| SD-WAN security integrates advanced AI, zero-trust models and SASE frameworks to protect data, simplify management. These features enable secure access across distributed networks and cloud applications. |
As an IT decision maker, you are undoubtedly totally aware of how SD-WAN facilitates efficient, centralised management, greater visibility into network activities, improved data traffic flow and application performance. These features are the enablers for distributed networks across branch-office and remote users, which in turn means the investigation into understanding SD-WAN security is your number one task when assessing solutions.
- SD-WAN Security Guide
SD-WAN architectures have evolved to integrate advanced security measures to safeguard against cybersecurity threats. Gartner have even defined a security framework which describes the key components required to implement end-to-end security from endpoint protection that shields remote worker devices to secure web gateways that scrutinise data to detect malware.
2024 has evolved SD-WAN security to include Artificial Intelligence (AI) and machine learning, which enhances detection and prevention of security threats. AI-driven security in SD-WAN systems enable the real-time identification and counteraction of potential intrusions, automating policy enforcement with high precision.
Despite these advancements, organisations are navigating through security challenges. Direct internet access and the complexities of SD-WAN deployments introduce huge risks, underscoring the need to deploy comprehensive security features. Although encryption plays a role in protecting data as it traverses the WAN, comprehensive SASE and SSE Cybersecurity is required to complete your networking solution.
While SD-WAN security features are important, the differentiators are based around centralised management systems, ease of configuration and deployment offer the insights required to supervise ecosystems. IT decision makers should understand that features are only the beginning – understanding how the features are configured, deployed and supported is just as important.
AI’s Role in Enhancing SD-WAN Security
In 2024, artificial intelligence (AI) is transforming SD-WAN security, creating a generation of solutions that are much more capable of protecting network infrastructures vs traditional solutions. Juniper Networks has pioneered the development of tunnel-free, application-aware, zero-trust security solutions. By leveraging the power of AI, these solutions offer improved visibility and control to enhance the security and performance of wide-area networks.
Machine learning (ML) – a subset of AI – has become an important aspect of the network, offering benefits from automating routine tasks to enhancing network performance.
The integration of AI and ML ensures that network devices can independently monitor data traffic, identify patterns, and accurately respond to security events. As traffic within organisations grows exponentially, this level of automation is required to mitigate against threats in real-time.
AI-powered Secure Access Service Edge (SASE) represents an approach that brings together network and security functions. This integration of AI across Secure Web Gateways (SWG), SD-WAN, Cloud Access Security Brokers (CASB), and Zero Trust Network Access (ZTNA) delivers a unified and adaptive security model.
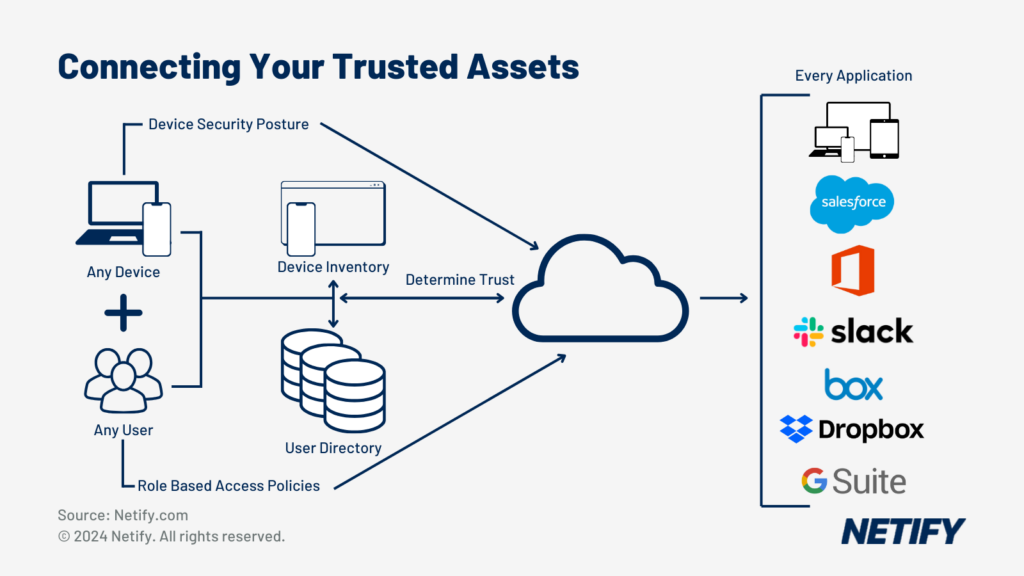
Zero Trust Network Access (ZTNA) within SASE
AI-driven SD-WAN solutions enhance zero-trust security, next-generation firewalls, as well as intrusion detection and prevention capabilities. These AI-enabled systems contribute not only to consistent visibility across the network but also enable smart decision-making and proactive threat detection.
