The retail industry faces challenged such as online threats, complex network integrations over multiple branches and insider vulnerabilities. SASE offers integrated solutions to ensure regulatory compliance, improve security and enable greater scalability to new branches. |

- Top CyberSecurity Challenges for Retail
If the latest cybersecurity headlines are giving your IT or SecOps teams a permanent case of shock and awe, there’s a good reason. Globally, the retail sector is one of the most frequently targeted, with retail sales in the US alone projected to top $5.2 trillion in 2022. In this article, we discuss the main challenges faced by IT teams.
A surge in e-commerce investments and online shoppers prompted by the pandemic has made online retail a more attractive prospect for would-be cybercrooks. Malicious insiders, negligent staff, and misconfigured or vulnerable software across networks, endpoints and POS devices have boosted the corporate attack surface in recent years.
So, what’s the latest news about cybersecurity in the retail sector? The SASE story provides a revealing profile of security problems and solutions.
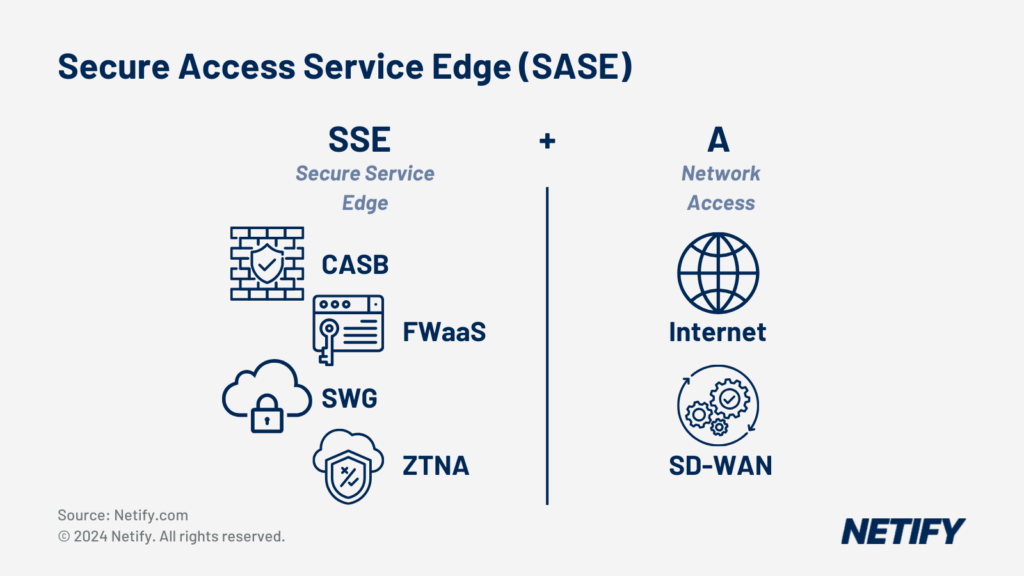
- Secure Access Service Edge (SASE) is SSE + SD-WAN (Access).
The Changing Reality in Retail Security
Retailers are digitising their operations to provide an efficient IT infrastructure and give customers a pleasant retail experience. But the new cloud-based approach to cybersecurity creates its own challenges.
The COVID-19 Pandemic
The pandemic has helped to transform retail organisations from the POS terminal to the back office. However, it’s also exposed retail operations to new cybersecurity risks, which can create an oversized impact on individual companies and the retail sector. Online sales as a percentage of total retail sales increased from 16 to 19 percent in 2020.
An Increase in Sophisticated and Damaging Cyberattacks
Traditionally, POS was the number-one target for data-hungry cyberattackers. The widespread adoption of EMV cards—which can’t be cloned as easily as stolen POS data—and new payment systems like Apple Pay push more malicious activity online. And there’s plenty of it. For example:
- Multi-directional attacks: Attacks originate increasingly from external and internal locations. Retailers are exposed at many spots of their IT infrastructures and employee turnover is high. Seasonal and temporary employees and many stores and distribution centres create points of insider vulnerability. And retailers outsource business processes such as marketing automation, customer databases, POS terminals and web search optimisation to third parties.
- More complex networks: Retailers want solutions that are easy to buy, deploy, maintain and troubleshoot. Faster application and service adoption, which makes online retail more complex, creates a growing attack surface in retail IT environments.
IT Cyberattack Solutions in Retail
There are no simple, IT-based solutions that address all retail IT security problems. However, next-generation hardware and software can drive down the cybersecurity risk of familiar and often costly problems.
New Cybersecurity Solutions to address challenges
These IT solutions (mostly platform-based services) use these technologies to secure retail operations:
- Artificial Intelligence-based Automation: AI-based data analytics have helped the e-commerce sector serve its customers more effectively and automate attack detection and response when cyberattacks occur. AI-driven solutions also improve threat intelligence methods and monitor changes in data and user behaviour.
