What is Network Segmentation?
| Network segmentation isolates network traffic or applications to prevent lateral movement for security. |
- What is Network Segmentation?
Network segmentation is the process of isolating network traffic, applications or data into their own subsections of the network. Often considered as a foundational security strategy, segmentation can be utilised to improve network performance and also to prevent lateral movement in the event of a breach.
Technological Overview
In traditional networks, there are two types of network segmentation, physical and logical/virtual.
With physical segmentations, networks are broken down into multiple physical sections or subnets. Each segment has its own firewall, wiring, switches and internet connections. This provides comprehensive isolation as the network segments are not inter-connected reducing the network plane where traffic and potential breaches may access the isolated segments.
Virtual segmentations are typically the more popular approach and utilises virtual local area networks (VLANs). VLANs are protecting by a common firewall and, due to not needing multiple sets of wiring to separate individual networks, provides a more flexible and cost-effective segmentation than physical.
However, as businesses are moving towards Software Defined Wide Area Network (SD-WAN) solutions, it is important to consider the ways that SD-WAN segments networks. Network segmentation has been adopted into many SD-WAN and SASE solutions and provides a shift from static VLAN to a dynamic, policy-based approach. Whilst VLANs are effective, SD-WAN mitigates their limitations in flexibility and cost-efficiency through easily configurable software configuration-based segmentations.
SD-WAN enables network segmentation through several methods:
- Path Isolation separates traffic onto different physical or logical paths based on application, user or security policies.
- Network traffic can also be separated at layers 3 and 4, where segmentation is done based on IP address, port, protocol or VLAN at the network and transport layer. Layer 7 can be used for application-aware segmentation. Isolation at layer 7 is based on deep packet inspection and application signatures.
By isolating traffic flows from each other, SD-WAN can route over links based on priority or security policies. This enables SD-WAN granular segmentation policies for routing priority traffic.
Benefits of Network Segmentation with SD-WAN and SASE
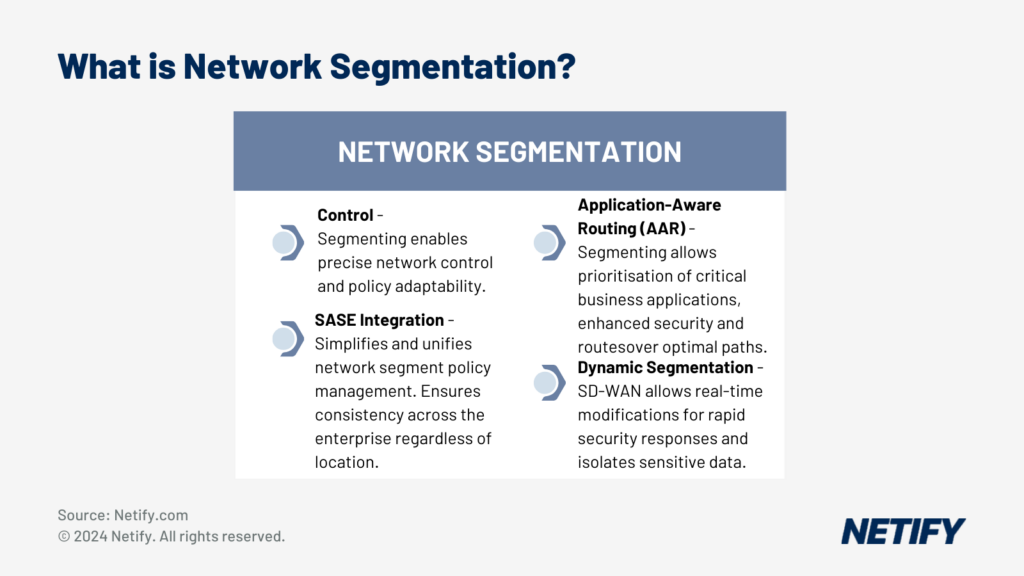
By using a policy-based approach, segmentation provides network administrators granular control over the network and the ability to quickly adapt policies depending on network requirements.
Dynamic segmentation enables adaptive security measures, as SD-WAN enables the segment to be changed on the fly and thus allows quick responses to potential threats. Sensitive sections of the network, when isolated through segmentation, can have granular security policies applied to minimise the effect of potential breaches.
Application Aware Routing is a key feature of SD-WAN, allowing business critical applications to be prioritised by isolating this traffic from less important traffic. This not only improves the security of the isolated traffic, but also improves the performance of network segments as this data can be sent over dedicated or more high-performing communication links.
As SASE provides a single unified management platform for both network and security policies across all endpoints, this reduces the complexity of implementation and maintenance of segmentation policies, ensuring consistent policies are enforced across the enterprise. SD-WAN seamlessly integrates with SASE, providing end-to-end security for segments.
Challenges and Considerations
When implementing SD-WAN network segmentation is important to consider the dynamic environment to which it is being implemented. Due to an increased adoption of the cloud and remote workforces, the need for highly dynamic network environments has increased. To meet the varying requirements of the network, it is therefore important that a segmentation strategy is created in order to adapt to changing network conditions and user behaviour. SD-WAN and SASE provide flexibility to the network, making it easier to segment and modify the network in response to network changes.
Another challenge is the interoperability of the network. Existing infrastructure can often be complex to integrate into SD-WAN for network segmentation. It is therefore important for organisations to consider vendors and find the most compatible SD-WAN solution for their network requirements in order to prevent potential bottlenecks.
Fresh Insights and Future Outlook
Artificial Intelligence (AI) and Machine Learning (ML) are increasing being used to assist with automated network segmentation. AI can automatically analyse the network traffic patterns, detect anomalies and adapt segmentation policies in real time in order to mitigate potential threats towards the network. AI can also analyse network telemetry and segment traffic over preferable links in order to optimise the performance of crucial applications, whilst also making the most efficient use of all available network links. This means that AI can intelligently change network segmentations in a self-adjusting manner to minimise downtime and prevent breaches.
Through the adoption of Zero Trust Network Access (ZTNA), constant verification and least privilege access is provided to users. The need to re-authenticated is introduced at every network segment, thus improving the security of the network.
Conclusion
Network Segmentation is an essential feature for ensuring the security and performance an organisations applications and traffic. Whilst physical segmentation provides complete isolation and virtual VLANs provide a reduced cost implementation, network segmentation through SD-WAN enables dynamic policy-based isolation of traffic. This not only enhances security through control access and rapid response capabilities buy also utilises segmentation for improving network efficiency and application performance. The integration of AI and ML further enhances these benefits, allowing networks to be reactive to network telemetry and potential threats.