-Generation Firewall (NGFW), Zero Trust Network Access (ZTNA) and advanced threat protection. |
| Cloud and Multi-Cloud Integration | Direct cloud on-ramps to AWS, Azure, and Google Cloud. Uses Telstra’s private backbone to optimise cloud access. |
| Cost Efficiency | Reduces reliance on MPLS by leveraging broadband and optimised routing. Offers simplified licensing and bundled managed services to lower operational costs. |
| Support for Cellular Connectivity | Provides LTE and 5G support for backup and primary connectivity in remote or mobile deployments. |
| Deployment Models Supported | Offers on-premises, hybrid, and cloud-based SD-WAN deployments. |
| Performance Guarantees or SLAs | Provides SLAs covering uptime and latency guarantees. |
| Support and Training Options | 24/7 technical support, dedicated account managers and online training resources. |
| Target-Market Customers | Telstra focuses on Finance, Healthcare, Retail, Manufacturing, Education, Government, Technology, Transportation, Energy and Telecommunications markets. |
Verizon

Cisco Catalyst Cisco Meraki Versa Networks VMware VeloCloud HPE Aruba EdgeConnect Fortinet North America Latin America Europe Middle East & Africa Asia-Pacific
Verizon offers a wide range of managed SD-WAN solutions through partnerships with major vendors such as Cisco, VMware, Fortinet and Versa Networks. Their managed SD-WAN services focus on security, cloud connectivity and global enterprise networking. Verizon integrates SD-WAN with its private network services and provides security features, such as Zero Trust frameworks and AI-powered network analytics for proactive issue resolution.
| Feature | Vendor/Provider Support |
|---|---|
| Partnered Vendors | Verizon partners with Cisco Catalyst, Cisco Meraki, Versa Networks, VMware VeloCloud, HPE Aruba EdgeConnect and Fortinet. |
| Integrated Security Features | Verizon adds managed security services, including built-in Next-Generation Firewall (NGFW), Zero Trust Network Access (ZTNA), and Secure Web Gateway (SWG). Verizon also offers managed threat detection and response services. |
| Cloud and Multi-Cloud Integration | Provides direct cloud connectivity to AWS, Azure, and Google Cloud via private backbones and cloud on-ramps. Further to this, Verizon supports multi-cloud orchestration. |
| Cost Efficiency | Offers flexible pricing models, including pay-as-you-go and subscription-based services. Streamlines operations by integrating multiple network functions into one solution, reducing hardware dependencies. |
| Support for Cellular Connectivity | Supports LTE and Verizon's private 5G for SD-WAN failover, primary connectivity and remote deployments |
| Deployment Models Supported | Supports on-premises, hybrid, and cloud-based SD-WAN deployments. |
| Performance Guarantees or SLAs | Provides performance SLAs with uptime guarantees and latency thresholds. |
| Support and Training Options | 24/7 customer support, dedicated account managers and managed service options. Offers training resources, including online portals and guided onboarding. |
| Target-Market Customers | Verizon focuses on Finance, Healthcare, Retail, Manufacturing, Government, Technology, Transportation, Energy and Telecommunications markets. |
Virgin Media Business

Versa Networks Fortinet Cisco Meraki Europe
Virgin Media Business provides managed SD-WAN services with a focus on high-speed broadband and resilient connectivity. Virgin Media primarily partners with Versa Networks and Fortinet for SD-WAN solutions, offering fully managed network services that cater to either secure cloud connectivity or strict security requirements.
| Feature | Vendor/Provider Support |
|---|---|
| Partnered Vendors | Virgin Media Business has partnered with Versa Networks, Fortinet and Cisco Meraki. |
| Integrated Security Features | Virgin Media offers next-generation security features such as stateful and next-generation firewalls, DNS filtering, URL filtering and antivirus protection. |
| Cloud and Multi-Cloud Integration | Offers seamless integration with major cloud platforms, enabling direct access to services such as Azure and AWS. |
| Cost Efficiency | Utilises a hybrid network approach, combining private and public networks to optimise connectivity and reduce reliance on expensive circuits. |
| Support for Cellular Connectivity | Supports LTE connectivity, providing redundancy and enabling both remote and mobile workforces. |
| Deployment Models Supported | Offers flexible deployment options, including on-premises, hybrid and cloud-based models. |
| Performance Guarantees or SLAs | Provides service level agreements (SLAs), tailored to the specific infrastructure and needs of the company. |
| Support and Training Options | Offers 24/7 monitoring, management and access to a team of consultants, engineers, project leaders and service managers for support. |
| Target-Market Customers | Suitable for various sectors including finance, healthcare, retail, manufacturing, education, government, technology, transportation, energy and telecommunications. |
Vodafone

