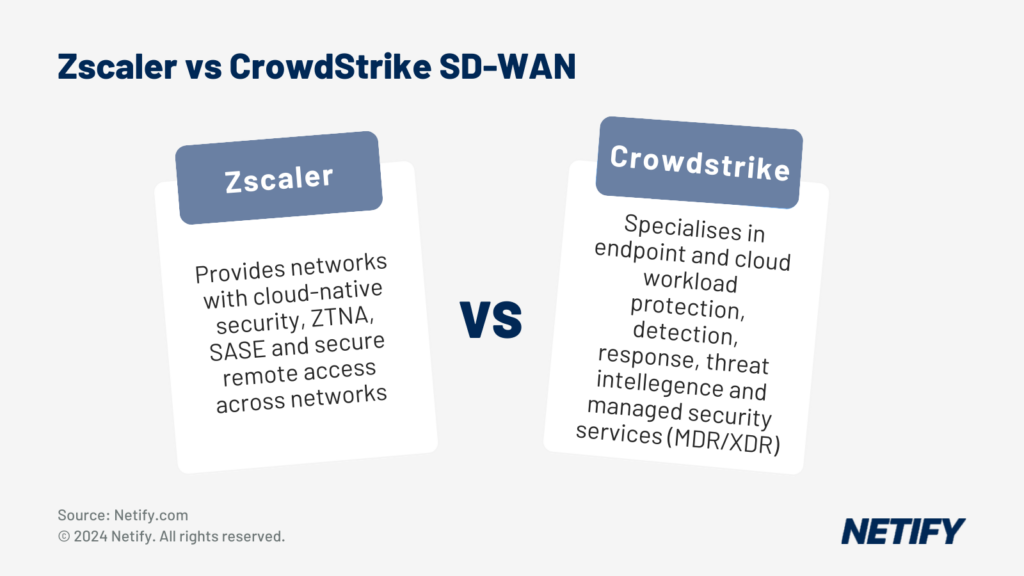
| Zscaler excels in cloud-native zero-trust security and SD-WAN solutions, while CrowdStrike leads in endpoint protection and threat detection, with both offering complementary benefits when integrated. |
What is the comparison between Zscaler vs CrowdStrike?
If you’re looking to accelerate your zero-trust network access strategy or deploy SASE, Zscaler is a solid choice. If you’re looking for industry-leading endpoint protection, consider CrowdStrike. Or, get both and leverage the unique security benefits from each solution through their deep integrations.
Zscaler vs CrowdStrike – Summary
Zscaler is a cloud-native network infrastructure solution and the Zscaler platform is designed to provide secure end-to-end zero trust network access regardless of where an organisation’s services or users are located. CrowdStrike is an endpoint security solution that began with EDR but has since evolved detection and response capabilities to cloud workloads, identity and data – in addition to endpoints. Zscaler and CrowdStrike have some cloud security capabilities in common, but otherwise, they exist to solve different problems. Integrating CrowdStrike with Zscaler is complementary, as this allows Zscaler to control access while CrowdStrike detects and responds to threats across an organisation’s IT estate.
Zscaler and CrowdStrike are leaders in their respective focus areas. They both have a respectable portfolio of big-name marquee customers, they both are well-covered for security and compliance, and they both offer a significant number of integrations with complementary technologies to enable them to be successful in most markets.
Zscaler vs CrowdStrike – SD-WAN comparison
What is the Zscaler SD WAN solution?
Zscaler incorporates several core SD-WAN capabilities, including the ability to uniformly enforce security controls while leveraging various transport services. That said, Zscaler’s platform would typically lay on top of underlying infrastructure which may or may not include SD-WAN solutions deployed by traditional internet service providers.
What is the CrowdStrike SD WAN solution?
CrowdStrike is a security solution and not a networking solution. Core capabilities don’t include providing or controlling network access, so its features aren’t relevant to SD-WAN.
