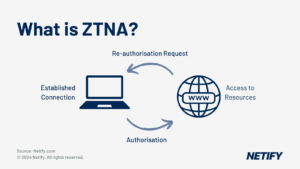
ZTNA (Zero Trust Network Access) is a security model focused on verifying every user and device before granting access to corporate applications, aiming to ensure secure, flexible access from anywhere, and gradually transitioning network architecture to a Zero Trust approach. 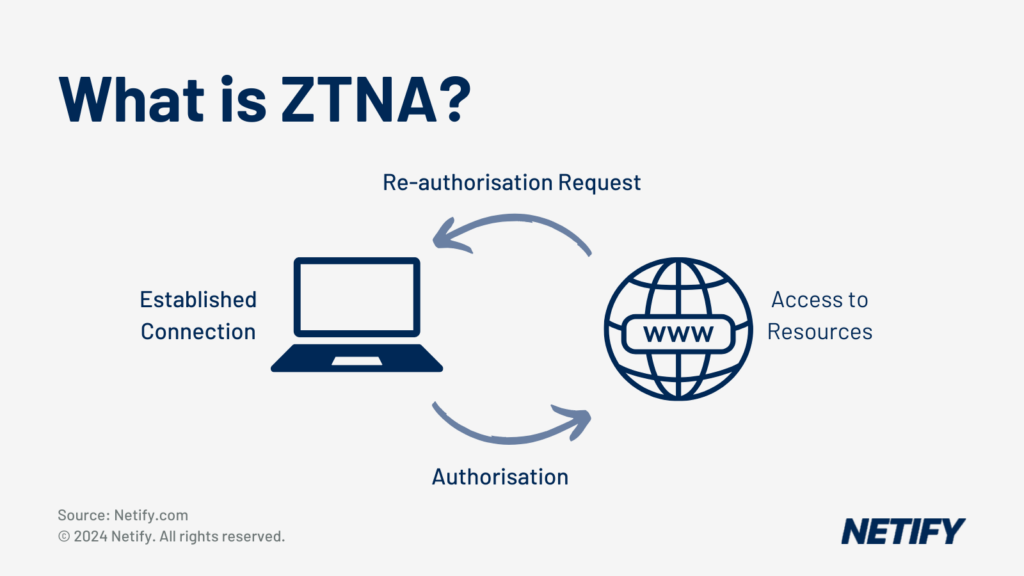
What is ZTNA?
The concept of Zero Trust was coined in 2010 by John Kindervag, with traction for the term skyrocketing in 2019 with Gartner’s definition of Zero Trust Network Access (ZTNA) as “A product or service that creates an identity and context-based, logical access boundary around an application or set of applications.” ZTNA is a shift in paradigm for network security. The traditional view is that devices and users within the network must be trusted but require verification of user identity, whereas, under ZTNA, this becomes “Never trust, always verify.” Zero Trust has since become a marketing buzzword, with vendors around the globe touting their standard solution “now with added Zero Trust features”. ZTNA is the network security “holy grail”, hence its rapid adoption by marketers. ZTNA promises the free, secure movement of internal and external network traffic by removing the security perimeter almost entirely and using assigned user identity credentials and context for authentication and authorisation.
This article will discuss ZTNA, its features, the hype, and how ZTNA can help you achieve your business goals.
The elusive true ZTNA solution
To dispel the myth surrounding ZTNA, we look to its name, particularly the misleading network access. ZTNA focuses on interoperability between applications and their end user rather than access to the corporate network. Ask any vendor or managed service provider (MSP) what ZTNA is, and no two will provide the same answer. At most, they will explain as vast as the ocean, as deep as a puddle, usually centring around its most straightforward form “Never trust, always verify.” The paradigm shift, as mentioned above, is a case of half-truths and marketing jargon. Zero Trust is possible, and with the march toward a Hybrid Cloud in the not-too-distant future, interoperability with resources external to the network, such as SaaS, IaaS, PaaS and Cloud services, will be more critical than ever.
The reason there is no true ZTNA solution lies in the fact that it is an ongoing process that ensures that the corporate security architecture aligns with the needs of the business strategy. Vendors and MSPs that offer ZTNA solutions provide features and services that will assist in the short-term and the overall long-term transition to a Zero Trust architecture. Zero Trust is not the simple paid quick-fix product or solution it is sometimes made out to be. However, ZTNA is a tangible framework that enables an organisation to take steps towards implementing a zero-trust model.
Zero Trust Network Access (ZTNA) within SASE - Zero Trust Network Access (ZTNA) within SASE
Why is ZTNA important?
