Use the Netify comparison tool to find out which SD WAN & Cybersecurity solutions match your Financial Services business needs.
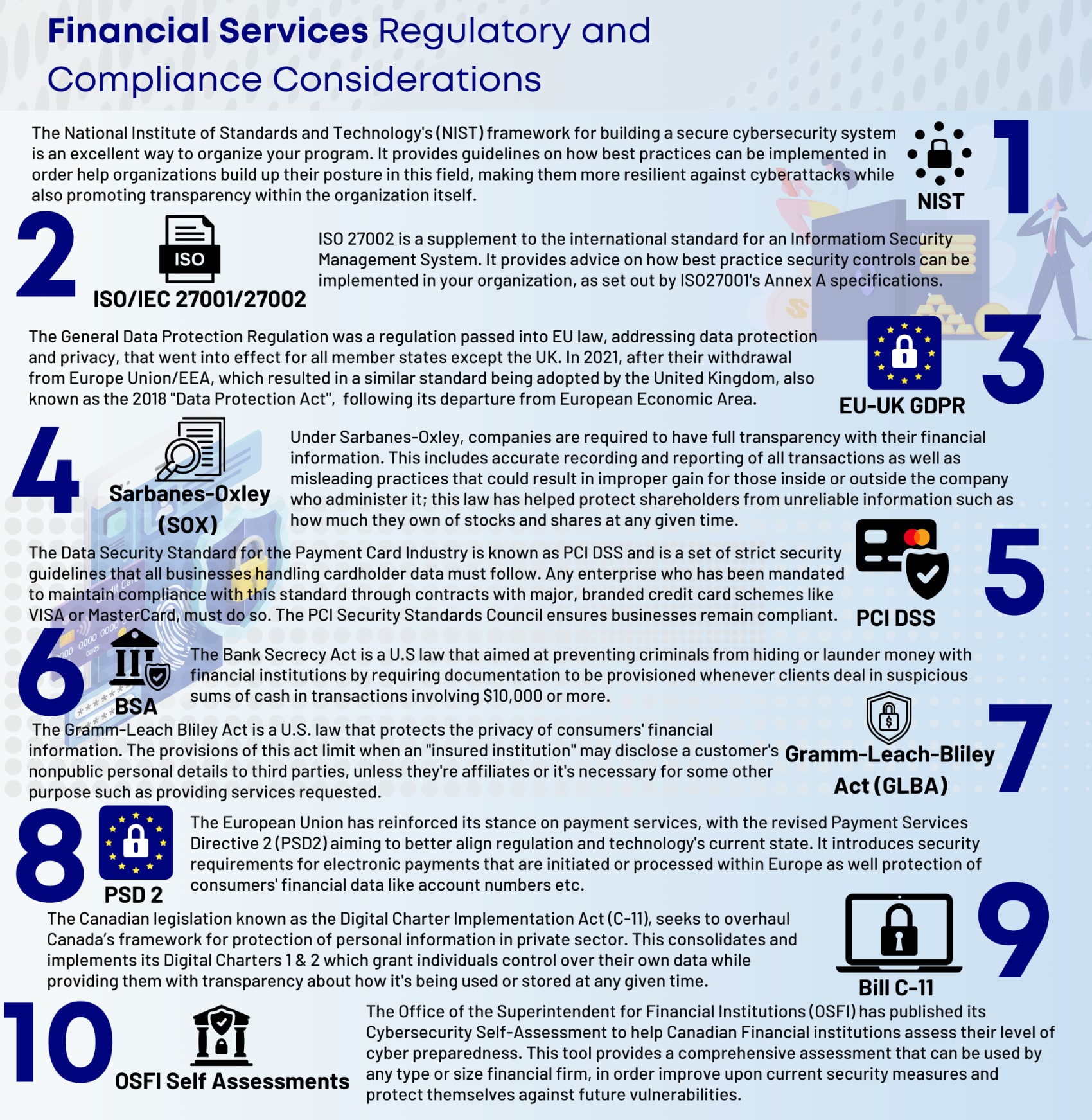
Comparing Cybersecurity and SD WAN vendors for the financial services sector requires aligning regulations and compliance across NIST, ISO/IEC 27001/27002, EU-GDPR, UK-GDPR, SOX, PCI DSS, BSA, GLBA, FINRA, PSD 2, Bill C-11 and OSFI Self Assessments.