Zscaler vs CrowdStrike – Cloud comparison
Cloud Computing with SASE integrations - Cloud Computing with SASE integrations
What is the Zscaler Cloud solution?
Zscaler’s cloud-native platform is comprised of various services including their Zero Trust Exchange, Zscaler Private Access, and Zscaler Internet Access services.
These services allow them to connect to a customer’s private cloud or on-premise infrastructure, as well as to connect to applications and services in public clouds or elsewhere on the internet.
Additionally, their solutions offer deep integration with leading public clouds including Microsoft Azure, Amazon Web Services and Google Cloud Platform.
What is the CrowdStrike Cloud solution?
CrowdStrike’s Falcon platform offers protection for workloads and resources hosted in the three major public clouds: Microsoft Azure, Amazon Web Services and Google Cloud Platform.
Zscaler vs CrowdStrike – Gartner SASE components (XDR, MDR, SWG, CASB, IDR, DLP, RBI)
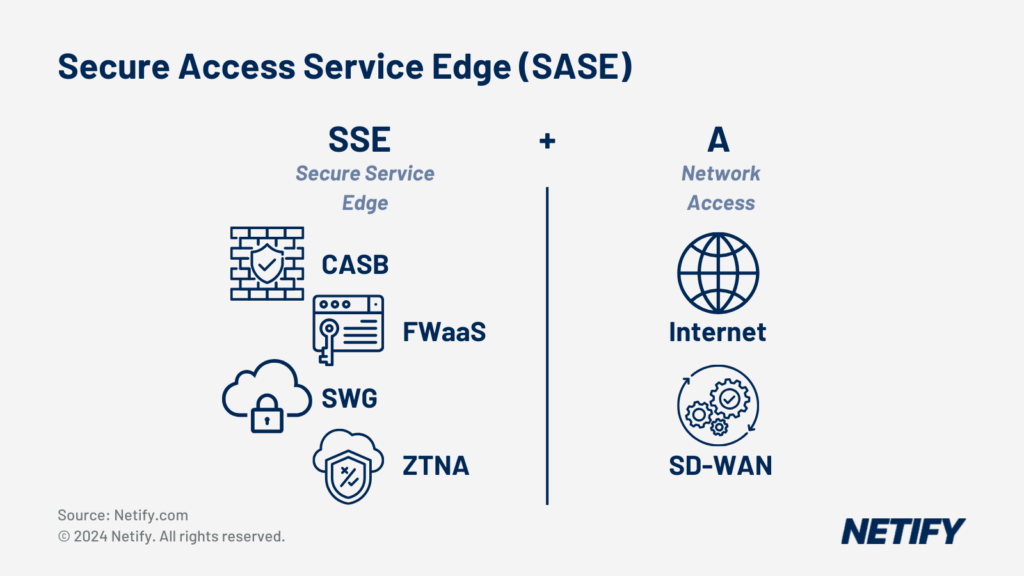
Secure Access Service Edge (SASE) is SSE + SD-WAN (Access) - Secure Access Service Edge (SASE) is SSE + SD-WAN (Access).
What is the Zscaler SASE Cybersecurity solution?
SASE (Secure Access Service Edge) is a concept for secure connectivity which is comprised of several underlying networking and security technologies. Zscaler’s platform consists of a portfolio of product and service components that can be combined or integrated with third-party point-solutions (for example, Zscaler offers an integration with CrowdStrike to leverage its XDR capabilities) to deploy SASE.
What is the CrowdStrike SASE Cybersecurity solution?
CrowdStrike’s Falcon platform offers XDR or MDR services. While CrowdStrike can integrate with third parties to support other SASE components, CrowdStrike doesn’t currently compete with vendors who offer comprehensive SASE solutions.
Zscaler vs CrowdStrike – Remote Access comparison
What is the Zscaler Remote Access solution?
Support for secure remote access is one of the primary problems that Zscaler solves. An organisation can securely connect their services and applications (whether on the internet, public cloud, private cloud, or on-premise) to Zscaler’s platform edge which spans across over 150 data centres.