In the contemporary workplace, where users expect to work from anywhere, ZTNA is the “magic bullet” that ensures that employees can securely access corporate resources anytime, anywhere. ZTNA aims to reduce the complexity between a combination of technologies and processes, enabling business and facilitating a unified experience by ensuring minimal differentiation between security postures for the intranet and the internet. This user and application-centric approach ensures that all network sessions follow business policies through authorisation, authentication and enforcing encrypted protocols only on the network. Zero Trust vendors and service providers help to address the contemporary challenges of inherent and excessive trust in users, devices, data and networks that remain from legacy network architectures, as well as combating the rising impact of breaches within a business.
The goal of ZTNA
A Zero Trust transition aims to enforce least-privilege access in every part of the network. This process is a slow, long-term metamorphosis of the network architecture that will require ongoing support. The technology to begin ZTNA adoption is available now and, when appropriately implemented, will enable business outcomes that were not previously available. ZTNA implementation cannot be a standalone add-on if the deployment is to be successful. It should be included in the network strategy from the ground up as it relies upon working synonymously with a “defence in depth” network security architecture.
An example of a Multi-Factor Authentication (MFA) provider for user/device identity verification.
What are the components of ZTNA?
ZTNA has three key components:
- User/application authentication
- Device authentication
- Trust
To achieve the required outcomes of these components, the Zero Trust Network model requires the following:
- Device directory
- Identity provider
- Policy evaluation service
- Access proxy
What comprises a modern ZTNA solution?
The key characteristics of a modern ZTNA solution are:
Data Loss Prevention
A ZTNA solution should support advanced Data Loss Prevention features such as exact data matching to prevent sensitive information from leaving the network through techniques like encryption on download or blocking.
Scalable Performance
Since ZTNA is responsible for connecting remote workers to corporate applications, a solution should be flexible and dependable to minimise unnecessary downtime. A solution hosted in the cloud can enable a business to leverage dynamic scaling, which allows resources to scale up or down when traffic spikes occur.
Granular Visibility and Reporting
Granular visibility and reporting allow for an in-depth view of the network and can assist in enabling security audits and demonstrating a commitment to regulatory requirements.
BYOD Deployment Options
Bring-Your-Own-Device (BYOD) deployment options allow businesses to let employees use unmanaged devices for work through agentless options, reducing the cost of investment in new equipment. ZTNA is also deployable with agent-based options for managed devices.
Advanced Threat Protection (ATP)
Leveraging Machine-Learning (ML) and Artificial Intelligence (AI), ATP uses threat prevention to protect the endpoints of an organisation from cyberattacks (including zero-day attacks) from sophisticated and advanced threat actors.
Integration with a comprehensive SASE offering
For an authentic Zero Trust security architecture, we must remove the traditional network edge to enable a unified security posture between the intranet and the internet. One of the most efficient ways to align your network and security architecture towards your Zero Trust goals is to implement ZTNA as part of a Secure Access Service Edge (SASE) solution from the same provider. Upgrading your infrastructure to a SASE architecture will help speed up your transition to Zero Trust and ensure that your ZTNA solution will natively integrate with the Secure Web Gateways (SWGs), Cloud Access Security Brokers (CASBs) and other SASE features offered by the vendor or managed service provider.
ZTNA Use Cases
| wdt_ID | wdt_created_by | wdt_created_at | wdt_last_edited_by | wdt_last_edited_at | Use Case | Description |
|---|---|---|---|---|---|---|
| 1 | hyelland | 21/10/2024 02:43 PM | hyelland | 21/10/2024 02:43 PM | Reduce Third-Party Risk | Third parties, such as contractors, often use unmanaged devices to access resources and receive overprivileged access. Secure the network by keeping the network invisible and providing access only to applications third parties are authorised to use. |
| 2 | hyelland | 21/10/2024 02:44 PM | hyelland | 21/10/2024 02:44 PM | VPN Alternative | Replace insecure and inefficient VPN access for remote users. Users get direct, encrypted access to applications without the need to backhaul through the data centre. |
| 3 | hyelland | 21/10/2024 02:44 PM | hyelland | 21/10/2024 02:44 PM | Accelerate M&A Integration | Easily and quickly manage network convergence and overlapping IPs to speed up the network integration following an acquisition or merger. |
| 4 | hyelland | 21/10/2024 02:45 PM | hyelland | 21/10/2024 02:45 PM | Secure Multicloud Access | With cloud services and applications increasing in popularity, ZTMA is key to securing multi-cloud and hybrid cloud access by strengthening the access controls required to use corporate applications and resources. |
ZTNA Deployment Options
ZTNA can be implemented in three ways. These are:
- Software-defined perimeter
- Network micro-segmentation
- Identity-aware proxy
The implementation method will depend on the area of the network deployed, and a business will likely use all three at some point in a broad network.