Despite these advancements, challenges exist across the complexity of AI deployments – there’s potential security vulnerabilities inherent in newly adopted technologies. Nevertheless, the integration of AI and ML into SD-WAN is the only way to fully secure networks on a real-time basis.
Insights from industry leaders confirm the growing adoption of AI and ML within network solutions. We are seeing vendor solutions which are paying significant attention to AI interconnected services and the role of AIOps in network management.
It is clear that AI-driven SD-WAN is set to play a huge role in the future of network performance and security. AI developments are shaping an era where advanced AI capabilities are central to the design and operation of secure networking solutions.
SD-WAN Vendors – Approach to Security
2024 vendors are enhancing their SD-WAN solutions to address current challenges. Companies such as Cisco, VMware, and Versa Networks offer security strategies to meet the needs of enterprise-scale deployments. Cisco’s approach to SD-WAN security includes an architecture that integrates security features directly into their platform, including advanced Cisco Catalyst SD-WAN design elements, which include DNS-layer security to provide a line of defence against cyber threats directly within their network management framework.
VMware differentiates through the implementation of enterprise firewalls via their SD-WAN Gateways. VMware’s architectural choice ensures that data is scrutinised and secured as packets flow through various network nodes – optimising traffic paths while enforcing security measures.
Versa Networks offers a suite of embedded security features via their multi-layered security platform which integrates anti-virus/malware defence and DNS security measures directly into their SD-WAN solutions to provide visibility and protection for both branch and cloud traffic.
The adoption of Secure Access Service Edge (SASE) models becomes increasingly relevant because vendors are blending network and security functions into a unified cloud-delivered security service.
Comparative Analysis of SD-WAN Security
Enterprises are engaging in a digital transformation by adopting multicloud environments and software-as-a-service (SaaS) applications. Your company analysis of SD-WAN security mechanisms involves examining various implementations and their impact on factors such as latency, total cost of ownership (TCO), and security effectiveness.
Firewall devices offer protection and are typically selected by enterprises with existing comprehensive security measures. Basic firewall appliances are aimed at complementing rather than replacing in-depth security systems. On the other hand, devices with next generation firewalls deliver more refined protections and are often positioned as a mid-range option in terms of security capability comparison.
Companies opting for firewall appliances with embedded SD-WAN functions gain benefits from the depth of security features that firewall vendors have developed over time. The convergence of firewall and SD-WAN means that the majority of firewall vendors now offer comprehensive SD-WAN features to meet the needs of most requirements.
We are witnessing the growth and adoption of Secure SD-WAN as a Service, which merges SD-WAN and security into cloud services. The ‘as a service’ approach often entails advanced threat protection and intrusion prevention methods. Enterprises prioritising scalability and intelligence in their security strategies may also integrate with cloud-based security providers (AWS, Azure, Google Cloud etc).
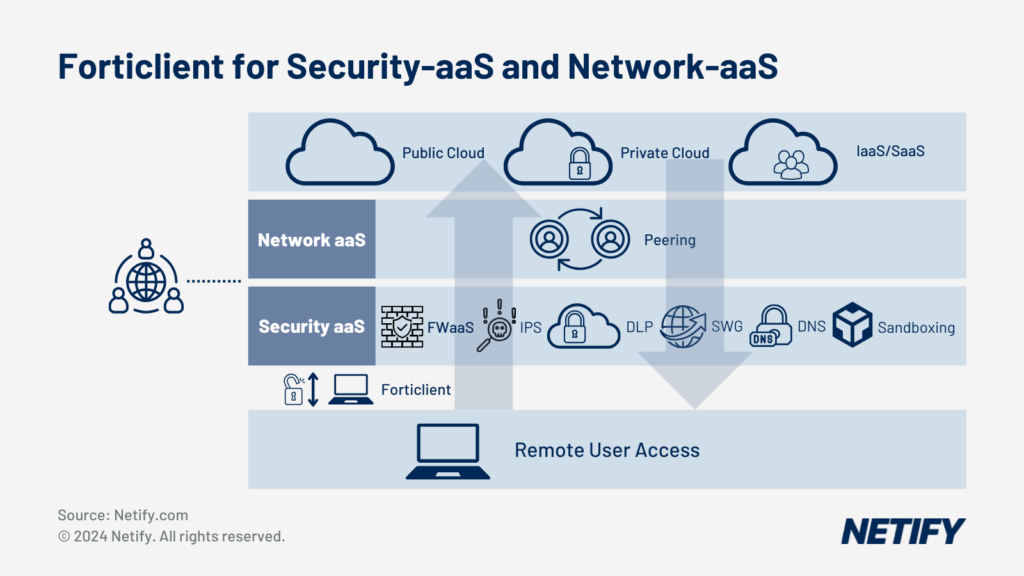
Forticlient For Security-as-a-Service and Network-as-a-Service
The methodology in securing SD-WAN spans encryption of data in transit, using IPsec and SSL/TLS protocols to ensure data integrity. Alongside encryption, network segmentation (offered by specific vendors) aids in minimising attack vectors and maintaining compliance with continuous monitoring and real-time threat detection employed to safeguard direct Internet network traffic.