Zscaler’s platform will act as a proxy and provide zero trust network access to those applications and services from any network anywhere in the world, by enforcing security policy as close to the user as possible.
What is the CrowdStrike Remote Access solution?
While CrowdStrike isn’t a remote access solution, CrowdStrike can integrate with remote access solutions to enhance security by detecting anomalies in login patterns or user behaviour, or by triggering additional identity verification (e.g. multifactor authentication) when certain risk factors exist.
Zscaler vs CrowdStrike – SIEM (Security Information and Event Management) comparison
What is the Zscaler SIEM solution?
Zscaler isn’t a SIEM, but their platform is architected such that it is likely to be positioned as a gatekeeper for most or all of an organisation’s connections to applications and services. Therefore, events generated within the Zscaler platform would make an extremely valuable data source for an integrated SIEM solution. Zscaler has a long list of SIEM integrations including industry leaders such as Splunk, Sumologic, LogRhythm and many more.
What is the CrowdStrike SIEM solution?
CrowdStrike Falcon isn’t a SIEM, but as an XDR solution it often serves as a primary data source for SIEM solutions. CrowdStrike offers integrations with several SIEM providers including Splunk, Exabeam, IBM Security and others. Additionally, CrowdStrike recently acquired Humio, a log management solution with SIEM-like security analytics.
Zscaler vs CrowdStrike – Endpoint Protection comparison
What is the Zscaler Endpoint Protection solution?
Zscaler isn’t a traditional endpoint protection solution, but because they are likely to be positioned in front of most or all endpoint connectivity, they can offer valuable context information to integrated endpoint protection solutions. Zscaler has integrations for many leading endpoint protection solutions including CrowdStrike, Microsoft Defender, VMware Carbon Black, SentinelOne and others.
What is the CrowdStrike Endpoint Protection solution?
Endpoint protection is the primary problem that CrowdStrike solves. CrowdStrike’s Falcon platform delivers advanced endpoint protection capabilities including next-generation antivirus, integrated threat intelligence, USB and firewall control, detection and response, and threat hunting.
Additionally, CrowdStrike offers managed endpoint protection services which include 24x7x365 monitoring (with a claimed average response time of less than 10 minutes), threat hunting, forensics and incident response.
Zscaler vs CrowdStrike – File Analysis comparison
What is the Zscaler File Analysis solution?
As a distributed proxy, Zscaler is well positioned to inspect all encrypted traffic without having to create potential bottlenecks by routing to a central location. This means that even without endpoint visibility, they are able to decrypt traffic for file analysis.
What is the CrowdStrike File Analysis solution?
CrowdStrike Falcon’s Next-Generation Antivirus (NGAV) capability utilises machine learning and artificial intelligence as well as multiple threat intelligence sources to analyse files and determine whether or not they’re malicious. As an endpoint protection solution, CrowdStrike Falcon can also take action on detections by quarantining files or preventing execution.
Zscaler vs CrowdStrike – Cloud Workload Protection comparison
What is the Zscaler Cloud Workload Protection solution?
Cloud workload protection is another one of the primary problems that Zscaler solves. Zscaler Cloud Protection delivers capabilities for Cloud Security Posture Monitoring (CSPM), Cloud Access Security Broker (CASB), Intrusion Prevention System (IPS), and Data Loss Prevention (DLP). Additionally, Zscaler’s platform offers cloud firewall functionality and sandboxing to enable zero-trust segmentation between workloads.
What is the CrowdStrike Cloud Workload Protection solution?
While Zscaler primarily protects cloud workloads by controlling access, CrowdStrike primarily protects cloud workloads by detecting and responding to threat indicators. CrowdStrike can provide visibility and runtime protection into workloads and containers across multiple clouds and CrowdStrike supports DevOps through integration with CI/CD pipelines. CrowdStrike also offers Cloud Security Posture Management (CSPM) capabilities to detect misconfigurations and ensure compliance with cloud security policies.