- Real-time User Monitoring (RUM): Organisations need real-time visibility into customer interactions across channels and platforms. RUM merges front-end and back-end data to monitor the end-user experience, prioritise security issues and help organisations make faster, more accurate decisions.
- Pattern recognition-based fraud detection tools: Chargebacks, credential stuffing and Account Takeover (ATO) attacks have a negative effect on retail revenues. Many E-commerce platforms use machine learning to create flexible systems that process mountains of retail data, find hidden patterns in user and network behaviour, automate verification processes and improve the performance of legacy fraud detection solutions.
- Content security policy protection software: As cloud services grow, retailers use more third-party services, often with no understanding of vendor data and behaviour. Losing track of vendor data and activity can have dire consequences.
For example, members of Magecart and other digital skimming groups can damage or steal stored consumer data. These types of vulnerability can be approached with real-time Content Security Policy (CSP) software. CSP defends against the injection of malicious code by using clearly defined access permissions.
CSP effectively protects web applications against client-side vulnerabilities. However, its complexity and maintenance costs can deter widespread use.
- Security at the edge: Cloud-based security software that accommodates new users, technologies, products and services is on the rise. Security isn’t limited to monitoring what occurs at an organisation’s perimeter. Now, much of the security story is about the edge.
Edge computing is an extra layer of security, which helps reduce the risk and damage of attacks across a growing variety of threats. Its zero-trust security model supports agile, fast, and ‘always-on’ consumer activity.
Edge security replaces traditional e-commerce security measures. Its distributed network architecture helps prevent a complete business shutdown in case of a breach. The goal: disconnect only the node effected by an attack—before it spreads across the system.
SASE Solutions
As retail applications and services shift to the cloud, retailers need edge-to-edge solutions that combine SD-WAN connectivity, security, and application and data visibility functions throughout distributed networks.
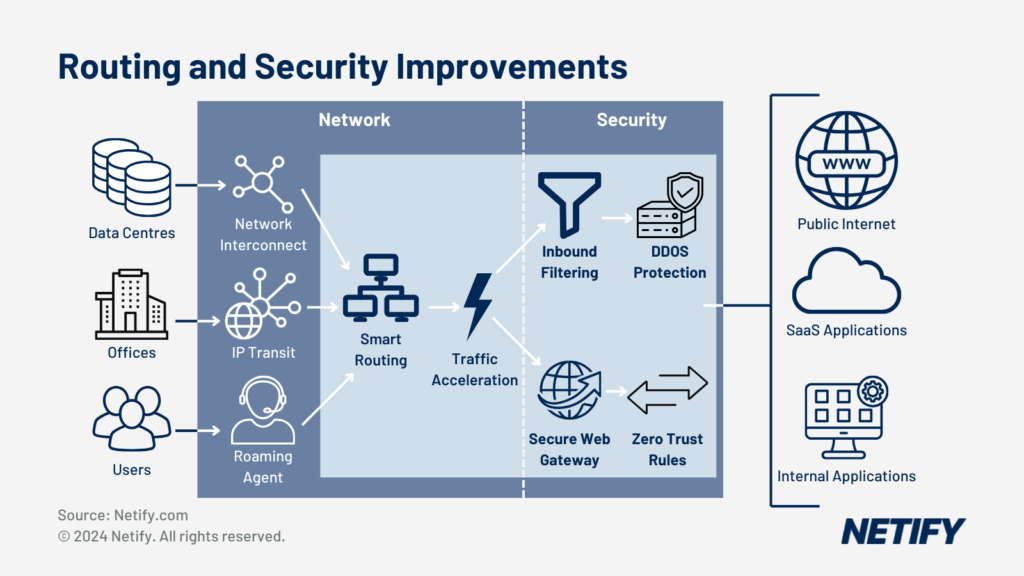
- SASE Routing and Security Improvements
By merging connectivity , security and data monitoring capabilities, Secure Access Service Edge (SASE) solutions send services directly to users, not the data center. By providing centralized data management for distributed systems, SASE simplifies and cuts the costs of SD-WAN environments that support:
- Retail apps and services.
- Cloud security functions related to network traffic and web security gateways, advanced firewalls and zero-trust account access.
But what is the SASE approach to cybersecurity? Here’s some background.
SASE Framework
SASE addresses the trifecta of modern networking problems: increasingly distributed networks, more network traffic (especially in the cloud) and a larger-than-ever attack target.
What is SASE?
SASE is a relatively new security and networking technology, which protects data access and information privacy throughout an organisation’s system. This approach protects an organisation’s IT infrastructure from edge to edge rather than infrastructure located within traditional perimeter boundaries. So, consider SASE as a cloud-based service, which:
- Merges SD-WANs and advanced security and monitoring capabilities.
- Reduces the number of system vendors and internet-connected devices.