Cisco Meraki VMware VeloCloud Juniper Networks Contrail North America Europe Middle East & Africa Asia-Pacific
Vodafone provides managed SD-WAN solutions through partnerships with Cisco Meraki, VMware VeloCloud and Juniper Networks. Vodafone’s SD-WAN is tailored for enterprises requiring global coverage and 5G-ready networking, which is backed by Vodafone’s extensive fibre and mobile network infrastructure.
| Feature | Vendor/Provider Support |
|---|---|
| Partnered Vendors | Vodafone partners with leading SD-WAN vendors, including Cisco, VMware, Fortinet, and Juniper Networks. |
| Integrated Security Features | Vodafone's SD-WAN incorporates security measures such as Next-Generation Firewall (NGFW), Zero Trust Network Access (ZTNA) and Secure Access Service Edge (SASE) frameworks. |
| Cloud and Multi-Cloud Integration | The solutions offer seamless integration with major cloud platforms such as AWS, Azure, Google Cloud, IBM and Alibaba. |
| Cost Efficiency | Vodafone's SD-WAN leverages cost-effective broadband options, consolidates network functions, and offers straightforward licensing models. This approach reduces reliance on expensive MPLS circuits and operational expenses. |
| Support for Cellular Connectivity | The SD-WAN solutions support LTE and 5G connectivity, adding redundancy and enabling remote workforces. |
| Deployment Models Supported | Vodafone offers flexible deployment models, including on-premises, hybrid and fully cloud-based SD-WAN options. |
| Performance Guarantees or SLAs | The solutions come with performance Service Level Agreements (SLAs), including uptime guarantees and latency thresholds. |
| Support and Training Options | Vodafone provides customer support, including 24/7 helpdesks, dedicated account managers and online training resources. |
| Target-Market Customers | Vodafone's SD-WAN solutions are tailored for various sectors, including Finance, Healthcare, Retail, Manufacturing, Education, Government, Technology, Transportation, Energy and Telecommunications. |
Windstream

VMware VeloCloud Fortinet Cato Networks North America
Windstream offers managed SD-WAN solutions through partnerships with VMware VeloCloud and Fortinet. Their SD-WAN services focus on optimising bandwidth utilisation, improving network security and ensuring high availability for businesses operating across multiple locations. Windstream integrates SD-WAN with its proprietary Kinetic Business fibre network, providing a hybrid WAN strategy for enterprises requiring secure, scalable and high-speed connectivity.
| Feature | Vendor/Provider Support |
|---|---|
| Partnered Vendors | Windstream partners with leading SD-WAN vendors, including Cisco, VMware and Fortinet |
| Integrated Security Features | Windstream's SD-WAN incorporates security measures such as Next-Generation Firewall (NGFW), Zero Trust Network Access (ZTNA) and Secure Access Service Edge (SASE) frameworks. |
| Cloud and Multi-Cloud Integration | The solutions offer seamless integration with major cloud platforms such as AWS, Azure, Google Cloud, IBM and Alibaba. |
| Cost Efficiency | Vodafone's SD-WAN leverages cost-effective broadband options, consolidates network functions, and offers straightforward licensing models. This approach reduces reliance on expensive MPLS circuits and operational expenses. |
| Support for Cellular Connectivity | The SD-WAN solutions support LTE and 5G connectivity, adding redundancy and enabling remote workforces. |
| Deployment Models Supported | Vodafone offers flexible deployment models, including on-premises, hybrid and fully cloud-based SD-WAN options. |
| Performance Guarantees or SLAs | The solutions come with performance Service Level Agreements (SLAs), including uptime guarantees and latency thresholds. |
| Support and Training Options | Vodafone provides customer support, including 24/7 helpdesks, dedicated account managers and online training resources. |
| Target-Market Customers | Vodafone's SD-WAN solutions are tailored for various sectors, including Finance, Healthcare, Retail, Manufacturing, Education, Government, Technology, Transportation, Energy and Telecommunications. |
Zayo Group

Versa Networks VMware VeloCloud Palo Alto Networks North America Europe
Zayo Group delivers managed SD-WAN services with a focus on fibre-optic network infrastructure and cloud connectivity. Their SD-WAN platform is built to provide secure, low-latency networking for businesses relying on hybrid and multi-cloud environments. Zayo’s SD-WAN solutions integrate with their extensive metro and long-haul fibre networks, ensuring enterprises benefit from high-performance, resilient network connectivity with real-time analytics and intelligent traffic management.
| Feature | Vendor/Provider Support |
|---|---|
| Partnered Vendors | Zayo partners with leading SD-WAN vendors, including Versa, VMware and Palo Alto Networks. |
| Integrated Security Features | Zayo SD-WAN incorporates security measures such as Next-Generation Firewall (NGFW), Zero Trust Network Access (ZTNA) and Secure Access Service Edge (SASE) frameworks. |
| Partnered Vendors | Zayo partners with Versa Networks, VMware VeloCloud and Palo Alto Prisma. |
| Integrated Security Features | Zayo's SD-WAN offers security measures such as Next-Generation Firewall (NGFW) capabilities and Zero Trust Network Access (ZTNA). |
| Cloud and Multi-Cloud Integration | The SD-WAN solution offers integration with leading cloud platforms, providing direct cloud on-ramps and utilising Zayo's private backbone. |
| Cost Efficiency | By leveraging low-cost broadband options and consolidating network functions, Zayo's SD-WAN solutions help reduce reliance on expensive MPLS circuits and cut operational expenses. |
| Support for Cellular Connectivity | Zayo's SD-WAN supports LTE/5G connectivity, adding redundancy and enabling remote workforces. |
| Deployment Models Supported | Zayo offers flexible deployment options, including on-premises, hybrid, and fully cloud-based SD-WAN solutions. |
| Performance Guarantees or SLAs | Zayo guarantees network uptime of 99.99% for on-net dark fiber and waves and 24x7x365 service assurance and real-time network monitoring, as well as Zayo's Network Operations Center (NOC) monitoring the network backbone round-the-clock. |
| Support and Training Options | Customers have access to 24/7 helpdesks, dedicated account managers and online training resources. |
| Target-Market Customers | Zayo's SD-WAN solutions are tailored for various sectors including Finance, Healthcare, Retail, Manufacturing, Education, Government, Technology, Transportation, Energy and Telecommunications. |