How to implement a Zero Trust Architecture
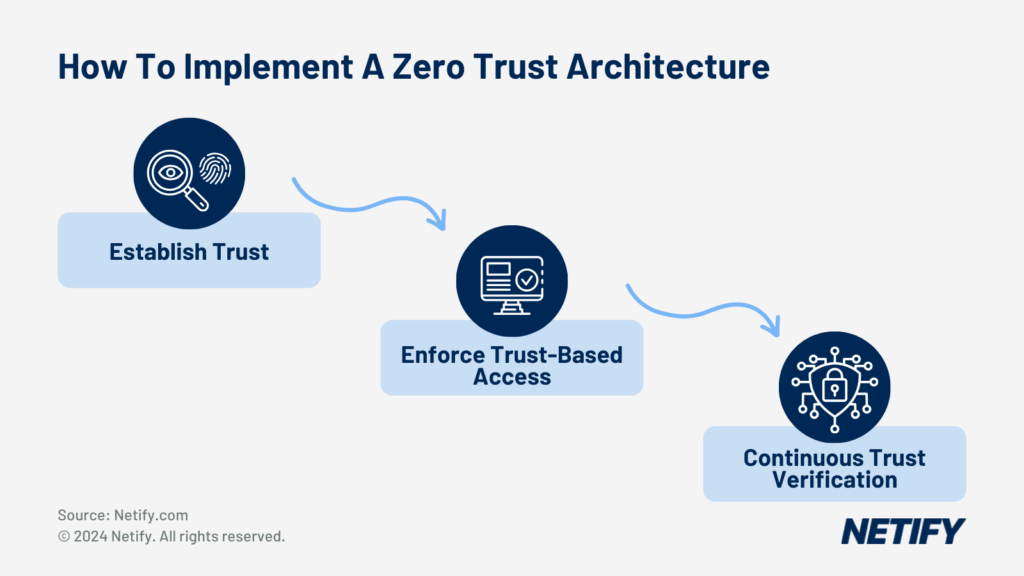
Establish Trust
Start by collecting flow data and telemetry. The collected data provides you with granular visibility into the network. Analysis of this data enables the discovery of assets and data on the network. Data protection requires knowing your network. By classifying assets and data, you can identify what network segments are business-critical key assets, hold sensitive data or are of high risk. Find and remediate insecure protocols and improve processes around user identity, such as multi-factor authentication (MFA), physical devices, e.g. USB, dongles etc. and remove compromised or redundant credentials. Making identity the new firewall requires an in-depth contextual understanding of both users and their devices. Whilst not essential, a User Entity and Behaviour Analytics (UEBA) solution may be helpful here. Making identity the control plane enables anomalies and discrepancies to be more easily identified. Establish who your users are and what resources they are authorised to access on the corporate network.
Enforce trust-based access
Now that trust has been established between the network, the users and their devices, admins can implement policies to ensure automated gating to applications and remediation based on device health. Gating ensures that resources are only available to users when their identity and device have been authenticated and meet business-defined data access policies. Access to resources should be least privilege with access decisions made in real-time, monitoring for policy violations and alert prioritisation for access requests for sensitive data. Logging and reporting should capture the state of identity, device, data and SaaS app during access requests to ensure compliance and assist with auditing. From here on out, admins should automate visibility into the network and trust verification, and we will be able to enforce the network only to use encrypted protocols.
Continuous trust verification
Now begins the ongoing support and the true paradox of Zero Trust. With the security perimeter removed, employees are free to work from anywhere, anytime, with the business reaping the benefits of increased productivity. However, for authentic Zero Access security architecture, everything on the network must be micro-segmented. No single asset should be able to be accessed by all users. Once the security architecture is built to support Zero Trust, this becomes easier as new assets can be added and segmented as needed. With the freedom permitted by Zero Trust comes the drawback that every network session must be authorised and authenticated with ongoing monitoring for behavioural changes that help to adjust the trust level of a user or device dynamically. In the end, though it is a balancing act, each business is unique, so their ZTNA implementation will be too. Companies must be able to efficiently and securely interact with the outside world without hindering business outcomes, so the extent of ZTNA implementation will vary widely depending on risk levels and requirements.