Zscaler vs CrowdStrike – IT Vendor Risk Management Tools comparison
What is the Zscaler IT Vendor Risk Management Toolset?
While Zscaler isn’t a vendor risk management tool, it does offer some capabilities which support vendor risk management. For example, where Zscaler is used to provide vendors with access to an organisation’s infrastructure, Zscaler may be able to provide information in support of a vendor access audit.
What is the CrowdStrike IT Vendor Risk Management Toolset?
Like Zscaler, CrowdStrike isn’t a vendor risk management tool, but in some deployments, it may be positioned to provide information to support audits on vendor access or behaviour when interacting with your resources.
Zscaler vs CrowdStrike – Insider Risk Management comparison
What is the Zscaler Insider Risk Management solution?
Zscaler’s architecture is designed to prevent insider risk threats like lateral movement, with Zero Trust Network Access (ZTNA) to further reduce attack surfaces for insider threats. And, Zscaler’s ability to inspect all encrypted traffic allows Zscaler or integrated threat detection tools to detect and respond to indicators of potential insider risk activity as they appear.
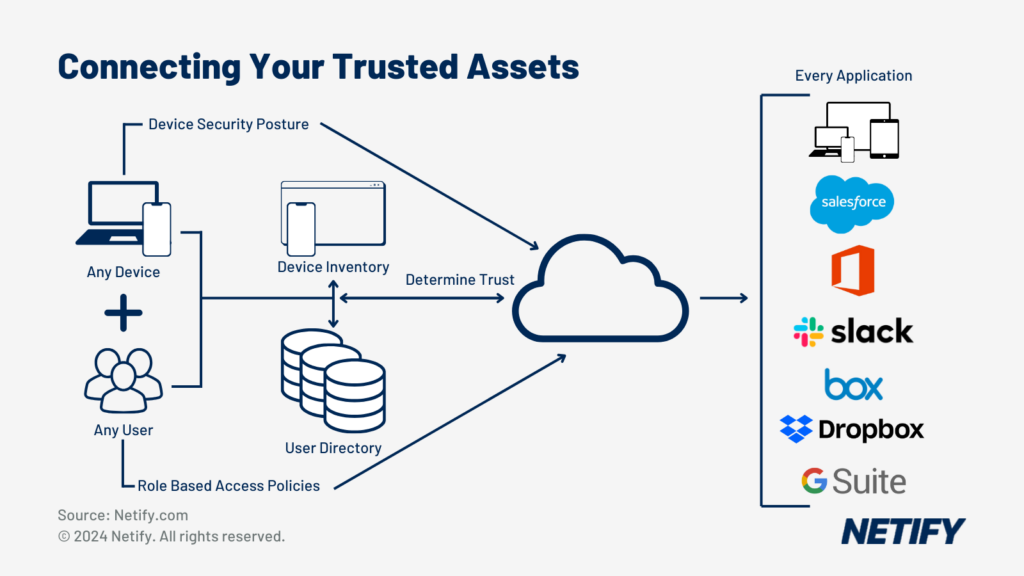
Zero Trust Network Access (ZTNA) within SASE - Zero Trust Network Access (ZTNA) within SASE
What is the CrowdStrike Insider Risk Management solution?
CrowdStrike Falcon enables organisations to manage insider risk threats by using machine learning and artificial intelligence to detect suspicious behaviour or indicators of compromise, providing the capability for security teams to respond quickly, or even immediately with pre-defined rules for protective actions.
Zscaler vs CrowdStrike – Identity Governance and Access Management
What is the Zscaler Identity Governance and Access Management solution?
The Zscaler platform’s Zero Trust Network Access (ZTNA) capabilities enable organisations to govern identity and access management consistently and at scale. Additionally, Zscaler’s Cloud Protection services can enhance security for DevOps by extending zero trust identity and access management to cloud resources and APIs. Zscaler also provides integrations for leading identity providers and access management solutions including Microsoft Azure Active Directory, Ping Identity, Okta, CyberArk, OneLogin and more.