The Netify SASE Cybersecurity and SD WAN marketplace offers expertise across the financial services sector. Our listings offer filters to help IT decision makers shortlist solutions which fit with compliance and regulations and offer case studies to demonstrate successes.
We're a free to use resource with research data, assessments and vendor briefings.
Below: The Netify Mind Map guide to Cybersecurity across financial services.
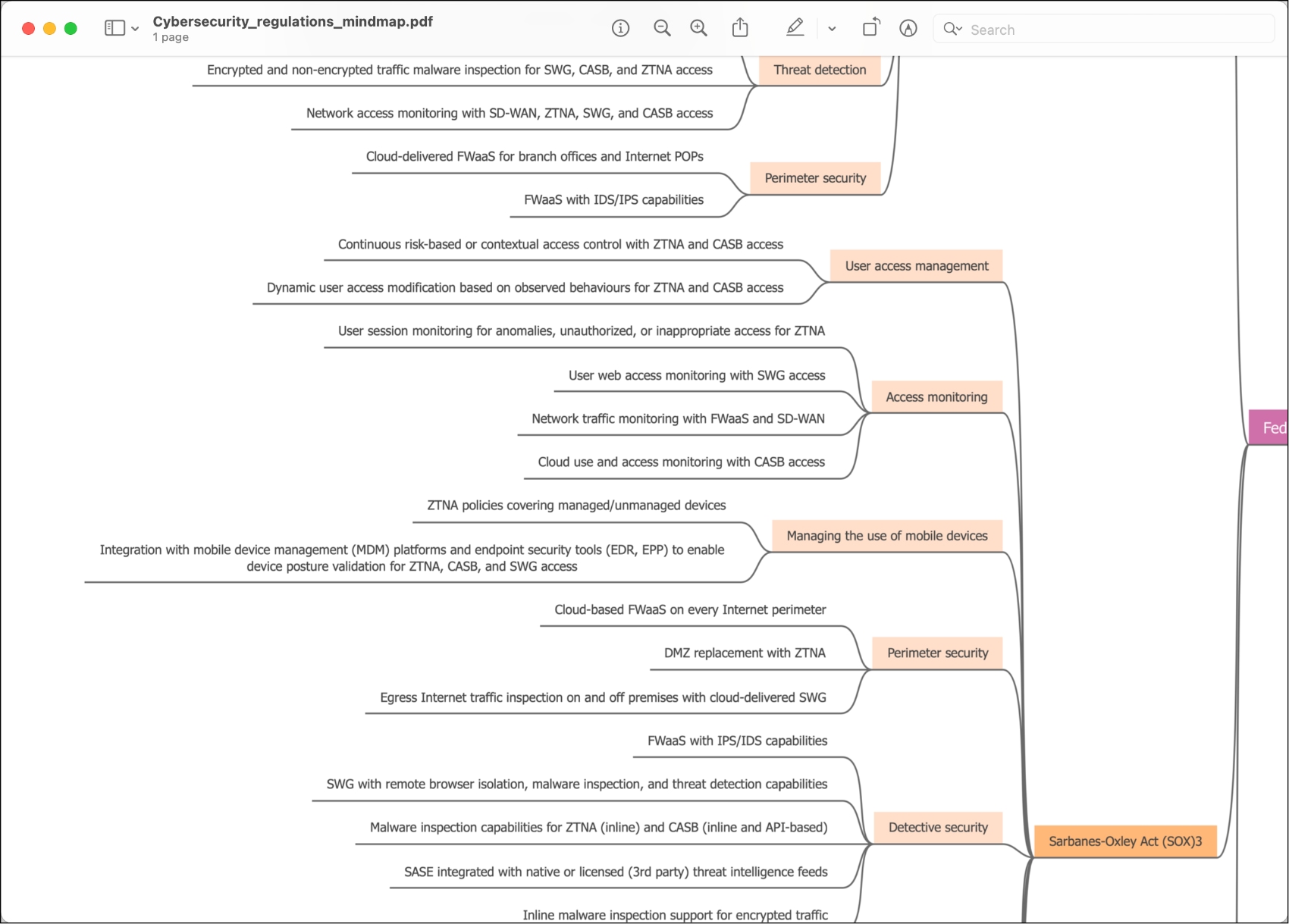
Organizations in the Financial Services (FS) sector are some of the most high-value targets for bad actors in today’s threat landscape and their defenders have to deal with constant attacks ranging from insider threats to social engineering to complex targeted operations carried out by Advanced Persistent Threats (APTs). It is no surprise that in the past few years, cyber risk continues to increase for these organizations as new technologies and ways of doing business and sharing information are adopted. There is also an increasing amount of responsibility bestowed upon these organizations by regulatory bodies to implement more security controls and get ahead of the latest cyber threats rather than just simply being reactive.