The Pillars of the Zero Trust Maturity Model
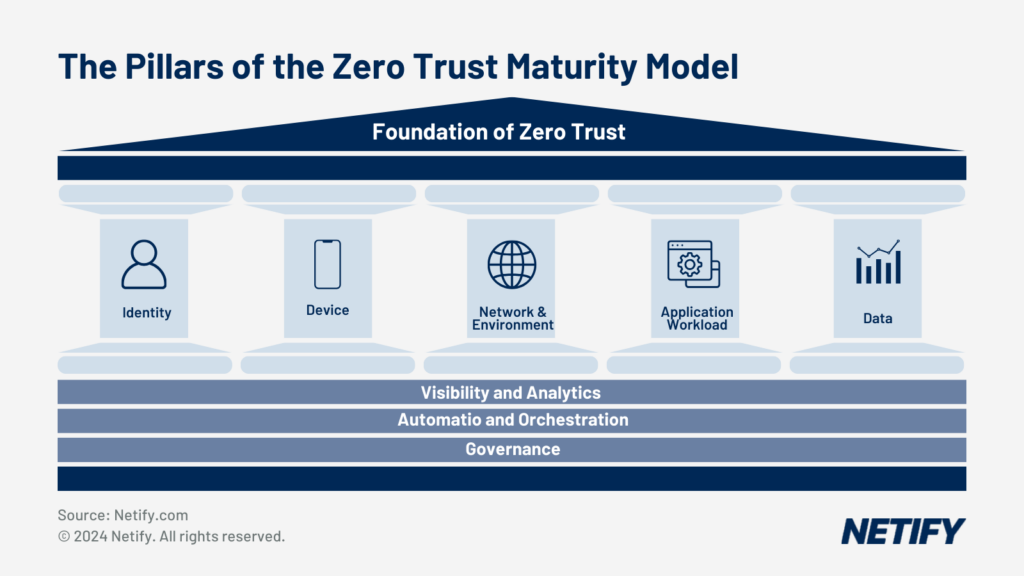
Figure 1: Foundation of Zero Trust1
- Identity: Hardening of access controls, such as Least Privilege, Dynamic, Centralised or Adaptive, to establish user trust.
- Device: Devices can be business-managed or Bring-Your-Own-Device (BYOD). Business devices should be secured and inventoried, with unauthorised devices being prevented from accessing corporate resources.
- Network/Environment: Establish trust-based access control on networks within an organisation’s management.
- Application Workload: Identify and mitigate internal and external threats by enforcing least access privilege, minimising the attack surface.
- Data: Data is the most important asset within the corporate network. We must know our network to protect it effectively. Using asset discovery, data discovery & classification, we gain visibility into what data must be protected and its flows.
There are three additional principles of Zero Trust that are not considered Pillars of ZTNA since they apply to all pillars. These are:
- Visibility & Analytics: Allows monitoring, logging and correlating activity throughout the network.
- Automation & Orchestration: The ability of a ZTNA solution to integrate with other IT network security solutions to ensure rapid isolation and mitigation of threats.
- Governance: A structure for Information Technology (IT) processes to align IT strategy with business strategy to ensure efficient and effective use of IT.
Benefits of a Zero Trust Network Model
- Improve the productivity of your employees by enabling them to securely and reliably work from anywhere.
- Provide conditional access to resources within the corporate network to reduce the size of the attack surface and enforce least privilege access controls to provide users with secure access to only the resources they require and avoid oversharing with third parties.
- Mitigate the impact of attacks involving compromised devices and stolen user credentials by preventing access to the network and restricting lateral movement.
Questions to ask a potential ZTNA vendor or managed service provider
- What ongoing support will you provide?
- Do you provide an Identity/Access proxy/Device directory/Policy evaluation service?
- Does your ZTNA form part of a broader SASE solution?
- Can you assist in the removal or isolation of legacy network components?
Summary
Any ZTNA solutions should be tailored to your business and gradually implemented alongside changes to network architecture to fulfil the requirements of the long-term business strategy. Consideration for business goals such as compliance requirements, enterprise mobility, reduction of infrastructure complexity and Hybrid Cloud readiness, as well as the ability to incorporate existing orchestration, security and monitoring tools, should be assessed when transitioning to a Zero Trust architecture. When adopting Zero Trust, IT decision-makers should advocate for change during the replacement or major upgrade of network components. Ideally, IT decision-makers should choose a ZTNA solution that is part of a complete SASE offering to minimise business disruption and maximise return on investment. Secure Web Gateways (SWGs), Cloud Access Security Brokers (CASBs) and ZTNA make up the foundation of SASE architectures. It is vital to remember that networks that fail to evolve will become susceptible to breaches over time. Implementing ZTNA is an ongoing process that can take years to complete. With a growing market of technologies for every niche requirement, there’s never been a better time to start your ZTNA transformation journey.
1This illustration was inspired by Figure 1 of the Cybersecurity and Infrastructure Security Agency (CISA): “Zero Trust Maturity Model”, (2021). https://www.cisa.gov/sites/default/files/publications/CISA%20Zero%20Trust%20Maturity%20Model_Draft.pdf