What is the CrowdStrike Identity Governance and Access Management solution?
CrowdStrike is an identity or access management solution, but integration with leading solutions enhances identity and access management by detecting identity threats. CrowdStrike Falcon can assign risk scores to a given credential, cloud resource, or endpoint by correlating events across endpoints, directories and clouds. CrowdStrike offers integrations with Microsoft Active Directory and Azure Active Directory, Okta, CyberArk, ForgeRock and more.
Zscaler vs CrowdStrike – IoT Security comparison
What is the Zscaler IoT Security solution?
Private Access can enable zero trust access for IoT or OT devices, whether internet-based or on-premise.
What is the CrowdStrike IoT solution?
While CrowdStrike Falcon’s core competency is endpoint protection, CrowdStrike offers several integrations with IoT, ICS and OT security solutions to detect potential threats to IoT devices on endpoints where CrowdStrike has availability.
CrowdStrike also offers integrations with network infrastructure to automate responses to IoT security threat detection (e.g. disabling switch ports or blocking wireless network access). IoT/ICS/OT security integrations include Dragos, Claroty, Medigate, Forescout and others. Network infrastructure integrations include Zscaler, ExtraHop, Airlock, Aruba, Gigamon and many more.
Zscaler vs CrowdStrike – Vulnerability Assessment comparison
What is the Zscaler Vulnerability solution?
Zscaler is not a vulnerability assessment solution, but Zscaler Cloud Protection’s Cloud Security Posture Management (CSPM) capability enables organisations to identify vulnerabilities in cloud configurations and workloads.
What is the CrowdStrike Vulnerability solution?
Although CrowdStrike Falcon is not a traditional vulnerability assessment solution, it offers features comparable to vulnerability assessment solutions that offer agent-based scans like Tenable.io or Rapid7’s InsightIDR.
The Falcon agent can continuously monitor endpoints for vulnerabilities due to misconfiguration or missing patches and dashboards help with assigning risk-based prioritisation to remediation efforts. Additionally, like Zscaler, CrowdStrike also offers CSPM capabilities to identify vulnerabilities in cloud configurations and workloads.
Zscaler vs CrowdStrike – Instant Communications comparison
What is the Zscaler Instant Communications solution?
When an organisation deploys Zscaler solutions, even administrator users won’t spend a tremendous amount of time working or collaborating within Zscaler applications, so instant communications aren’t as important as they would be in network or security operations tools.
What is the CrowdStrike Instant Communications solution?
The CrowdStrike Falcon platform is designed for regular use by security analysts and incident responders and it therefore includes the CrowdStrike Message Centre. This allows security teams to collaborate securely within their organisation, or with CrowdStrike’s analysts, threat hunters, or threat intelligence team.
Zscaler vs CrowdStrike – Security and Compliance comparison
What is the Zscaler Security and Compliance solution?
Zscaler’s platform maintains global security framework compliance certifications including ISO 27001/27701/27018/27017, SOC 2/3 and CSA-Star. Zscaler has published attestations for HIPAA, PCI-DSS, APRA and MSA. Zscaler also maintains government certifications for FedRAMP, DoD IL, FIPS 140-2, IRAP, ITAR, CJIS, VPAT/508, NCSC Cyber Essentials, CISA TIC3.0, and NIST 800-63C. Finally, Zscaler’s platform is designed for compliance with privacy frameworks including GDPR, PIPEDA, APPI, CCPA, AU/NZ Data Privacy and Privacy Shield.
What is the CrowdStrike Security and Compliance solution?
CrowdStrike maintains global security framework compliance certifications for PCI-DSS, CSA-Star, HIPAA, CREST and SOC 2. CrowdStrike also maintains government certifications for FedRAMP, NSA-CIRA and FFIEC. Finally, CrowdStrike complies with privacy frameworks including Privacy Shield and GDPR.