Legal obligations for data protection are evolving rapidly as new threat intelligence comes to the forefront, so it is more important than ever that we find some semblance of cohesion and understanding as to what financial services organizations need to know and practice to maintain a responsible level of resilience against cyber threats. This starts with understanding the both new and existing regulations and security frameworks, the reasons for which they exist and the best way to achieve regulatory compliance while maintaining an effective security posture against today’s most prevalent threats. This article attempts to bring clarity to the requirements and how to stay in compliance with them effectively and efficiently.
There are many regulatory bodies we can consider stakeholders in the financial services industry and in addition to regulations we also have many relevant security standards and frameworks which may be broadly applicable, or specifically applicable to organizational functions.
Additionally, there are other emerging privacy regulations which aren’t specific to the financial services industry, but they are still significant because they must be followed by any kind of business handling personal data under their jurisdiction – like the European Union’s General Data Protection Regulation (GDPR), the United Kingdom’s version (UK-GDPR), or California’s California Consumer Privacy Act (CCPA).
There is another data privacy regulation which should be mentioned even though it was not enacted in its last vote. Canada’s Bill C-11 was meant to give greater control of personal data to consumers and users of services and technology. Although this hasn’t been enacted and therefore is not mandatory, it shows that Canada is, generally, aiming to ensure all data collection is transparent to whom the data is being collected on and to allow them to review and remove this data from collections anywhere it is stored – with many similarities to GDPR and CCPA.
The SOX Framework spawned from The Sarbanes-Oxley (SOX) act of 2002 and is required to be followed by all public companies in the financial sector in the United States. This framework was set up to protect investors from fraud by providing a way to validate the accuracy of financial transactions but has grown to include cybersecurity requirements to help curb common attacks aimed at the financial sector.
Payment Card Industry (PCI) Data Security Standards (DSS) is an international standard with which any business that processes credit card payments must comply. PCI DSS has various levels of certification which carry different security requirements based on an organization’s role in processing card payments. For example, smaller merchants who accept card payments may be able to comply with simple self-assessment questionnaires or undergoing a very basic automated vulnerability scan, while organizations who process or store large amounts of card transaction data may need to be regularly audited by a Qualified Security Assessor (QSA).
Additionally, financial organizations in the European Union must comply with PSD 2 (Payment Services Directive) which includes language on safeguarding digital payments, data integrity and authentication methodology. The Bank Secrecy Act (BSA), which is another United States regulation, requires all financial institutions that accept funds from customers to work with governmental bodies in order to battle crime in the financial sector. BSA has requirements around cybersecurity and managing data breaches in its scope which requires organizations to consider and prepare for potential cyber incidents.
The Gramm-Leach-Billey Act (GLBA) is a privacy regulation specific for financial services and it’s required to be followed by all United States organizations selling financial services or products. GLBA aims to protect the consumer by giving them the right to knowledge of how their data is shared and putting the responsibility of privacy and safe data handling on the processors and organizations handling private data, including financial institutions specifically.
The Financial Industry Regulatory Authority (FINRA) in the United States requires that all brokers and brokerage firms giving financial advice or participating in the trade of securities are licenced and registered. Any broker or brokerage firm licenced under FINRA is subject to compliance with FINRA rules, regulations and regular compliance audits.
There are many regulations, authorities and standards that need to be considered when approaching solutions to cybersecurity and data protection requirements. The good news is that there is a relatively new cybersecurity framework that tries to take on all of the overlap between many of the above-mentioned requirements while adding a few more for good measure and tying it all together in one comprehensive framework - The National Institute of Standards and Technology’s (NIST) Cybersecurity Framework (CSF). While this framework is generally only mandatory for United States federal government agencies or organizations that contract with them, there is a Financial Services Specific Profile available to help financial services organizations adapt the NIST CSF to the complexities of the financial services sector.
This is a very good way for any financial services organization to ensure compliance with many regulatory requirements while using common language to demonstrate their security posture and controls they implement to protect their customers, partners and themselves. The FS profile maps the ISO 27001 standard and NIST CSF to the most prevalent FS regulations. One of the most significant benefits of the framework is the fact that the NIST CSF is free-of-charge to use and agile enough to work for organizations across industries, with relatively simple mappings to most other security standards, frameworks and major regulatory requirements.