IT decision-makers must balance the trade-offs between security effectiveness, ease of management, and TCO. Each approach presents its unique attributes; comparative analysis of these mechanisms is fundamental to optimising the security of SD-WAN architectures.
As businesses send more traffic to cloud platforms (IaaS), the model of SD-WAN as a Service gains traction in partnership with cloud as a service solutions.
The requirement for secure remote access has never been more apparent as home workers increase in numbers. SD-WAN solutions are under scrutiny to ensure they provide cyber threat protection alongside seamless access for users. There’s a balance between providing remote users with access to resources while maintaining a security posture to protect the organisation. The concept of Zero-Touch Deployment is evolving in terms of features and adoption.
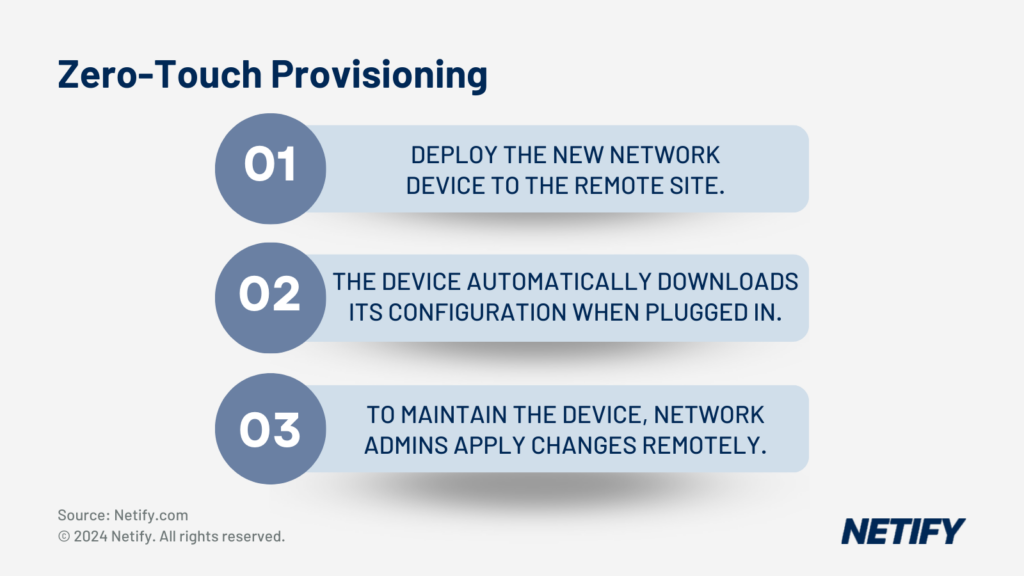
The steps of Zero Touch Provisioning (ZTP)
ZTNA is revolutionising the deployment process through automation, which in turn reduces the need for manual configurations. The projected rise of Secure Access Service Edge (SASE) further indicates a convergence of networking and security services, aiming to simplify the management of distributed endpoints and data centres.
Incorporation of AI into SD-WAN brings forward a new era of security innovation by automating optimisation of traffic paths to improve both performance and security monitoring. The integration of SD-WAN and Wireless WAN (WWAN) signifies a leap towards more innovative and flexible deployment options.
Gartner are projecting substantial growth in the SD-WAN market, with a particular emphasis on security. Anticipated advances in security features include comprehensive firewalls and VPN solutions. Collectively, these trends suggest a future where SD-WAN security is characterised by intelligent, cloud-driven solutions that not only protect against sophisticated cyber threats but also provide streamlined network management and improved user experience.
What Are the Elements of SD-WAN Security?
The architecture of an SD-WAN solution lies at its foundation, enabling centralised management and support for applications across multicloud and software-as-a-service (SaaS)platforms.
Within this framework, encryption—often through IPsec—plays a critical role in protecting data as it travels across the network, whether that be through virtual or physical paths. Automation aids in the swift roll-out of updates to enhance the security posture, while scalability ensures that as the network grows, the security measures grow with it, without compromising on QoS or capacity.
The enterprise firewall and next-generation firewalls (NGFW) are needed to extend protection against intrusions and managing the security solution effectively. Secure Access Service Edge (SASE) is becoming integral to SD-WAN security, converging network and security functions to streamline service delivery. Secure web gateways offer another layer, deploying URL filtering and malware protection to thwart potential threats. A noteworthy mention is segmentation, or micro segmentation, which is available from specific vendors such as Cisco and Versa.
Cloud Computing with SASE integrations
Cloud applications have placed demands on service delivery, with SD-WAN security providing the architecture to accommodate these applications securely. This allows businesses to maintain their agility and ensure users have the necessary access without compromising on security. The overall security solution of SD-WAN encompasses a layered approach, where integrated security and policy enforcement work in tandem.