- Can be scaled up and down and billed based on usage.
But vendors offer SASE services in a large, complex third-party environment.
SASE Ecosystem
To find, install and use SASE software and services, IT pros must search a crowded, highly fragmented market that includes many potential providers. For example, these vendors provide SASE connectivity services:
- SD-WAN
- Network carriers
- Content delivery network
- Network-as-a-service
- Bandwidth aggregators
- Networking equipment vendors
These third-party providers offer security capabilities directly to customer IT operations:
- Secure Web Gateway (SWG)
- Cloud-based access security (CASB)
- Zero-trust, protected network
- Software firewall-as-a-service
- Web API protection-as-a-service
- Domain name server (DNS)
- Remote Browser Isolation (RBI)
Also, SASE solutions provide robust benefits and value to adopters willing to try a new approach to retail security.
SASE Benefits
Implementing SASE architectures enable retail enterprises to:
- Reduce operations costs and simplify security systems administration: In SASE environments network security as a service comes from a single vendor. Consolidating technology stacks and number of vendors reduces IT labour and security investment costs.
- Increase agility and discover new digital business scenarios: SASE enables IT organisations to share applications, services, APIs and data with partners and contractors with less cybersecurity risk.
- Improve network performance: Networks use latency-optimised routing to maximise connectivity speeds.
- Increase ease of use and information transparency: SASE capabilities enable IT teams to operate with fewer agents per device and provide consistent application performance anywhere, with any device. IT pros can update threat data without buying new hardware or software. And they can adopt new capabilities with lower operations overhead.
- Acquire Zero Trust Network Access (ZTNA) capabilities: SASE solutions base access permissions on user, device, and application identity, not IP address or geographic location information. This new approach uses edge-to-edge encryption to protect data within and beyond the network perimeter.
SASE solutions provide an efficient, cost-effective way to implement a direct-to cloud architecture without compromising on data visibility and control and network security performance.
Retail and E-Commerce Regulations
There are many national- and state – level standards and regulations that govern retail operations in the U.S. and European Union. Compliance is more complex and frustrating than ever. But non-compliance can have serious negative effects, including penalties and fines that damage brand reputations and lead to lost customer loyalty and revenue.
Important Retail/E-Commerce Regulations
Here are three well-known standards, which describe SASE-related cybersecurity capabilities:
- General Data Protection Regulation: GDPR, a European Union rule, which regulates data protection and privacy for all organizations that do business in the European Union and the European Economic Area. SASE-related topics include the definition of personal data, data encryption and cybersecurity risk; email marketing efforts; and customers’ rights to access and view their personal data.
- California Consumer Privacy Act: The CCPA is a statute designed to improve the privacy rights and data security of consumers doing business with for-profit organisations operating in California. Consumers have the right to examine all the data a business collects about them. SASE-related data access topics include the definition of personal information, consumer right-to-know information and the types and frequency of data updates.
- Payment Card Industry Data Security Standard: PCI DSS is a national standard written to help organisations secure and manage information provided in branded payment card transactions. PCI standards are required by credit card providers but administered by members of the U.S. payment card industry. PCI-related topics include personal data protection priorities, applicable types of card data, and developing a risk management program for stored PCI data.
No single technology or approach can solve all retail cybersecurity challenges
Retailers should consider using new IT tools and established best practices to secure back-end, e-commerce servers. Examples include:
- Establishing and enforcing account access for all users
- Requiring Multi-Factor Authentication (MFA) on all administrative and highly privileged accounts.
- Updating server operating system and applications regularly.
- Encrypting all customer data at rest.
- Considering installation of Web Application Firewall (WAF) and a security solution on servers.
- Installing robust, multi-layered endpoint defences.
Enable Safer, More Efficient Security Operations
To compete more effectively in modern retail sector, retailers must create architectures that reduce the risk of cyberattacks. That means developing SASE-enabled defence tactics such as:
- Secure SD-WAN: Retailers must secure their cloud-based, IT security stack, which includes internal – and external – facing applications. SASE solutions include SD-WAN capabilities, which enable faster changes to system architecture and provide integrated security—without adding additional complexity of security add-ons and overlays.
- Zero-Trust Account Access: Often, IT leaders view the ZTA approach to security as too costly and time-consuming to implement. In SASE solutions, retail-centred ZTA requirements include microsegmentation to prevent risks associated with contactless payments and IoT. And automation reduces the time, effort, and cost of adopting this otherwise laborious process.
- Cloud Access Security Brokers: Cloud Access Security Brokers (CASBs) are on-premises or cloud-based software that monitor and enforce security policies and user behaviour. These vital capabilities support security operations and compliance. CASB capabilities help govern your organisation’s cloud use with detailed visibility and control functions, based on specific user identity, service, activity, applications and data.
In other words, consider adopting SASE solutions to secure retail operations and comply with new regulations whenever they change.