The collaboration between NIST creators and the financial services sector stakeholders resulted in customizations specific for FS organizations which allows them to benefit from the longevity of an ever-evolving tool like the NIST CSF. Adoption of the FS profile also eases some of the complexity due to multiple regulations in the FS industry as well as reduces the administrative cost for managing them alongside multiple security frameworks.
(measured in billions USD)
The financial services sector is one of the most heavily regulated sectors in the world. When deciding on what type of functionality you need to have in place, you should map your regulatory requirements for cybersecurity to the functionality of the cybersecurity solution and SD-WAN.
Reach out to your compliance team to get input on the type of areas within your organization that have the highest risk.
A TPRM allows you to cross-reference compliance requirements with security assessments. Going through a TPRM process provides actionable insights into how to meet regulatory requirements with the right level of security. The work you carry out under question 1 above will help during this process.
Financial services often use a mix of private and public cloud infrastructures. These multi-cloud environments mean that the underlying infrastructure is complex. SD-WAN helps ameliorate this complexity; however, it is vital to have visibility of critical apps and devices. Does your organization have the in-house capability and solutions to continuously monitor this complex environment? If not, can you reach out to specialist third-party managed services for help?
Certain regulations will stipulate certain roles in an FI are under greater monitoring and protection than others. Julie Hoggett of the FCA said at a City Financial Global event, that financial firms must provide “effective surveillance at all times”. “It is essential in changing times that firms identify the risks associated with the new environment in which we are all operating.” Maintain a register of critical roles and the apps and data they require access to. This will be important in configuring zero trust and privileged access, key enablers in meeting regulations.
The 2021 Enterprise Strategy Group (ESG) survey found that 79% of organizations are experiencing a widening visibility gap across their cloud infrastructures. To determine how to optimise the configuration of your SD-WAN you need full visibility across your branch infrastructure, home office environment and remote devices. Other important considerations are the elastic nature of financial operations: ask, how often do you add/remove branches, and how fluid is your general workforce in terms of Work from Anywhere?
Deep integration of cybersecurity solutions into an SD-WAN is important for various reasons including ease of deployment, maintenance and interoperability. A cloud-based model of cybersecurity solution deployment and management provides the scalability needed for financial institutions who have to spin-up branches and allow employees flexible working conditions.
Once you have mapped your cybersecurity regulations and assets protection requirements you can establish the types of cybersecurity functionality you need. You will likely have to review a variety of cybersecurity solutions to build up the functionality required to address the complex cyber threats targeting the financial sector.
The skills gap in cybersecurity, estimated to be around 2.7 million worldwide, is affecting financial institutions as much as any sector. Also, the Covid-19 pandemic placed an additional burden on the sector. Solution evaluation, deployment and management can be outsourced to specialists. If you make this choice, ensure that you choose a solutions partner that has experience working in the financial and banking sector.
An FI is a target for cybercriminals as 74% of banks and insurers seeing a rise in cybercrime since the pandemic started. At the same time, remote working has only exacerbated this situation and to add to this many FIs have seen budget cuts in risk departments, exacerbating the problem further. Being proactive by having a robust but flexible cybersecurity strategy is an important part of building a secure organization - and must involve ongoing monitoring of the situation. Information security regulations and standards are regularly updated to reflect changes to the cybersecurity landscape and technology. An FI must respond quickly to stop a threat from becoming a security incident.
Netify will arrange either a 1 hour demo session of Gartner rated vendors, niche players and startups with walkthroughs of features and benefits or opt for our vendor briefing session to learn more about high level capability.
If you need to compare SD WAN & SASE Cybersecurity for the Financial Services sector, download our Top 10 Playbook, includes an at-a-glance guide to regulations and frameworks.
Zscaler host regular webinars, request the next available dates now. You'll learn about their value proposition and how their solution meets the needs of specific business requirements.

Complete your details below to receive the latest dates for Zscaler's up and coming webinar.
CrowdStrike host regular webinars, request the next available dates now. You'll learn about their value proposition and how their solution meets the needs of specific business requirements.

Complete your details below to receive the latest dates for CrowdStrike's up and coming webinar.
Netify assessments are free to use, answer 10 questions to begin finding your perfect SD WAN or Cybersecurity solution.
Try the beta version of our SD WAN and connectivity pricing calculator. Currently supporting Versa SD WAN and SASE Cybersecurity in our initial release.